Method, device and system for preventing reverse analysis of ELF program
A reverse analysis and procedural technology, applied in the field of information security, can solve problems such as harm, danger, and insecurity, and achieve the effect of high security, guaranteed strength, and resistance to supply chain attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
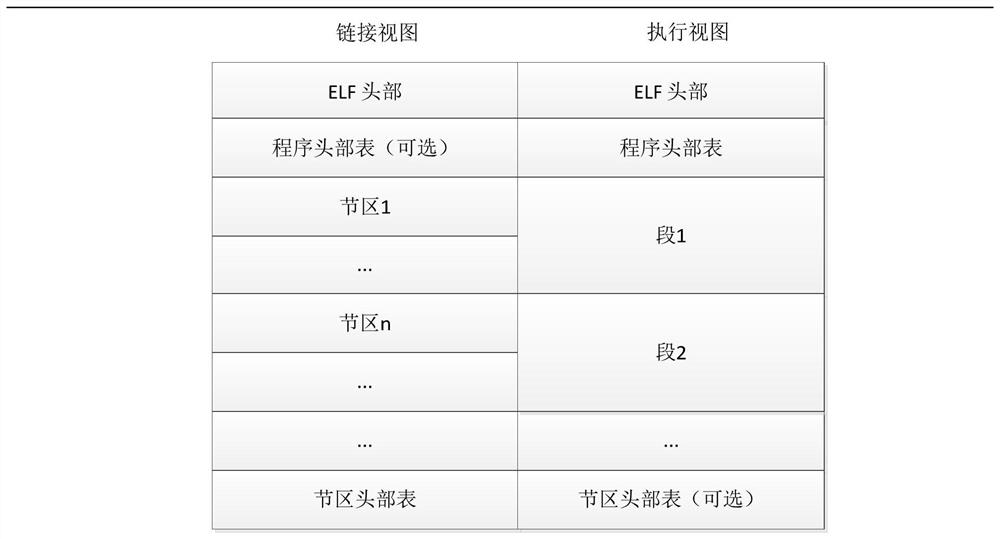
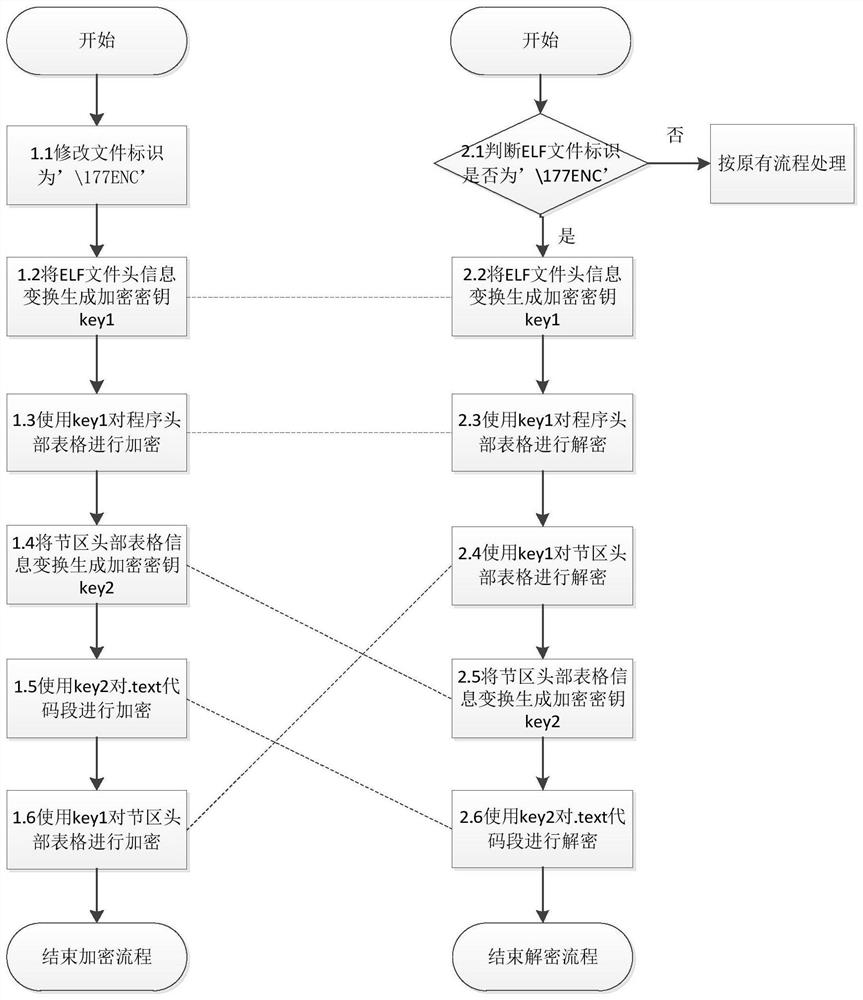
[0059] Such as image 3 As shown, a method for preventing an ELF program from being reversely analyzed is provided in the embodiment of the present invention, comprising the following steps:
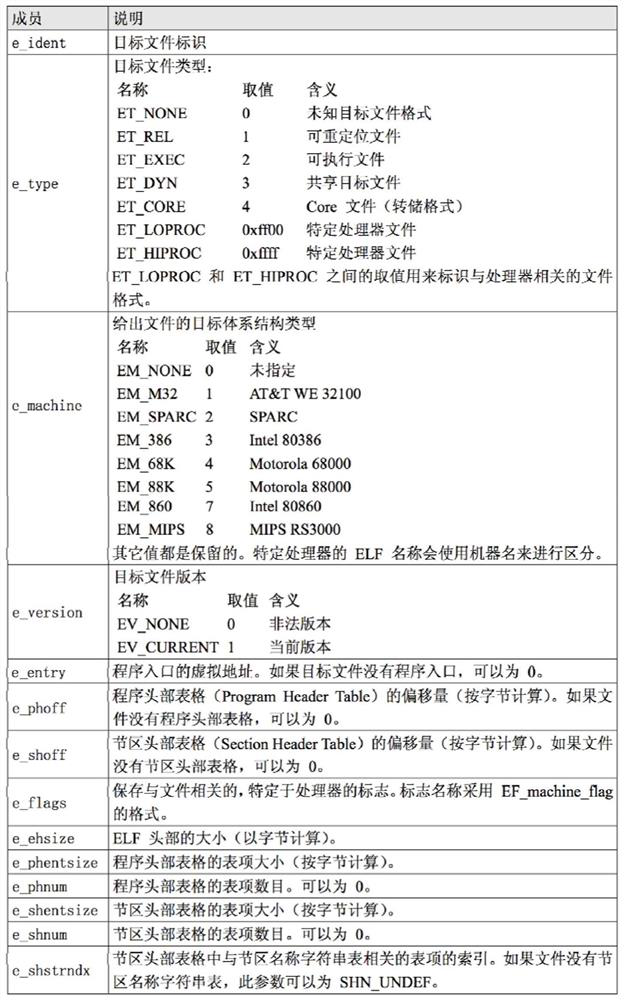
[0060] (1) After the ELF program is compiled and generated, use its own information to generate a cascade key after transformation; use the cascade key to encrypt the key header and information of the ELF program to form encrypted ELF program;
[0061] (2) When executing the encrypted ELF program, it is loaded, decrypted and executed by the kernel
[0062] Described step (1) specifically comprises the following steps:
[0063] 1.1 Modify the file identification of the ELF program, and change the original '\177ELF' to '\177ENC', so that the kernel decryption process can be performed according to this mark to distinguish and load, and it is compatible with the original normal ELF file format.
[0064] 1.2 Use the header information of the ELF program file as input, and after processing ...
Embodiment 2
[0078] An embodiment of the present invention provides a device for preventing an ELF program from being reversely analyzed, including:
[0079] The encryption module is used to generate a cascade key using its own information after transformation after the ELF program is compiled and generated; use the cascade key to encrypt the key header and information of the ELF program to form an encrypted The ELF program;
[0080] The decryption module is used to load, decrypt and execute the encrypted ELF program through the kernel when executing the encrypted ELF program.
[0081] Optionally, the method for forming the encrypted ELF program includes the following steps:
[0082] Modify the file identifier of the ELF program for differential loading processing, compatible with the original normal ELF file format;
[0083] Use the header information of the ELF program file as input, and after processing and transforming, a set of character strings are obtained as the key key1 for subs...
Embodiment 3
[0096] An embodiment of the present invention provides a system for preventing an ELF program from being reversely analyzed, including a storage medium and a processor;
[0097] The storage medium is used to store instructions;
[0098] The processor is configured to operate according to the instructions to execute the steps of the method according to any one of Embodiment 1.
[0099] Those skilled in the art should understand that the embodiments of the present application may be provided as methods, systems, or computer program products. Accordingly, the present application may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, the present application may take the form of a computer program product embodied on one or more computer-usable storage media (including but not limited to disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com