Network security dynamic defense system and method based on big data
A dynamic defense and network security technology, applied in transmission systems, electrical components, etc., to achieve good defense effects and prolong attack time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
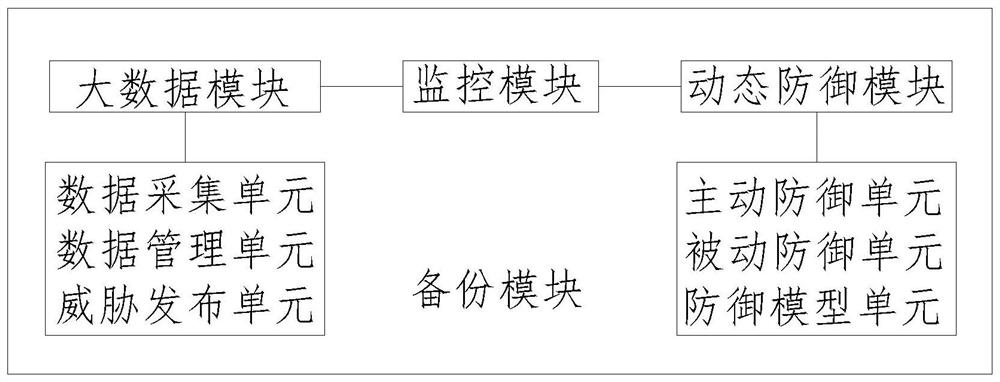
[0030] Such as figure 1 As shown, a kind of network security dynamic defense system based on big data that the present invention proposes, comprises big data module, dynamic defense module, backup module and monitoring module; Big data module and dynamic defense module are all bidirectionally connected with monitoring module; Backup module It is used for all data in the data module, dynamic defense module, and monitoring module, as well as attack behavior data; the big data module includes a data collection unit, a data management unit, and a threat release unit; the data collection unit, data management unit, and threat release unit are connected in sequence; The data acquisition unit scans the data packets circulating in each node in the network, collects and restores the data packet image files online in real time, and extracts abnormal behavior data; after the data management unit obtains the abnormal behavior data, it cleans its characteristic information, Grouping, summa...
Embodiment 2
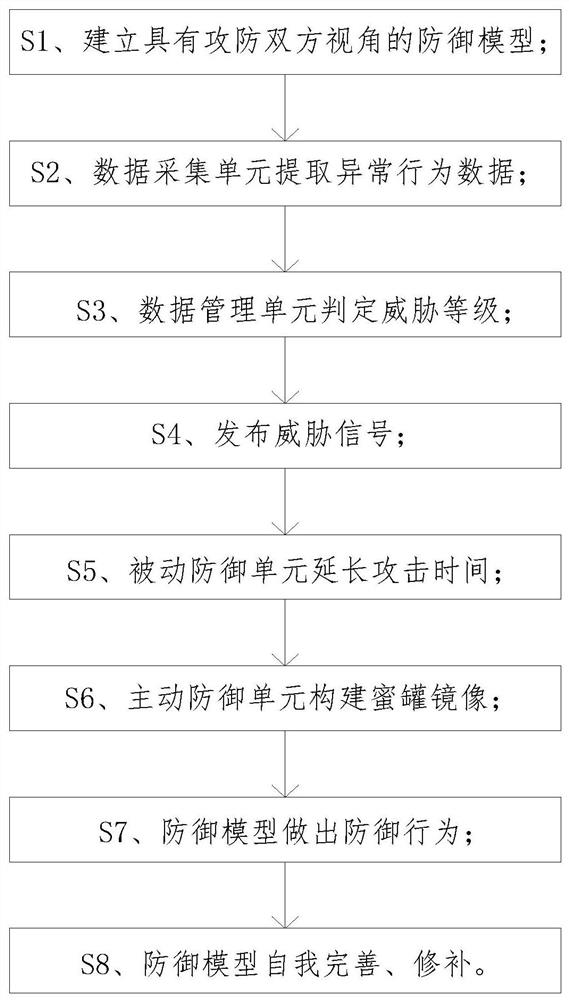
[0041] Such as figure 2 As shown, the present invention proposes a network security dynamic defense method based on big data, and the steps are as follows:
[0042] S1. Extract and model according to the attack behavior characteristics recorded in the database, and combine it with the random change state of the defense system. Each system state corresponds to a different attack surface, and the attack and defense sides predict the attack surface. Through the machine Learning and establishing a defense model with the perspective of both offense and defense;
[0043] S2. The data collection unit scans the data packets circulating in each node in the network, collects and restores the data packet image files online in real time, and extracts abnormal behavior data;
[0044] S3. After the data management unit obtains the abnormal behavior data, it cleans, groups, and summarizes its characteristic information, and conducts intelligent analysis in combination with the abnormal beh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com