Penetration attack method of AI-based automatic penetration test system
A penetration testing and vulnerability technology, applied in the field of network data security, to achieve the effect of stable service level, reduced risk exposure window, and fewer blind spots of knowledge
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
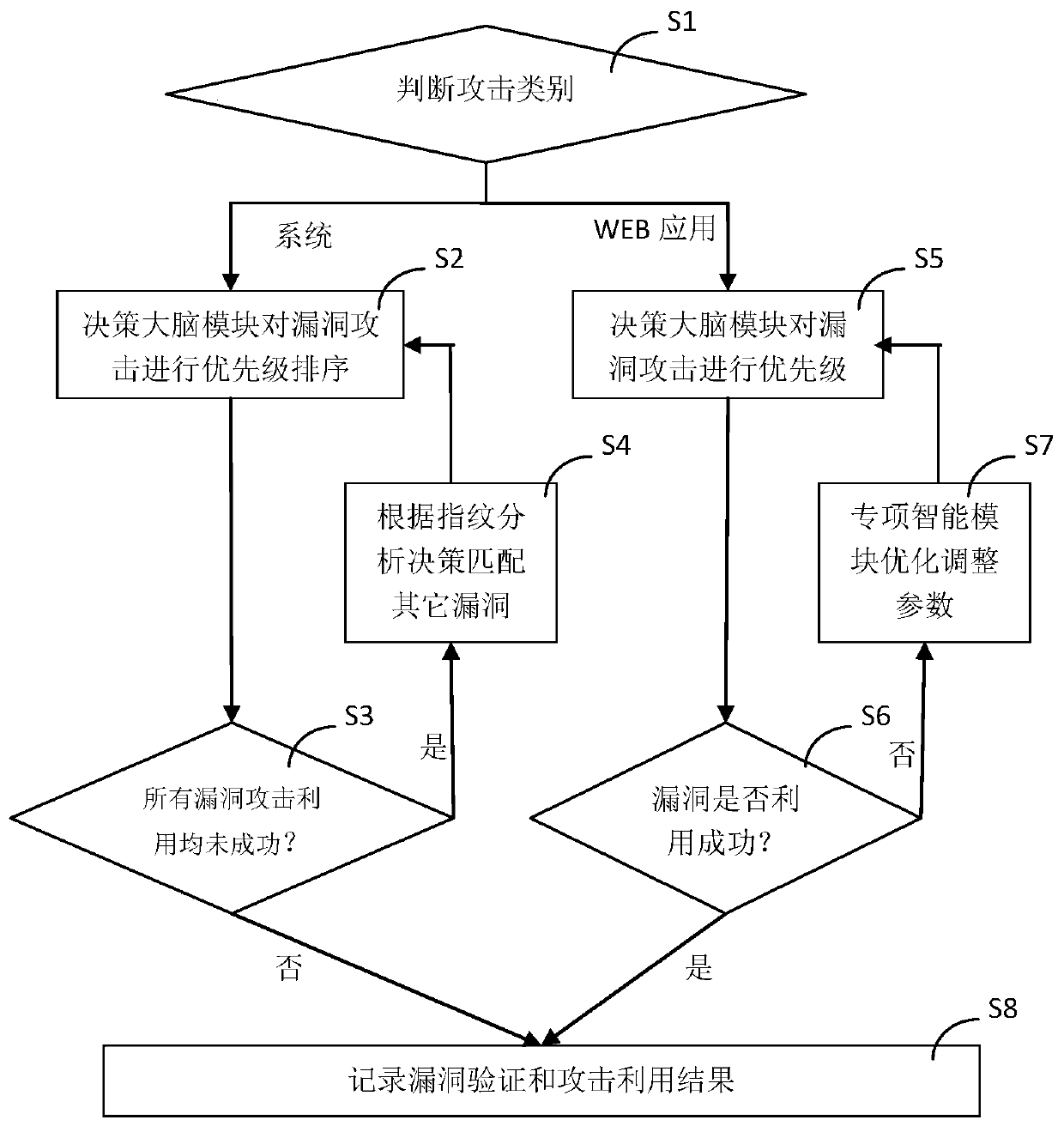
[0071] Such as figure 1 As shown, the present embodiment includes the following steps during use:
