Method for detecting and defending ransomware based on access permission
A technology of access rights and software, which is applied in the direction of instruments, calculations, electrical digital data processing, etc., can solve the problems of poor accuracy and real-time performance, and achieve the effects of improving efficiency, wide application prospects, and simple structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] Such as figure 1 As shown, the present invention provides a method for detecting and defending ransomware based on access rights, comprising the steps of:
[0047] S1. Set sensitive folders in the system to be monitored, generate a list of sensitive folders, and set defense scripts and whitelists for the system to be monitored;
[0048]S2. Configure the defense script to monitor the system API required for file traversal in real time, intercept all processes that call the file traversal system API, and set it as a concerned process, and search for the software corresponding to the concerned process in the white list;
[0049] S3. When there is no software corresponding to the concerned process in the white list, configure the defense script to determine whether the folder that the concerned process calls the system API to traverse is in the list of sensitive folders;
[0050] S4. When the folders that the concerned process calls the system API to traverse are in the li...
Embodiment 2
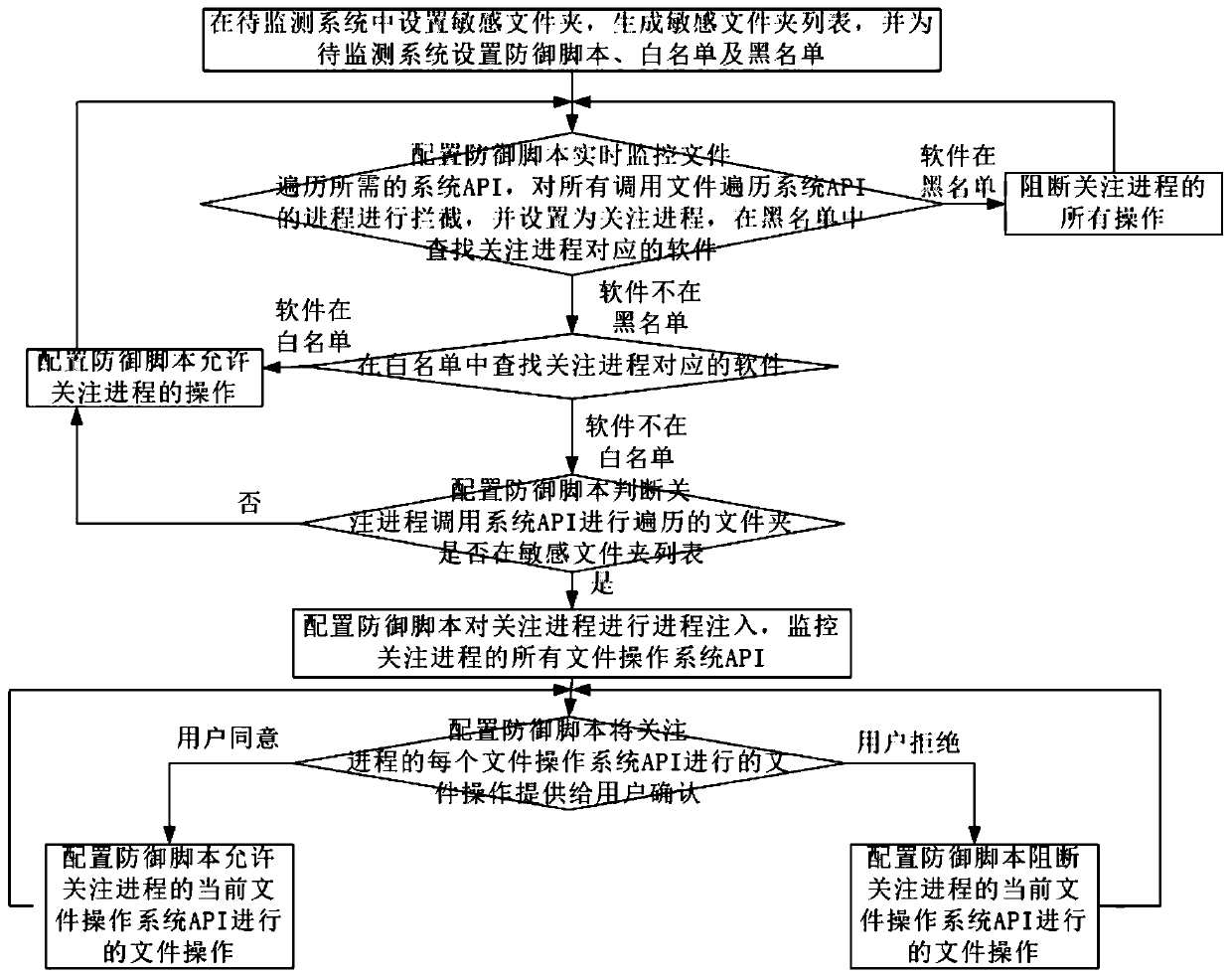
[0052] Such as figure 2 As shown, the present invention provides a method for detecting and defending ransomware based on access rights, comprising the steps of:
[0053] S1. Set sensitive folders in the system to be monitored, generate a list of sensitive folders, and set defense scripts, whitelists and blacklists for the system to be monitored; sensitive folders can be set to automatically recursively include all subfolders, and subfolders can also be set Folder hierarchy scope;
[0054] S2. Configure the defense script to monitor the system API required for file traversal in real time, intercept all processes that call the file traversal system API, and set it as a concerned process, and search for the software corresponding to the concerned process in the blacklist;
[0055] When there is software corresponding to the concerned process in the blacklist, block all operations of the concerned process, and return to step S2;
[0056] When there is no software corresponding...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com