Multi-application single sign-on method and device, equipment and storage medium
A single sign-on and multi-application technology, applied in the computer field, can solve the problems of weak framework compatibility, difficulty in compatibility with single sign-on business, and weak expansion ability of framework business, so as to improve flexibility and compatibility and reduce modification , Improve the effect of user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
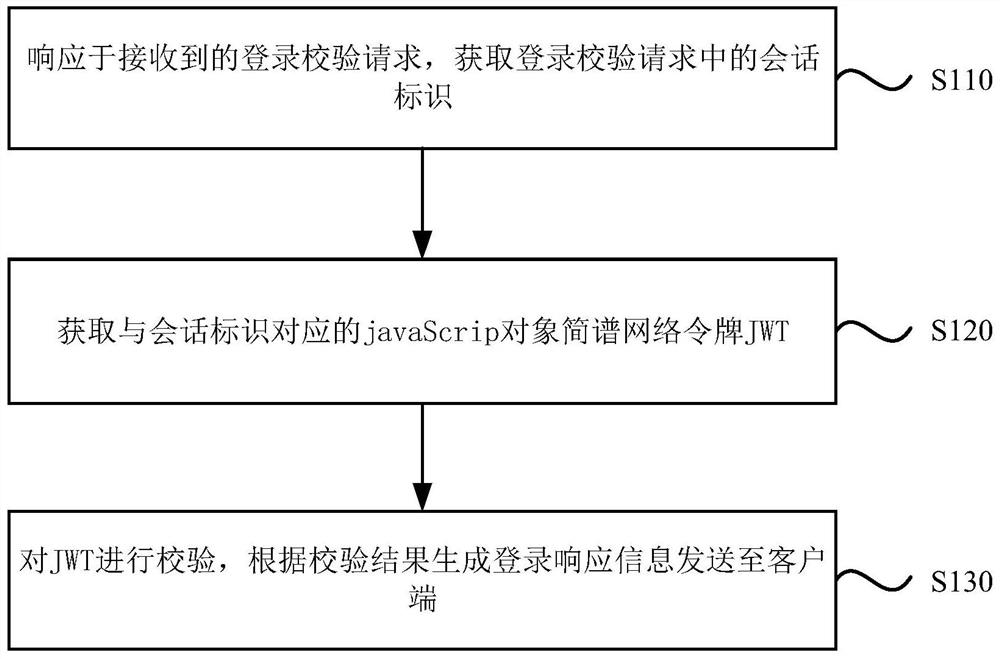
[0029] figure 1 It is a flowchart of a multi-application single sign-on method provided by Embodiment 1 of the present invention, and this embodiment is applicable to the situation of implementing multi-application single sign-on. The method can be executed by a multi-application single sign-on device, and the device can be implemented by hardware and / or software, for example, the multi-application single sign-on device can be configured in a computer device. Such as figure 1 As shown, the method specifically includes the following steps:
[0030] Step S110, in response to the received login verification request, acquire the session identifier in the login verification request.
[0031] In this embodiment, the login verification request is initiated by the client and is used to make the server perform a single sign-on login verification request. Optionally, the login verification request includes the client ID of the client that initiates the login verification request, the...
Embodiment 2
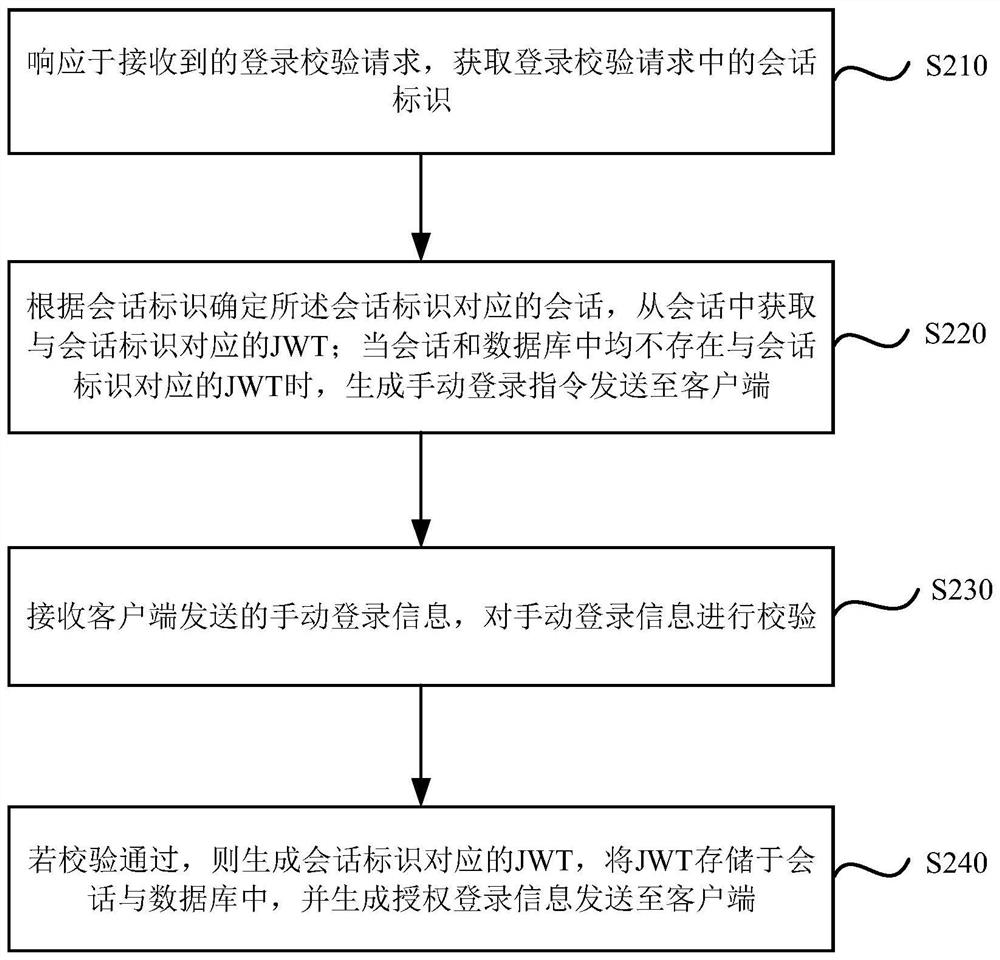
[0046] figure 2 It is a flow chart of a multi-application single sign-on method provided by the embodiment of the present invention. On the basis of the above-mentioned solution, this embodiment specifies the operation when the JWT corresponding to the session identifier is not obtained. Such as figure 2 As shown, the method specifically includes the following steps:
