Post-penetration method of automatic penetration test system based on AI
A penetration testing and automatic technology, applied in neural learning methods, biological neural network models, platform integrity maintenance, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
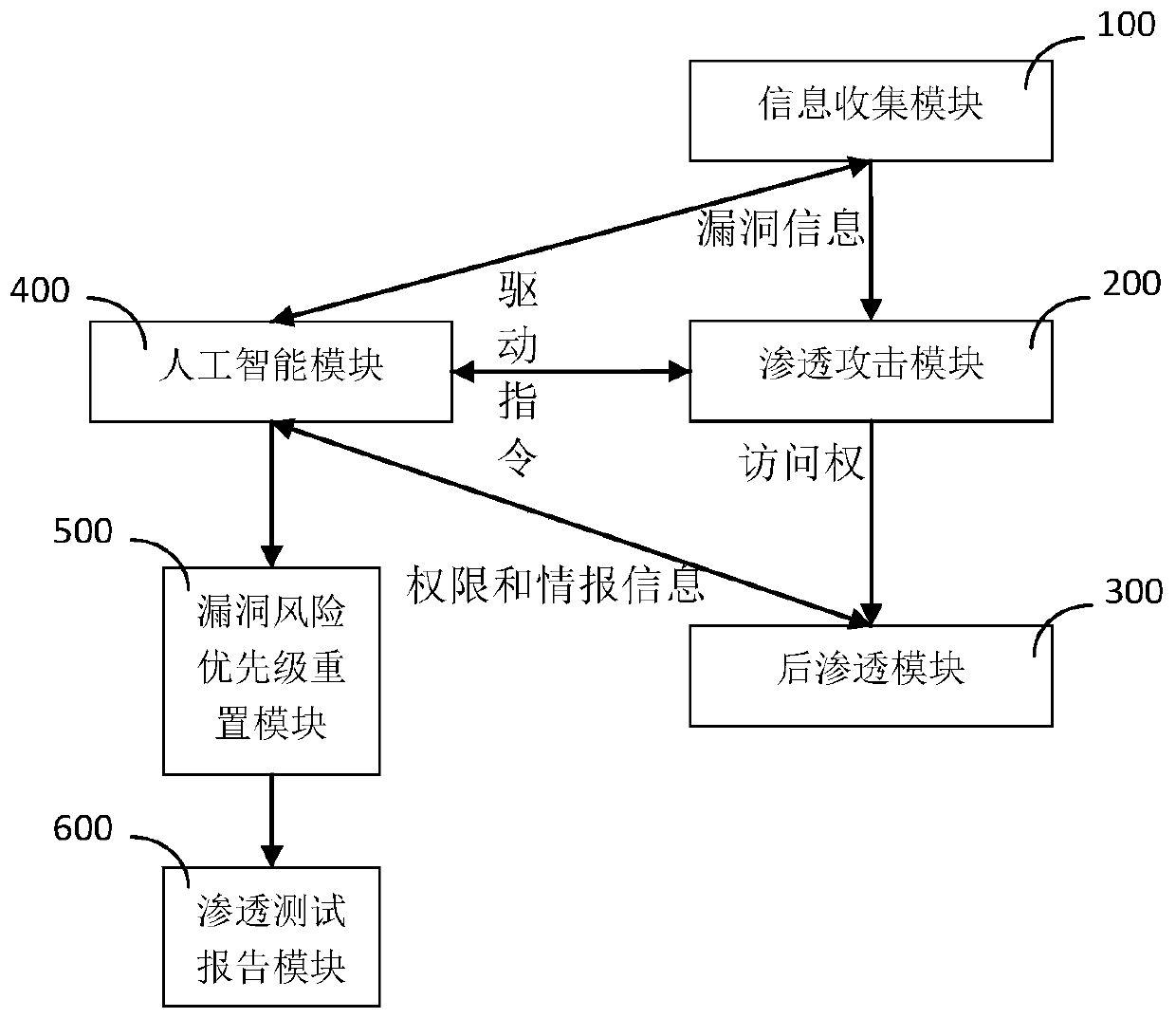
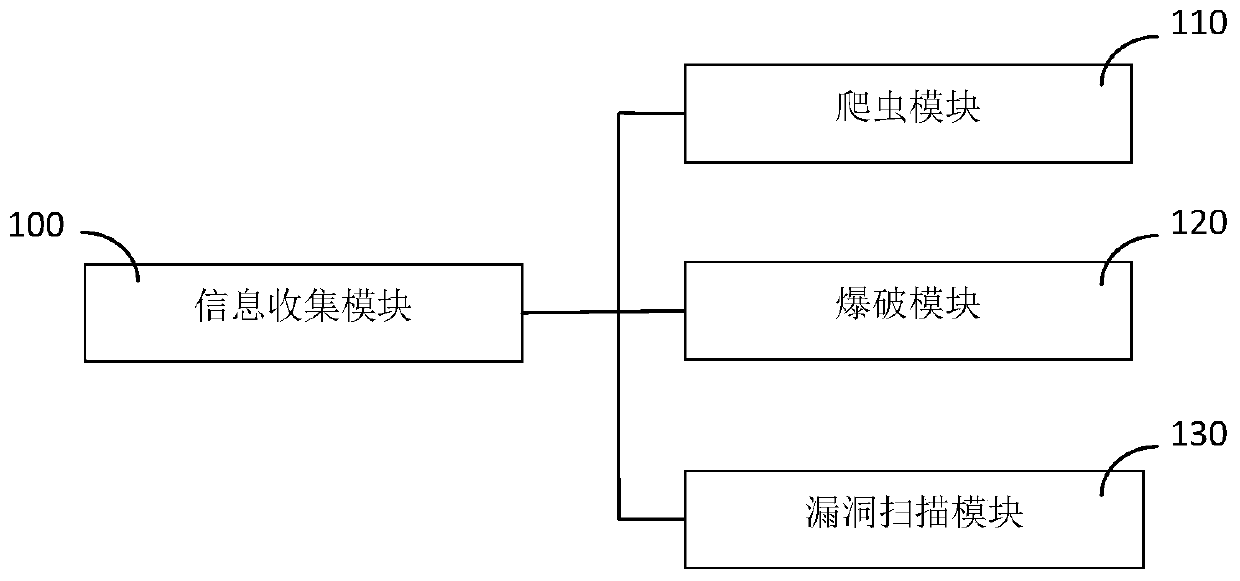
[0090] Such as figure 1 As shown, the present embodiment includes the following steps during use:
[0091] S1. After the post-infiltration module 300 recognizes that the current shell has normal authority, it automatically escalates the authority through exploiting the vulnerability;
[0092] S2, the post-infiltration module 300 automatically extracts the account password data from the memory;
[0093] S3. The post-infiltration module 300 automatically traverses the file system, and the special intelligent module 430 identifies sensitive data files according to the content of the file system, extracts and generates sensitive information;
[0094] S4. The decision-making brain module 420 judges whether an iterative attack is required according to the sensitive information, and returns to the iterative attack judgment if it is judged to be yes, and proceeds to step S5 if it is judged to be otherwise;
[0095] S5. The decision-making brain module 420 judges whether to perform a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com