Causal knowledge-based power information network attack scene reconstruction method and system
A network attack and power information technology, applied in transmission systems, electrical components, electrical digital data processing, etc., can solve the problems of alarm division and automatic identification of false alarms, complex and difficult causal knowledge, and relying on expert knowledge, etc. Carry out targeted, improve defense measures, and enrich the effect of scene information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
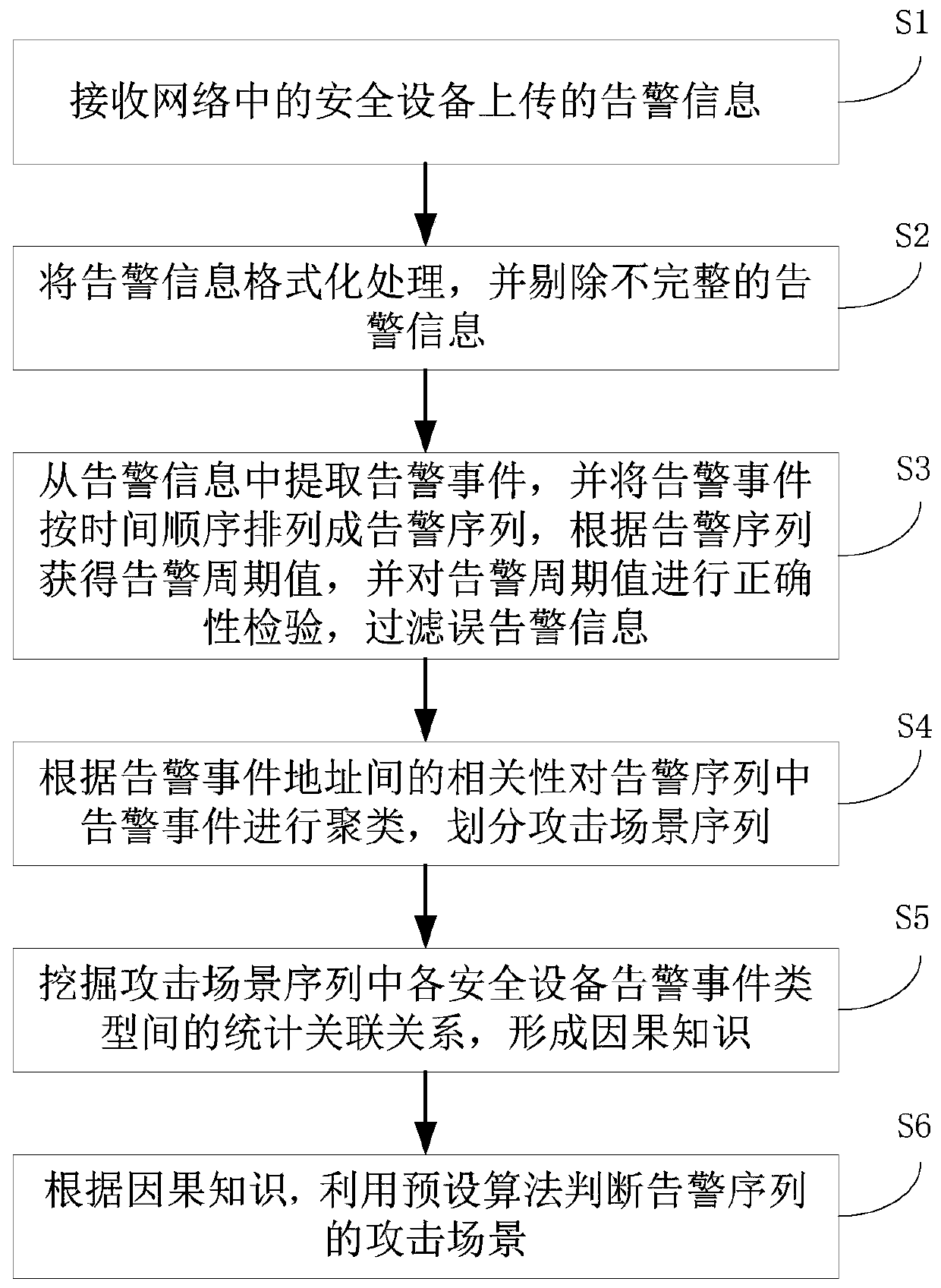
[0044] The embodiment of the present invention provides a power information network attack scenario reconstruction method based on causal knowledge, such as figure 1 shown, including the following steps:
[0045] Step S1: Receive alarm information uploaded by security devices in the network. In the embodiment of the present invention, when a network attacker attacks the target network, the attacker's attack action will trigger security devices in the target network, such as IDS (Intrusion Detection System), Firewall, etc. to generate alarm information (such as log alarm) ; After the security device generates the alarm information, it uploads the generated alarm information to the server.
