Hierarchical security multi-party calculation method and device based on Chinese remainder theorem
A technology of secure multi-party computation and Chinese remainder theorem, which is applied in the field of information security and can solve problems such as inability to coordinate processing and leaking secrets.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
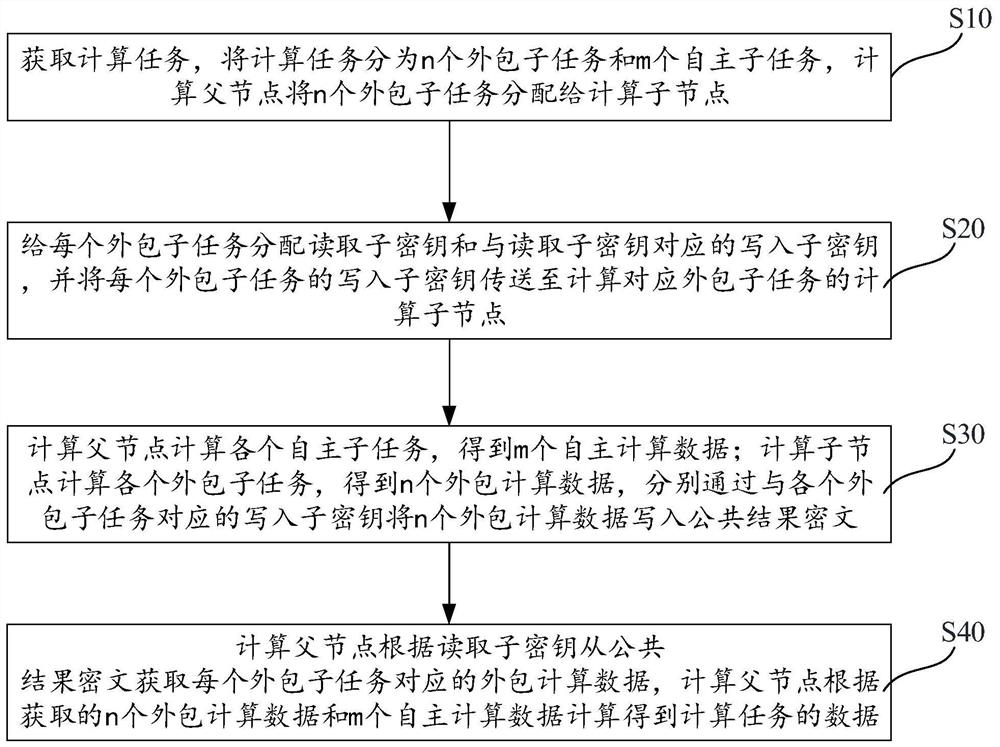
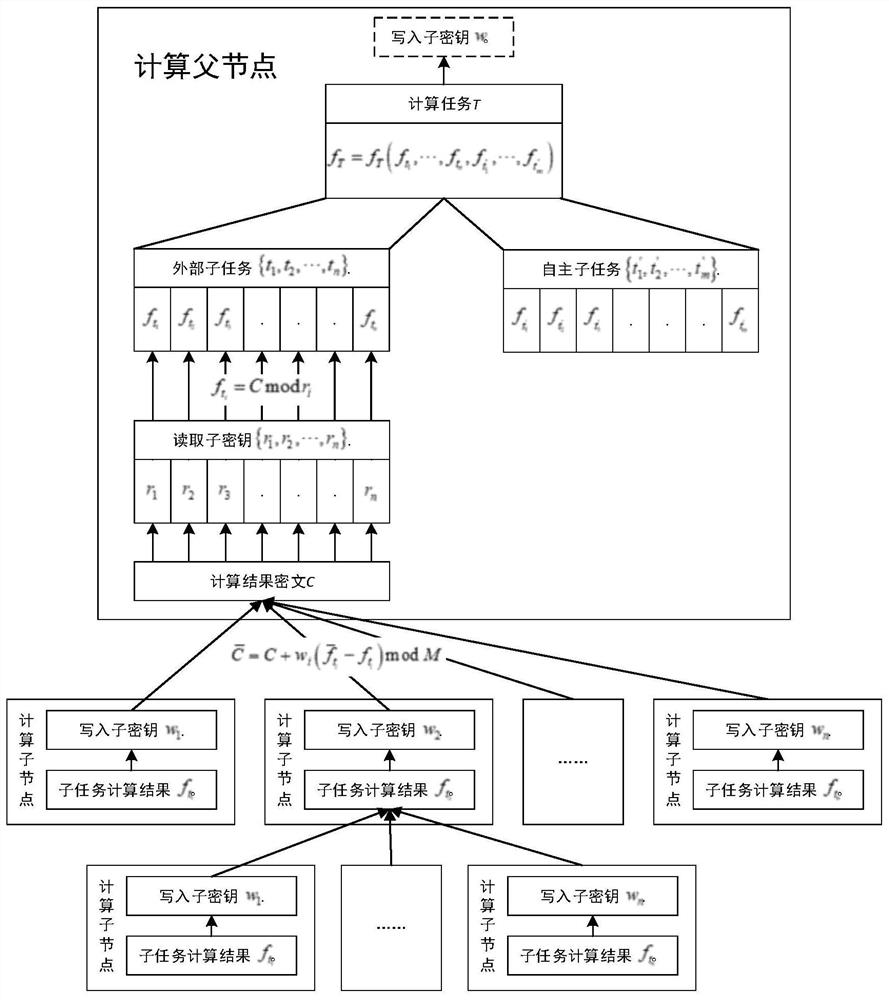
[0042] figure 1 It is a flow chart of the steps of the hierarchical secure multi-party computing method based on the Chinese remainder theorem described in the embodiment of the present invention, figure 2 It is a framework diagram of the hierarchical secure multi-party computation method based on the Chinese remainder theorem described in the embodiment of the present invention.
