Method and system for preventing address spoofing attack by NS reverse query
A technology of spoofing attack and reverse query, applied in transmission systems, electrical components, etc., can solve the problems of inappropriate complex scenarios, increase maintenance overhead, address spoofing attacks, etc., and achieve the effect of preventing ND address spoofing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
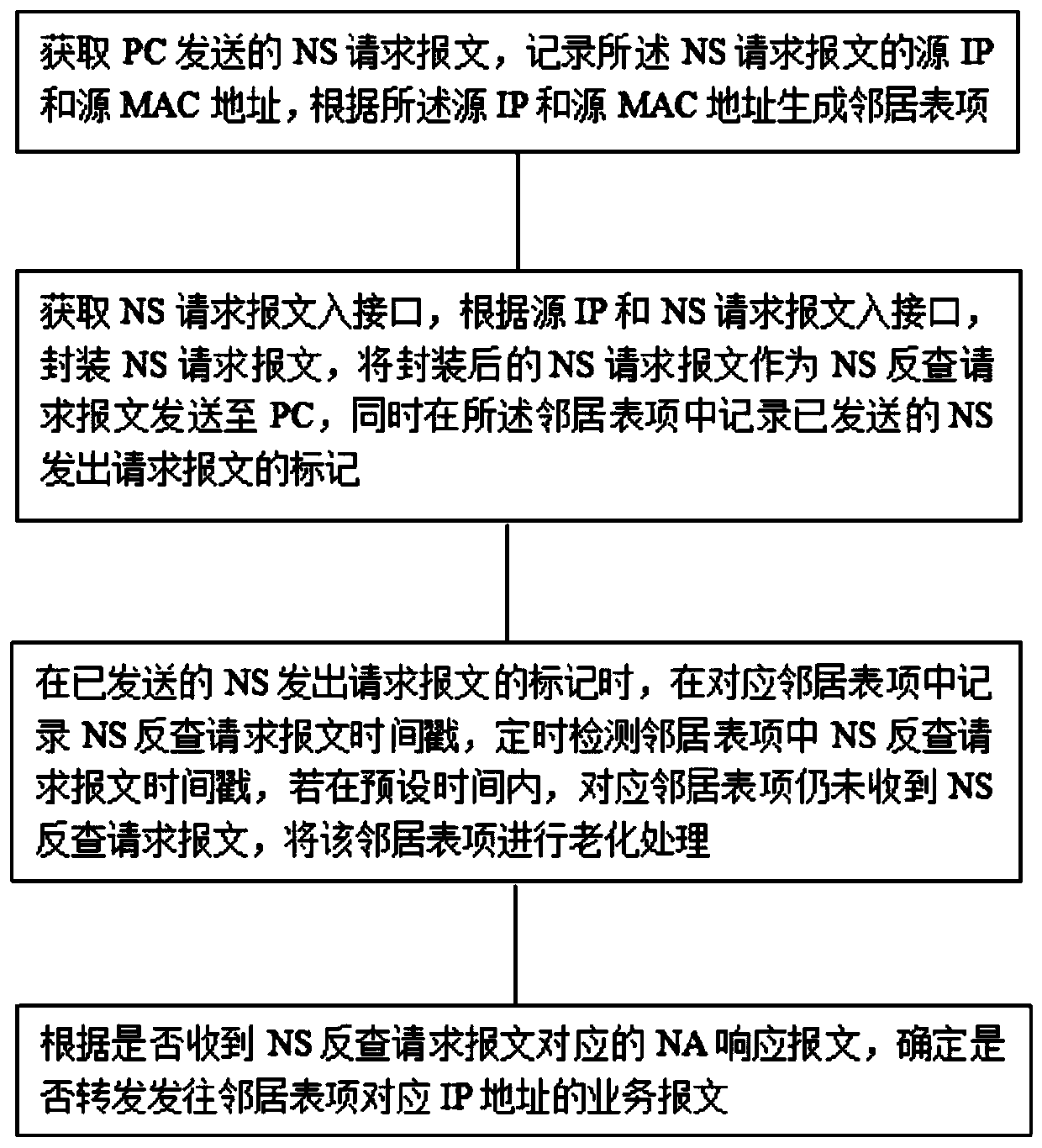
[0033] An embodiment of the present invention provides a method for NS reverse query to prevent address spoofing attacks, and a schematic flowchart of the method is as follows: figure 1 As shown, the method includes the following steps:
[0034] Obtain the NS request message sent by the PC, record the source IP and source MAC address of the NS request message, and generate a neighbor table entry according to the source IP and source MAC address;
[0035] Obtain the inbound interface of the NS request message, encapsulate the NS request message according to the source IP and the inbound interface of the NS request message, and send the encapsulated NS request message to the PC as an NS reverse check request message. The item records the flag of the sent request message sent by the NS;
[0036] When the sent NS sends the mark of the request packet, record the timestamp of the NS reverse query request packet in the corresponding neighbor entry, and regularly detect the timestamp...
