Safety protection intelligent identification method in 5T operation and maintenance
A technology of security protection and intelligent identification, applied in biometric identification, neural learning methods, character and pattern recognition, etc., can solve problems such as threats to safe production, limited energy, and easy fatigue and distraction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
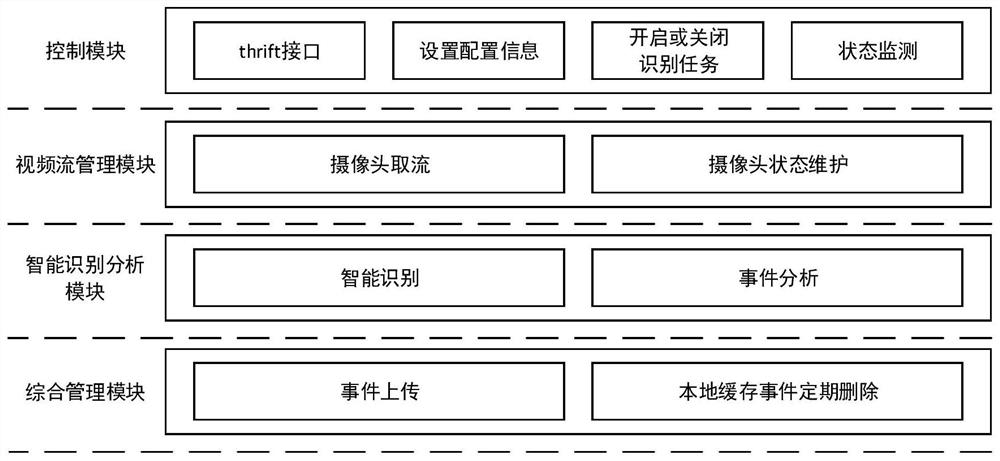
[0121] The structure diagram of the function module of the protection identification unit is as follows: figure 1 shown, including:
[0122] 1. Control module
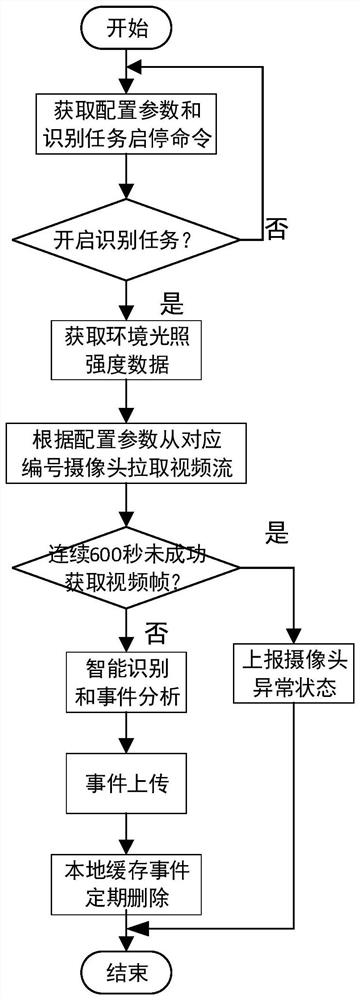
[0123] The 5T detection host computer can set configuration information through the thrift interface of the control module, enable and disable identification tasks, and monitor the operating status of the system (realizing remote operation and real-time monitoring of the status of the system).
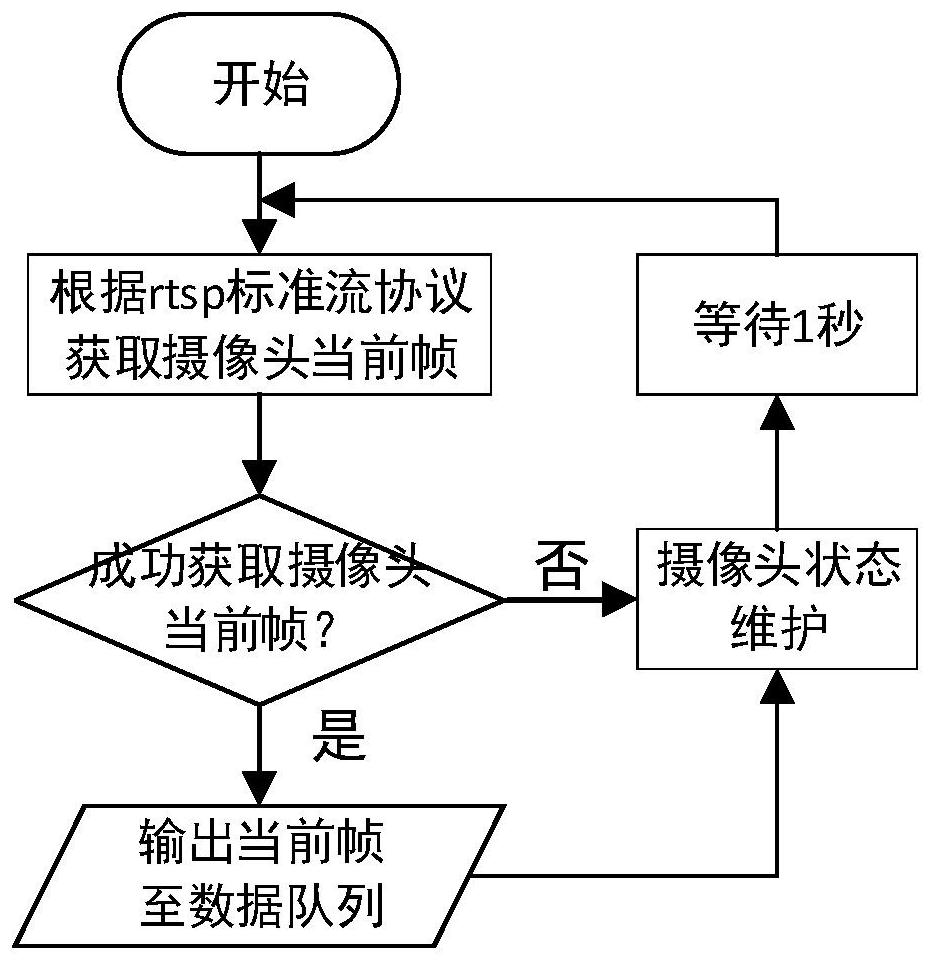
[0124] 2. Video stream management module
[0125] The video stream management module grabs the video stream from the camera and maintains the camera status according to the configuration information and commands issued by the control module.
[0126] 3. Intelligent identification and analysis module
[0127] The intelligent identification and analysis module is mainly responsible for the intelligent identification of operators, safety helmets, and protective clothing; event analysis of safety helmets and protective clothing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com