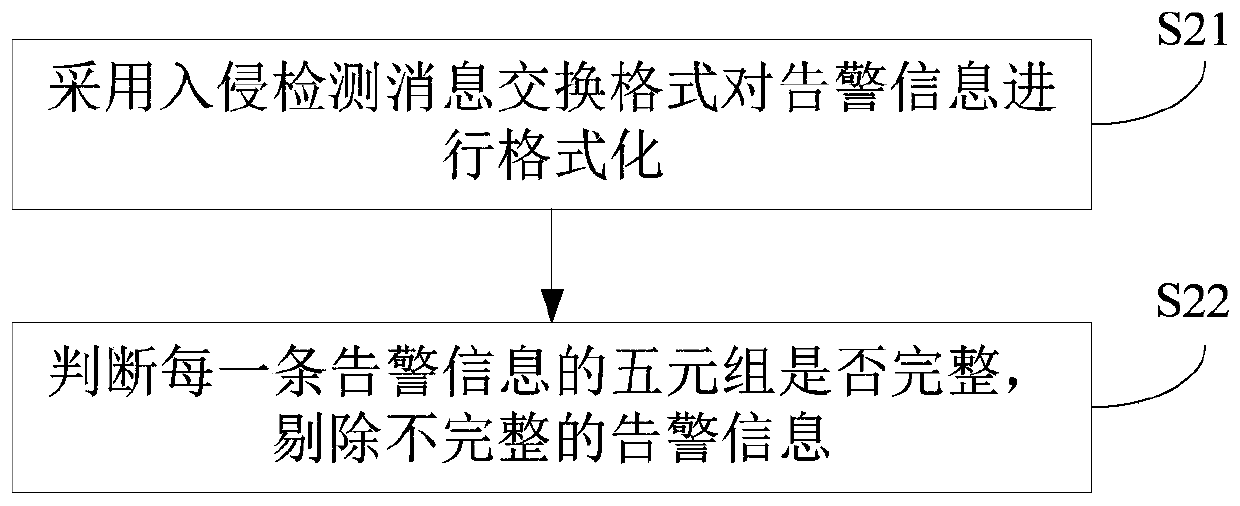
[0046] Step S2: format the alarm information, and eliminate incomplete alarm information. In the embodiment of the present invention, the alarm information is preprocessed. First, IDMEF (The Intrusion Detection Message Exchange Format) is used to format the alarm information; secondly, the...
Embodiment 2
[0089] The embodiment of the present invention provides a power information network attack scenario reconstruction system based on causal knowledge, such as Figure 8 shown, including:
[0090] The receiving module 1 is configured to receive alarm information uploaded by security devices in the network. This module executes the method described in step S1 in Embodiment 1, which will not be repeated here.
[0091] The preprocessing module 2 is used to format the alarm information and remove incomplete alarm information. This module executes the method described in step S2 in Embodiment 1, which will not be repeated here.
