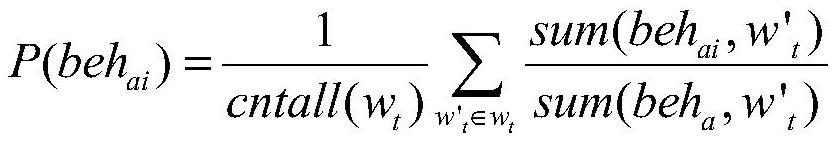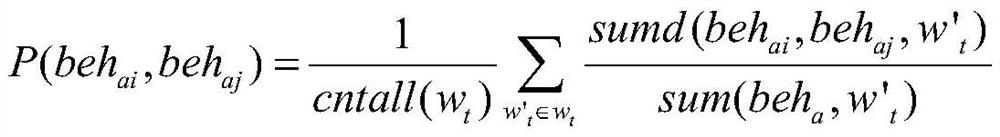Mining method for discovering dependency relationship between threat behaviors, terminal and storage medium
A technology of dependencies and storage media, which is applied in the mining method for discovering dependencies between threat behaviors, terminals and storage media, can solve problems such as computer loss, and achieve the effect of improving incident response capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention relates to a mining method for discovering dependencies between threat behaviors, and the described features, structures or characteristics can be combined in any suitable manner in one or more embodiments. In the following description, numerous specific details are provided to ensure a thorough understanding of embodiments of the invention. However, those skilled in the art will realize that the present invention does not specify an implementation method for some details of the technical solution, and the skilled person may use other known methods, devices, steps, etc. to implement it. Therefore, the following description does not illustrate or describe well-known methods, apparatuses, implementations or operations in detail to avoid obscuring aspects of the present invention.
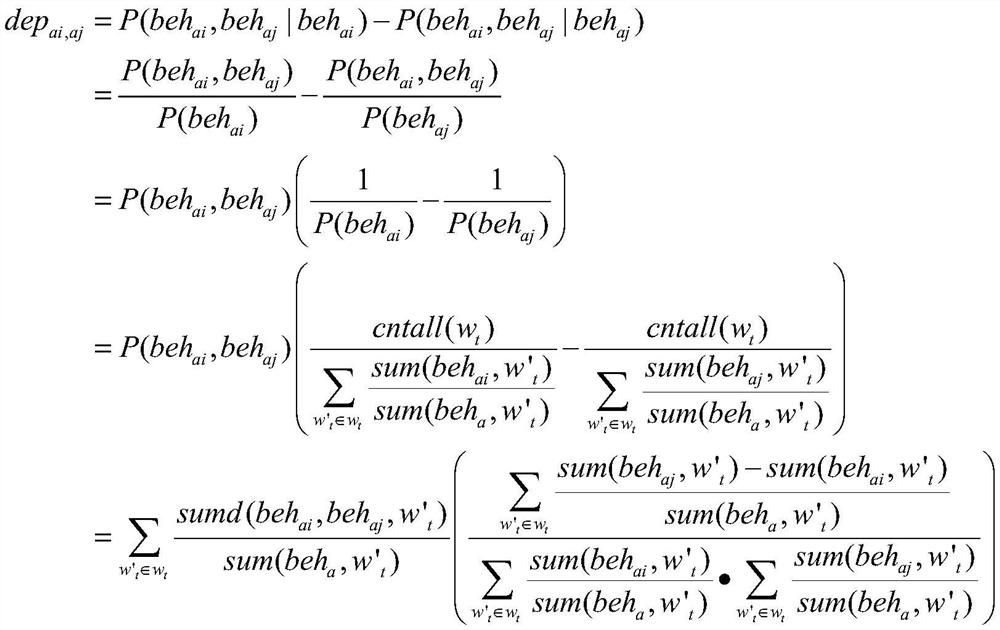
[0046] The invention provides a mining method for discovering the dependency between threat behaviors, and the purpose of the invention is to mine the dependency between beh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com