[0043] like figure 1 and figure 2 As shown, the embodiment of the present invention provides a hierarchical secure multi-party computing method based on the Chinese remainder theorem, including the following steps:
[0044] S10. Acquire computing tasks, divide the computing tasks into n outsourced subtasks and m autonomous subtasks, and the computing parent node assigns n outsourced subtasks to computing child nodes;
[0045] S20. Assign a read subkey and a write subkey corresponding to the read subkey to each outsourced subtask, and transmit the write subkey of each outsourced subtask to the c...
Embodiment 2
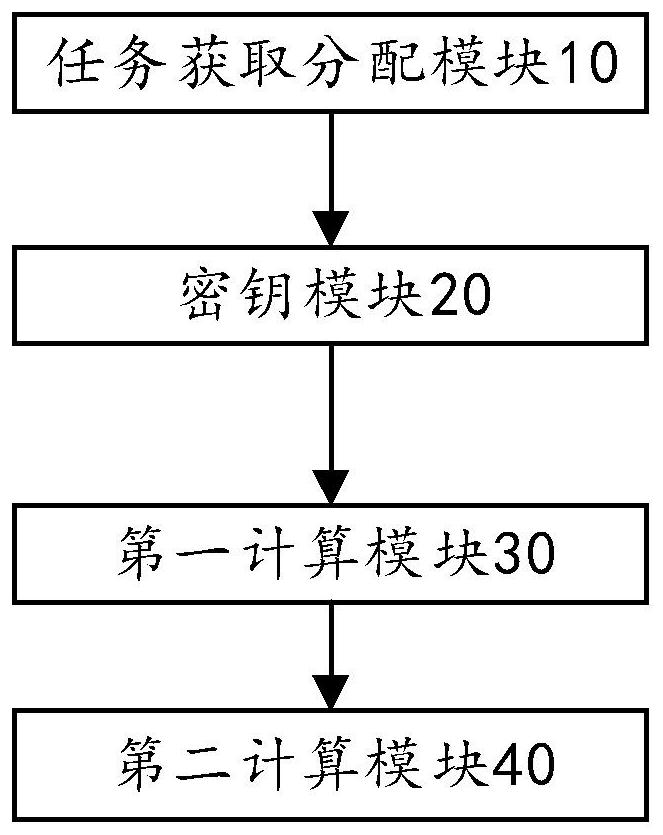
[0098] image 3 It is a frame diagram of a hierarchical secure multi-party computing device based on the Chinese remainder theorem described in the embodiment of the present invention.
[0099] like image 3 As shown, the embodiment of the present invention also provides a hierarchical secure multi-party computing device based on the Chinese remainder theorem, including a task acquisition and distribution module 10, a key module 20, a first computing module 30 and a second computing module 40;
[0100] The task acquisition and distribution module 10 is used to acquire computing tasks, divide the computing tasks into n outsourced subtasks and m autonomous subtasks, and calculate the parent node to assign n outsourced subtasks to the computing child nodes;
[0101] The key module 20 is configured to assign a read subkey and a write subkey corresponding to the read subkey to each outsourced subtask, and transmit the write subkey of each outsourced subtask to the computing Compu...
Embodiment 3
[0106] An embodiment of the present invention provides a computer-readable storage medium. The computer storage medium is used to store computer instructions. When running on a computer, the computer executes the above-mentioned hierarchical secure multi-party computing method based on the Chinese remainder theorem.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com