Terminal fraud phone recognition method based on call text word vector
A technology of fraudulent phone calls and word vectors, applied in the information field, can solve the problems of inability to detect fraudulent phone calls in real time, victims being deceived, etc., so as to improve the accuracy and recall rate of recognition, solve semantic deviation, and ensure the effect of user privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
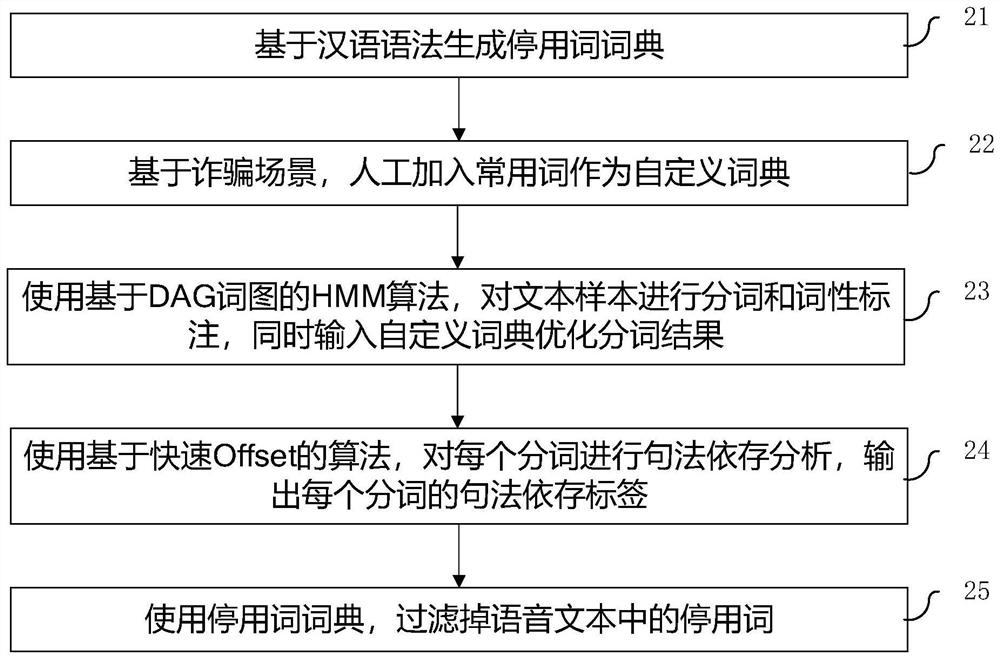
[0016] like figure 1 As shown in the present invention, a method for identifying fraudulent phone calls based on a call text word vector includes:
[0017] Step 1. The user marks the incoming calls in the mobile terminal App. For the incoming calls marked by the user as fraudulent, the call is extracted and converted into text after the user authorizes and agrees, and then the converted text is handed over to the user for viewing and desensitization, and finally After the user authorizes and agrees, upload the user-viewed and desensitized text to the server and save it as a text sample. Desensitization means removing sensitive information related to personal identity, such as ID number, name, mobile phone number, etc.;
[0018] Step 2. Perform word segmentation a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com