[0072] S1, determine the type of attack, enter step S2 when performing a penetration attack on the system, and enter step S5 when performing a penetration attack on a WEB application;
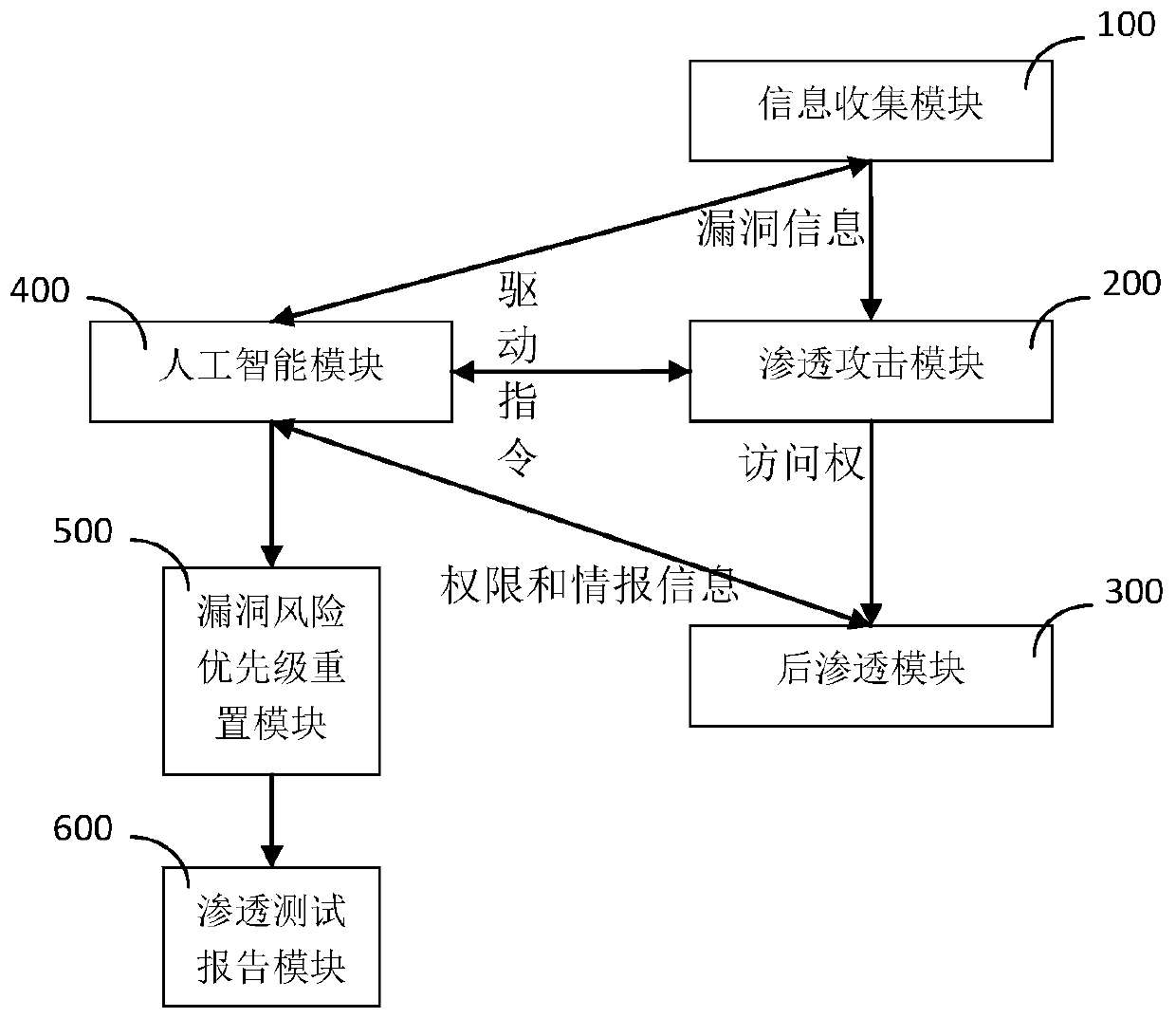
[0073] S2. The decision-making brain module 420 establishes attack branch nodes according to the attack surface, intelligence data, and vulnerability information, and prioritizes them according to the success rate of exploiting the vulnerabilities;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com