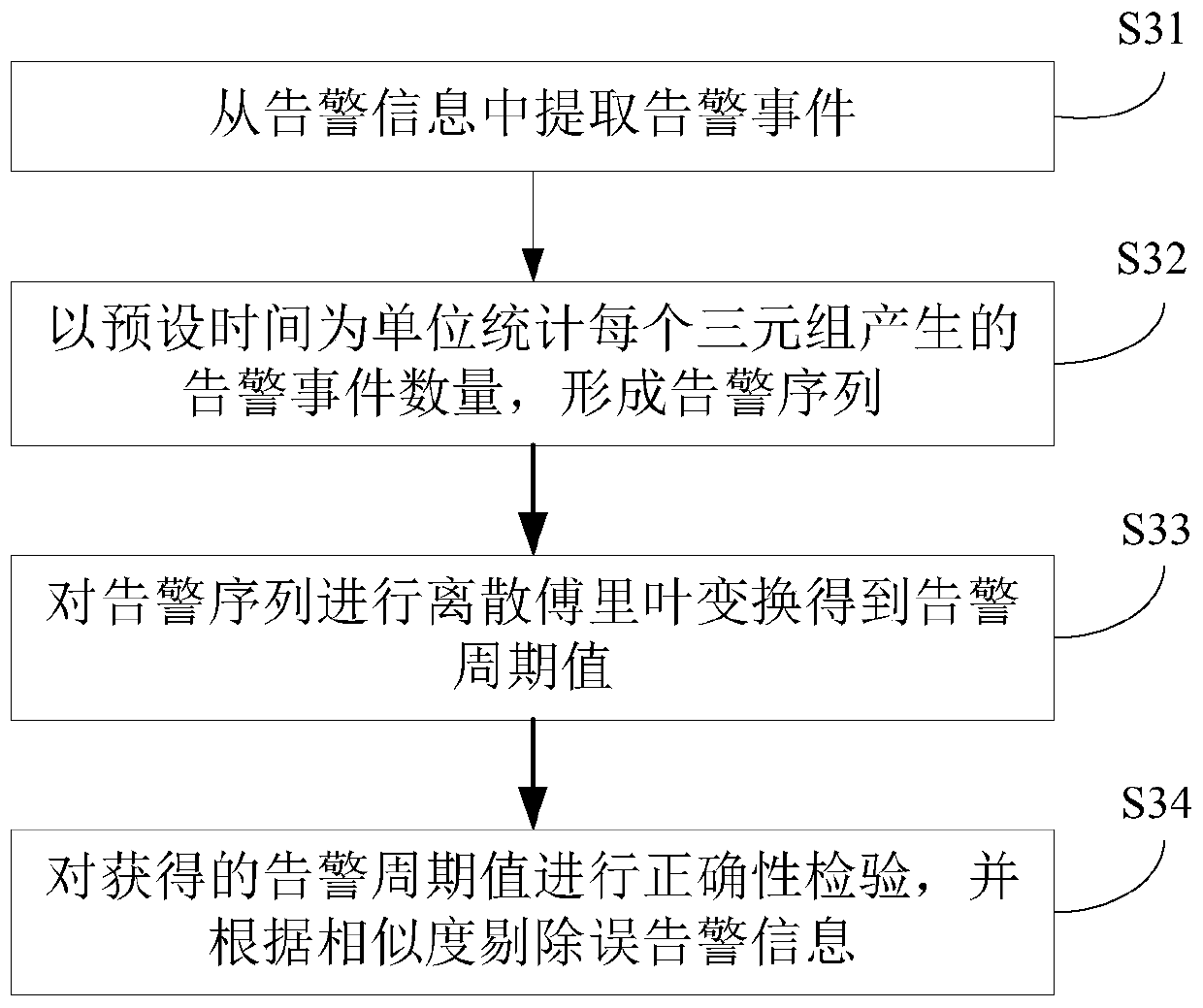
[0092] The filtering module 3 is used to extract alarm events from the alarm information, arrange the alarm events into an alarm sequence in chronological order, obtain the alarm cycle value according to the alarm sequence, and check the correctness of the alarm cycle value to filter false alarm information. This module executes the method described in ste...
Embodiment 3
[0098] An embodiment of the present invention provides a computer device, such as Figure 9 As shown, the device may include a processor 71 and a memory 72, wherein the processor 71 and the memory 72 may be connected via a bus or in other ways, Figure 9 Take connection via bus as an example.
[0099] The processor 71 may be a central processing unit (Central Processing Unit, CPU). Processor 71 can also be other general processors, digital signal processor (Digital Signal Processor, DSP), application specific integrated circuit (Application Specific Integrated Circuit, ASIC), field programmable gate array (Field-Programmable Gate Array, FPGA) or Other chips such as programmable logic devices, discrete gate or transistor logic devices, discrete hardware components, or combinations of the above-mentioned types of chips.
[0100] As a non-transitory computer-readable storage medium, the memory 72 can be used to store non-transitory software programs, non-transitory computer-exe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com