Malicious code data imbalance processing method based on swarm intelligence algorithm and cGAN
A swarm intelligence algorithm and malicious code technology, applied to the data balance strategy in the malicious code classification problem, in the field of malicious code data imbalance processing, can solve the problems of sample data set imbalance, poor model performance, data imbalance, etc., to achieve training Simple and fast, solve the effect of data imbalance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention is explained and elaborated below in conjunction with relevant accompanying drawings:
[0041] In order to make the object, technical solution and features of the present invention clearer, the present invention will be further described in detail below in conjunction with specific implementation examples and with reference to the accompanying drawings.
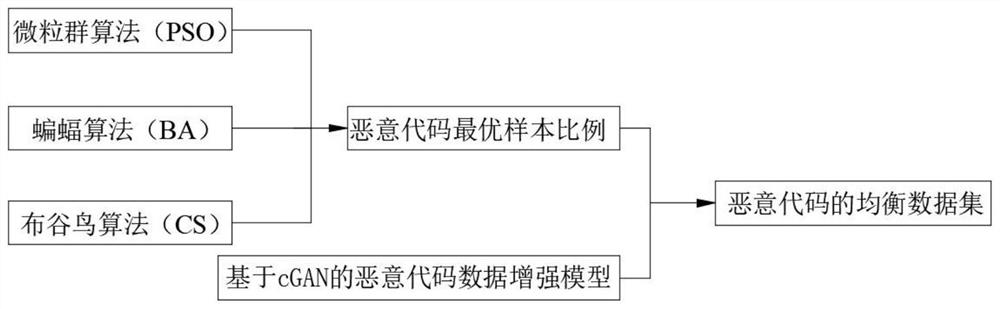
[0042] The flow chart of the construction of the malicious code balance data set is as follows: figure 1 shown, including the following steps:
[0043] Step S10, constructing a malicious code generation model;
[0044] Step S20, using the swarm intelligence algorithm to calculate the acceptable optimal initial sample ratio of the malicious code;
[0045] Step S30, generating malicious codes of each family, and constructing a relatively balanced malicious code data set.
[0046] The step S10 of constructing the malicious code generation model of the embodiment also includes the following steps: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com