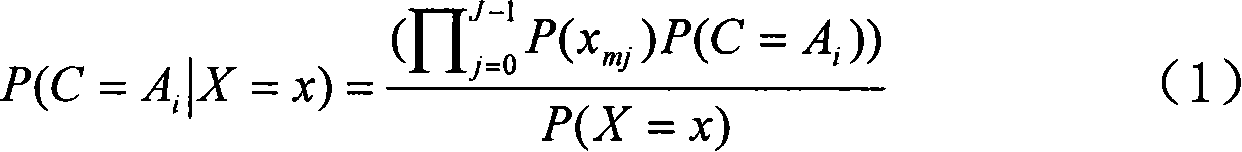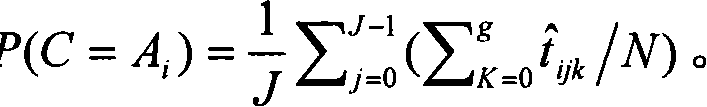Bayesian statistical model based network anomaly detection method
A network anomaly and detection method technology, applied in the field of network anomaly detection, can solve the problems of high false alarm rate, difficulty in determining the reference range of parameters, lack of flexibility, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Bayesian statistical analysis combines prior information with sample information for statistical inference. The prior information is integrated with the sample information using Bayesian formula to obtain the posterior information. The obtained posterior information can be used as a priori for a new round of calculations, and can be integrated with further obtained sample information to obtain the next posterior information. As this process continues, the posterior information is indeed getting closer and closer to the true value. In other words, the learning mechanism of the Bayesian method does exist and is effective. This learning process is actually an iterative process.
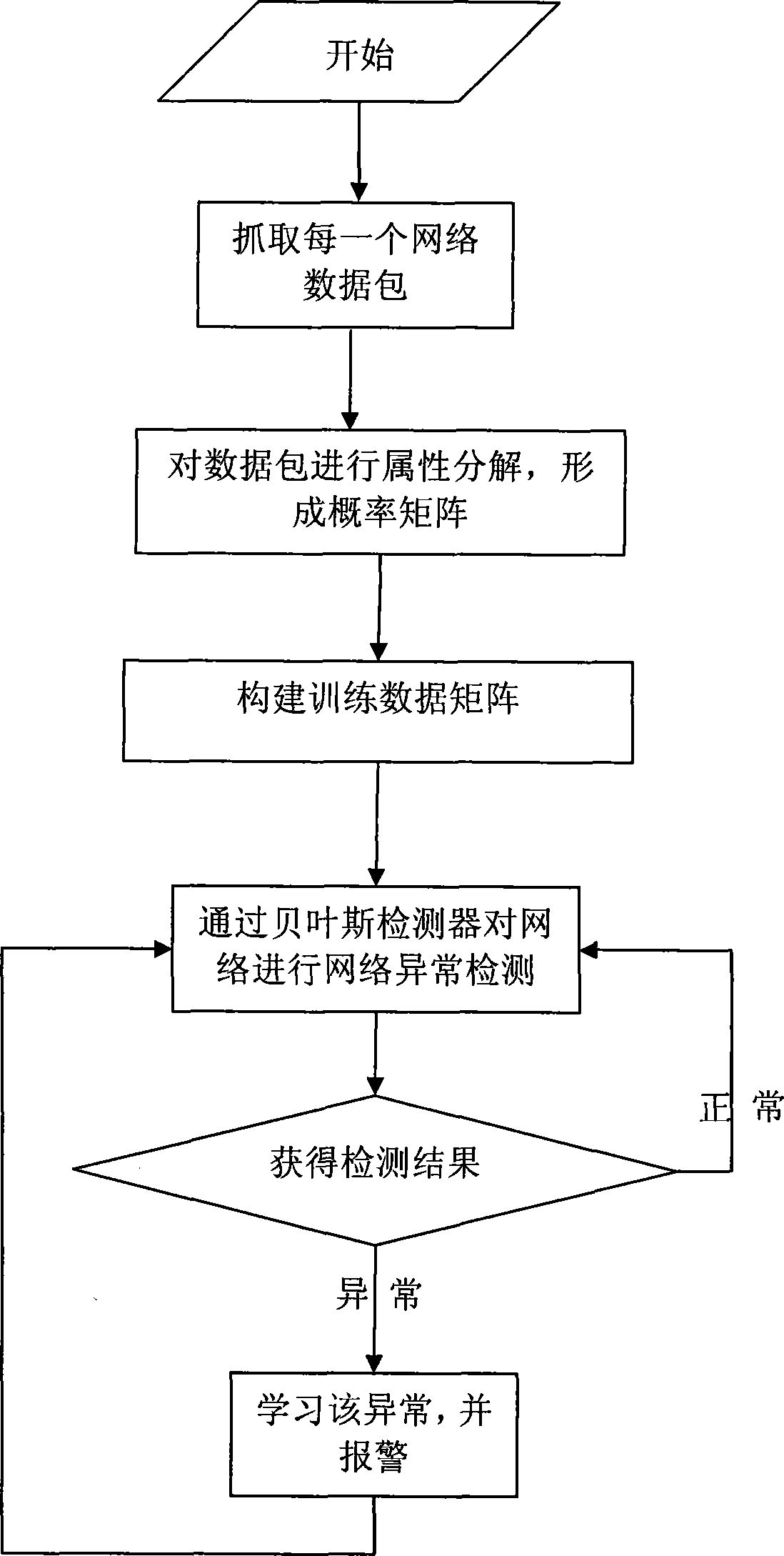
[0042] The steps of the present invention are:
[0043] (1) Capture data packets on the network in bypass listening mode:
[0044] (2) Decomposing the data packets in a fixed format,
[0045] The attribute decomposition of the data packet refers to decomposing and classifying the captured net...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com