An abnormal traffic detection method for encrypted network based on knowledge graph
A technology of knowledge graph and traffic detection, which is applied in the field of network abnormal traffic detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
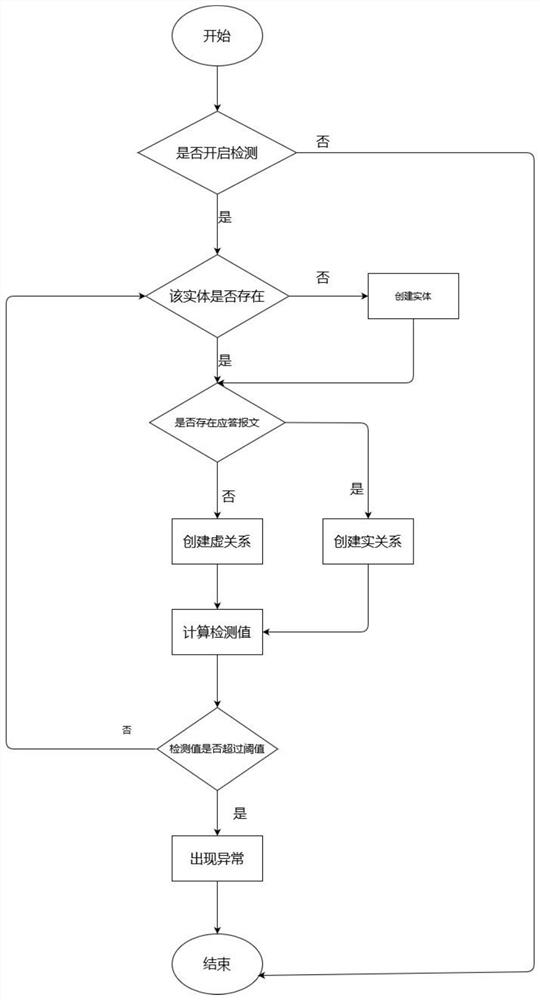
[0030] In order to better understand the contents of the present invention, an example is given here.
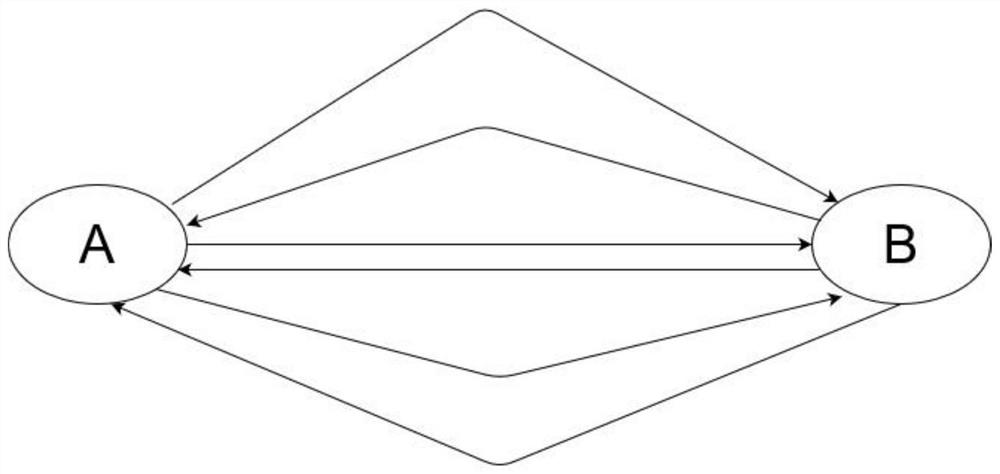
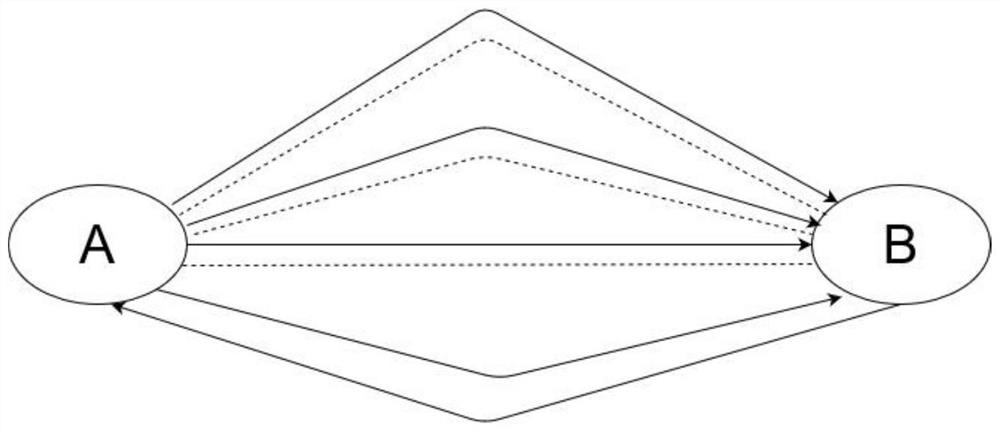
[0031] All kinds of data on the Internet are represented in the form of knowledge graphs, which can more clearly and intuitively show the behavior of each entity and the relationship between entities. A typical application scenario is that user A communicates with user B, and there is a lot of traffic between them. User A sends a request message to user B. In the data message, user A is the source IP entity, and user B is For the destination IP entity, if the traffic is normal, user B will respond to user A with a response message. One party requests and the other party responds. This connection is a group of real connections. This communication process is normal communication traffic, such as figure 1 shown. An abnormal communication flow process is that user A sends a request packet to user B, but user A does not respond to the response packet sent by user B to user A, so...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com