A dns covert tunnel event automatic detection method, device and electronic equipment
A technology for DNS tunneling and automatic detection, applied in the field of network security, can solve the problems of inability to apply concealed new DNS tunnels, inability to provide sufficient, and high false positive rate, so as to improve friendliness, enhance interpretability, and reduce false positive rate. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
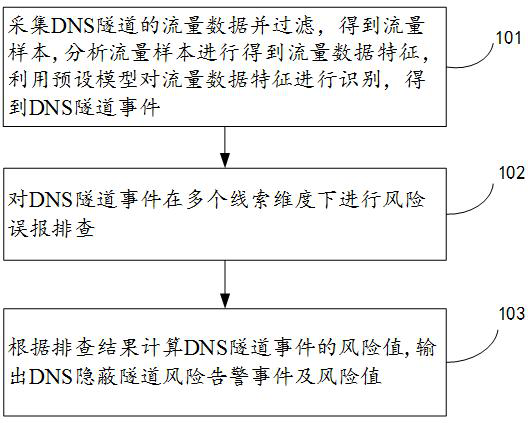
[0052] Such as figure 1 As shown, the embodiment of the present invention provides an automatic detection method for DNS covert tunnel events, which uses machine learning algorithms to detect suspected DNS covert tunnel traffic, thereby performing event clue calculation and secondary checksum of suspected DNS covert tunnel traffic Risk calculation.
[0053] The DNS covert tunnel event automatic detection method proposed by the present invention comprises:
[0054] Suspected DNS covert tunnel traffic detection step 101, collecting traffic data of the DNS tunnel and filtering redundant traffic data to obtain traffic samples; analyzing the traffic samples to extract traffic data features; using a preset model to analyze the extracted traffic data features Identify and obtain DNS tunneling events;
[0055]Event clue calculation step 102, performing risk misreporting investigation on the DNS tunneling event under multiple clue dimensions; and
[0056] The event risk calculation ...
Embodiment 2
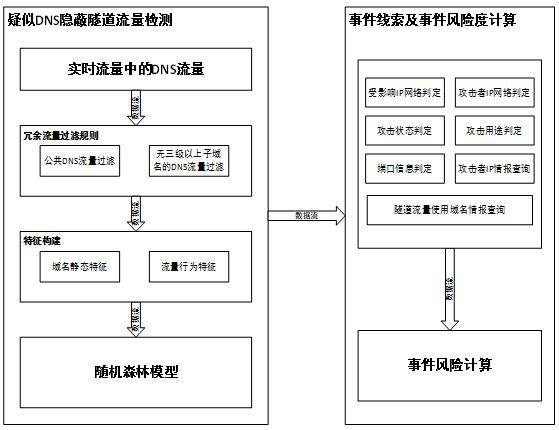
[0121] Another aspect of the present invention also includes a functional module architecture completely corresponding to the aforementioned method flow. Such as Figure 5 As shown, the embodiment of the present invention also provides a DNS covert tunnel event automatic detection device, including:
[0122] The traffic detection module 201 is configured to collect traffic data of the DNS tunnel and filter redundant traffic data to obtain traffic samples; analyze the traffic samples to extract traffic data features; use a preset model to identify the extracted traffic data features , get the DNS tunnel event;
[0123] An event clue calculation module 202, configured to perform risk misreporting investigation on the DNS tunneling event under multiple clue dimensions; and
[0124] The event risk calculation module 203 is configured to calculate the risk value of the DNS tunnel event according to the investigation result; and output the DNS covert tunnel risk event alarm and th...
Embodiment 3
[0128] The present invention also provides a memory, which stores a plurality of instructions, and the instructions are used to realize the method described in the first embodiment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com