A User Management System Based on Internet Document Sharing Space
A user management and document sharing technology, applied in the field of shared documents, can solve problems such as usage habits and feedback efficiency that cannot be supervised, and achieve the effect of improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
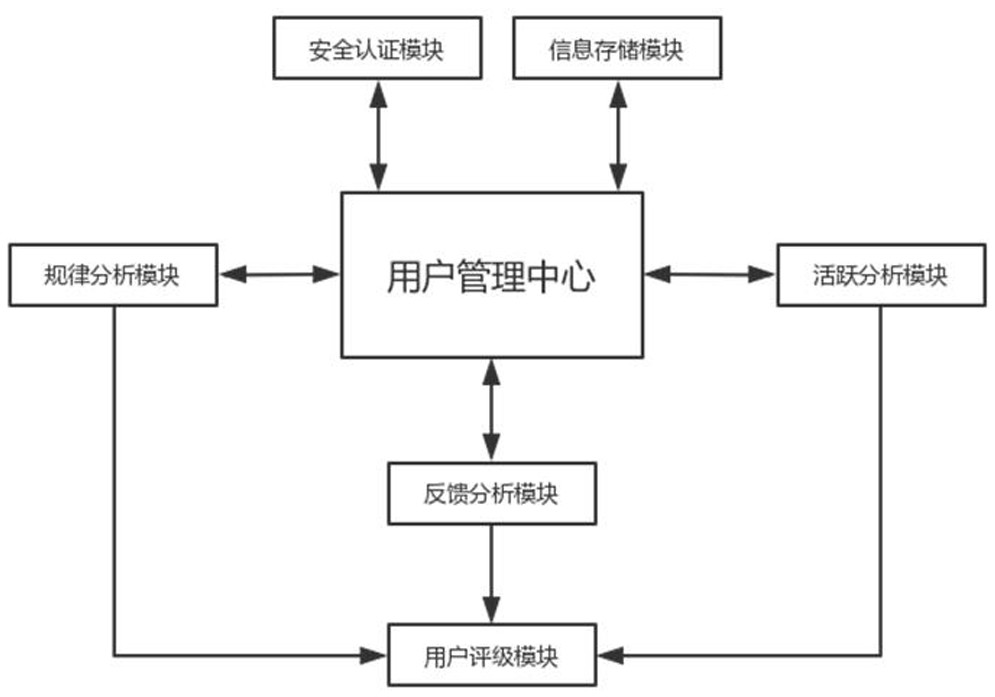
[0054] see figure 2 As shown, the activity analysis module is used to detect and analyze the activity of users logging into the shared space through the user's login data and modification data. The user's login data includes the total number of times the user logs into the shared space within L1 working days, and the number of times the user modifies Including the total number of times users modify the content of the shared space within L1 working days. L1 is a positive integer. The specific detection and analysis process of the active analysis module includes the following steps:
[0055] Step S1: Obtain the user's identity information. The user's identity information includes the user's login id, login password, and mobile phone number for registration. The user's login data and modification data are retrieved from the user management module through the user's login id. The user's Identity information can be obtained directly from the information storage module;
[0056] S...
Embodiment 2
[0082] see image 3 As shown, the security authentication module is used to perform security authentication when the user logs in. The specific security authentication process includes: obtaining the user's last login time when the user logs in, and marking the difference between the current system time and the user's last login time as Disconnection duration; compare the disconnection duration of the user with the disconnection duration threshold, mark the user whose disconnection duration is not less than the disconnection duration threshold as a verified user, obtain the identity information of the verified user, and send the verification user’s registration information to the verification user. The mobile phone number sends a verification code to verify that the user receives the verification code and enters the verification code in the operation interface to log in;
[0083] After the verification user is logged in, the security authentication module sends a replacement s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com