[0047] Step S210, in response to the received login verification request, acquire the session ID in the login verification request.
[0048] Step S220: Determine the session corresponding to the session ID according to the session ID, obtain the JWT corresponding to the session ID from the session, and generate a manual login instruction and send it to the client when there is no JWT corresponding to the session ID in the session or the database.
[0049] In this embodiment, when there is no JWT corresponding to the session identifier in either the session or the database, it means that neither the session n...
Embodiment 3
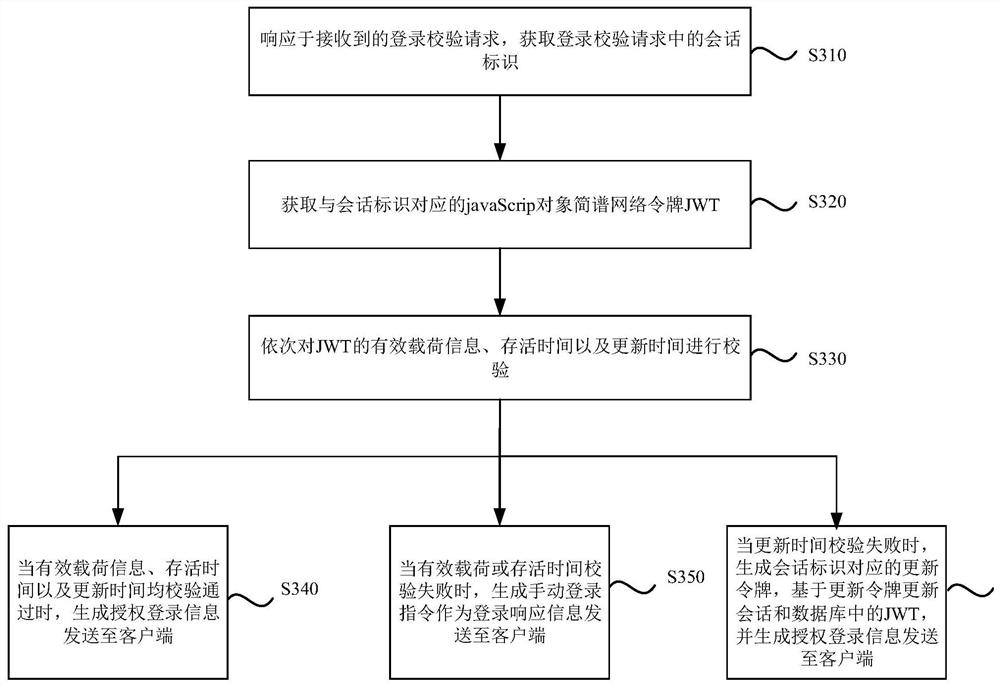
[0058] image 3 It is a flow chart of a multi-application single sign-on method provided by an embodiment of the present invention, and this embodiment is further optimized on the basis of the foregoing embodiments. Such as image 3 As shown, the method specifically includes the following steps:
[0059] S310. In response to the received login verification request, acquire the session identifier in the login verification request.
[0060] S320. Acquire a javaScrip object numbered notation network token JWT corresponding to the session identifier.
[0061] S330. Verifying the payload information, survival time, and update time of the JWT in sequence.
[0062] In this embodiment, after the JWT is obtained, the JWT is parsed to obtain the payload information, survival time and update time of the JWT, and the payload information, survival time and renewal time are verified in sequence. Wherein, the payload information is the subject content part of the JWT, which is a JSON obj...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com