Access method of third-party application, terminal and computer readable storage medium
A technology of access method and access authority, which is applied in the field of communication, can solve the problems of high development cost, achieve the effect of reducing development cost and solving the problem of high development cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
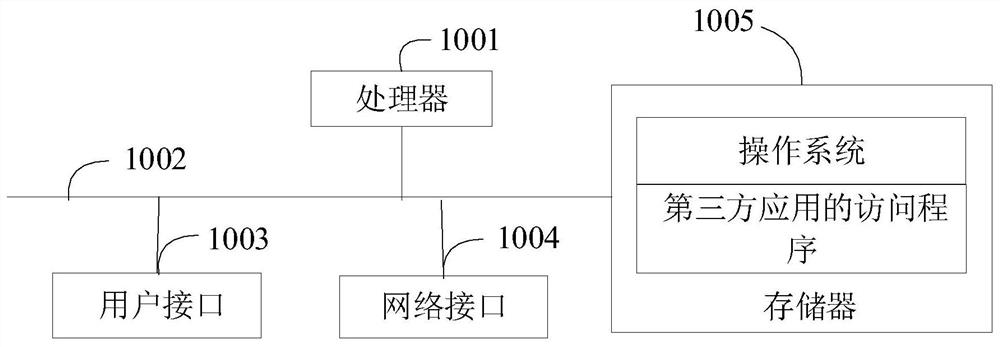
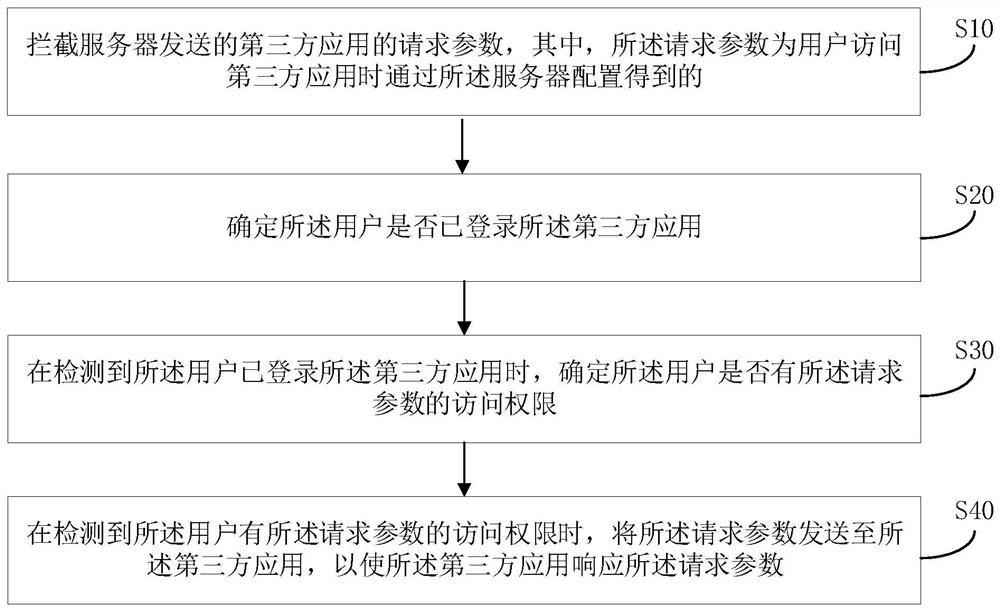
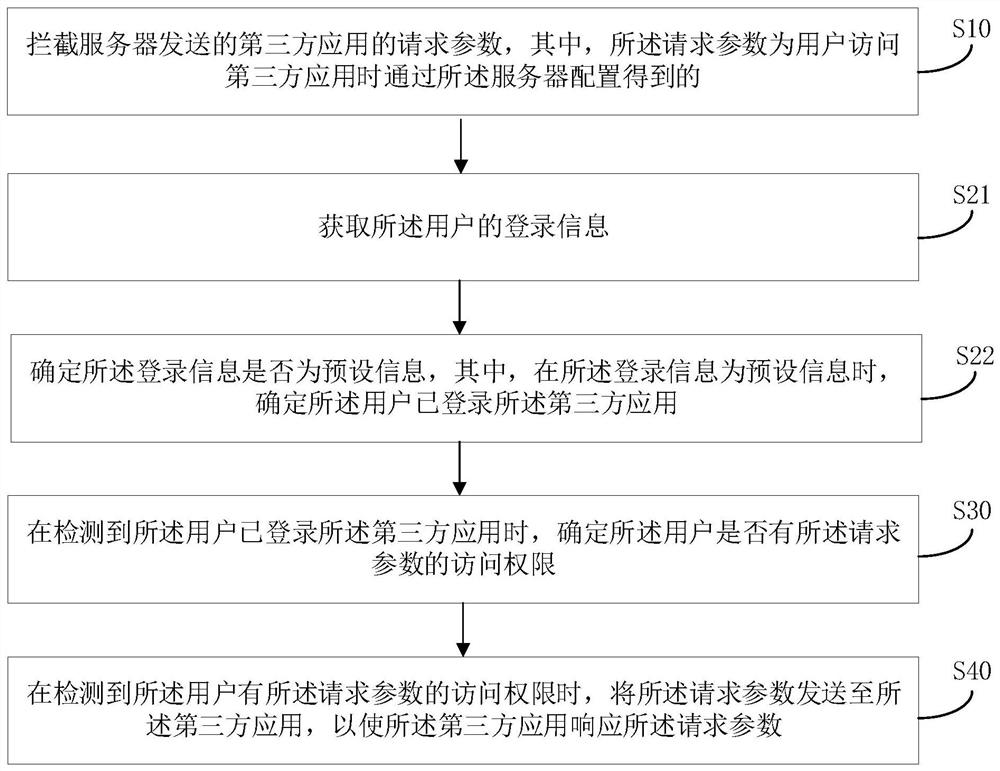
[0046] The main solution of the embodiment of the present invention is: intercept the request parameter of the third-party application sent by the server, wherein the request parameter is obtained through server configuration when the user accesses the third-party application, determine whether the user has logged into the third-party application, and detect When the user has logged into the third-party application, determine whether the user has the access right to the request parameter, and when it is detected that the user has the access right to the request parameter, send the request parameter to the third-party application, so that the third-party application responds to the request parameter. In this way, when a user accesses a third-party application, this solution does not directly access the third-party appli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com