Embodiment 2
[0047] An embodiment of the present invention provides a method for NS reverse query to prevent address spoofing attacks, including the following steps:
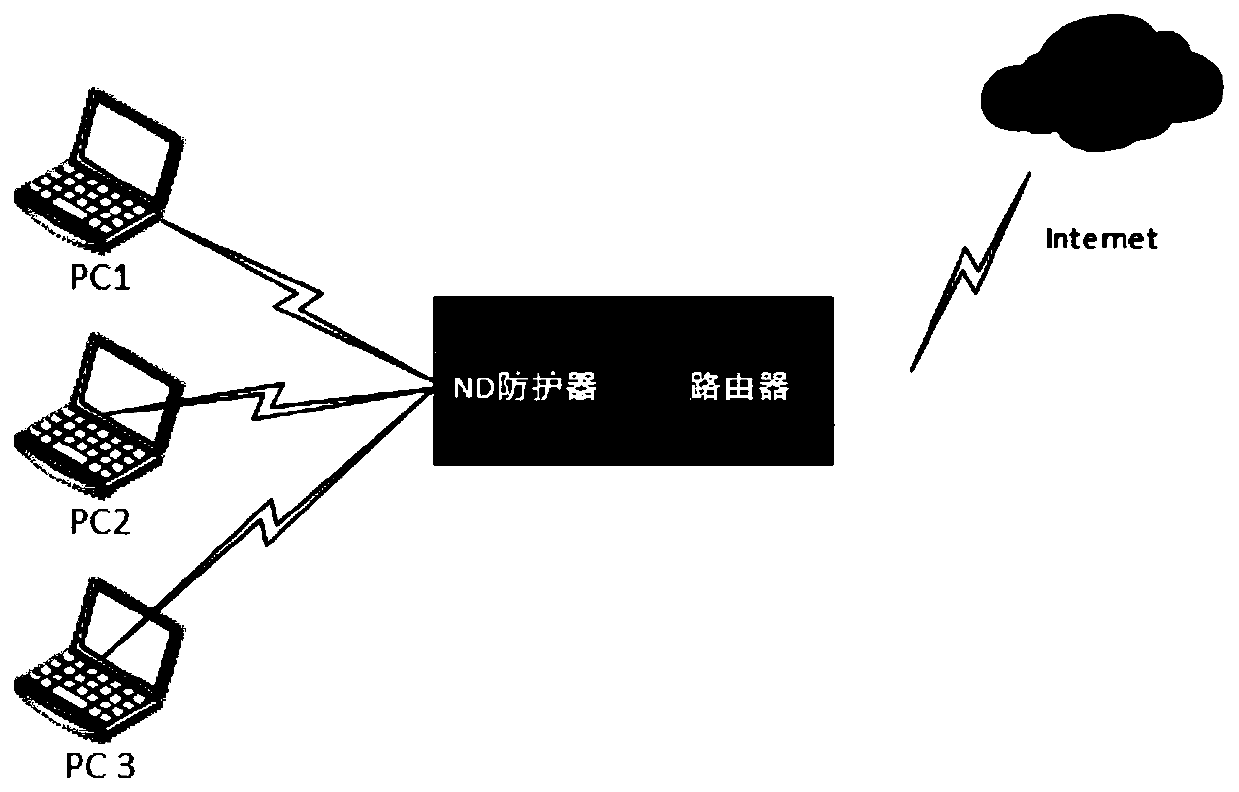
[0048] After receiving the NS request message from the PC, the ND protector records the source IP and source MAC address of the NS message to generate a neighbor table entry, and records the incoming interface of the message and the number of NS requests;
[0049] Encapsulate the NS request message according to the source IP and ingress interface, send the encapsulated request message to the PC, record the sent NS reverse check request mark in the neighbor entry, and record the NS reverse check time stamp;
[0050] If the NS request message from the PC is received again when the NS reverse check response message is not received, the number of NS requests in the neighbor table entry will increase by 1;
[0051] When the ND protector receives the NA response message of the reverse-check NS message, it sets the ND entry of the ...
Embodiment 3
[0054] The embodiment of the present invention provides a system for preventing address spoofing attacks by NS reverse query, including a neighbor entry generation module, an NS reverse query module, a message forwarding module, a timestamp recording module, and an aging processing module;
[0055] The neighbor entry generating module is used to obtain the NS request message sent by the PC, record the source IP and source MAC address of the NS request message, and generate neighbor entries according to the source IP and source MAC address;
[0056] The NS reverse lookup module is used to obtain the incoming interface of the NS request message, encapsulate the NS request message according to the source IP and the incoming interface of the NS request message, and send the encapsulated NS request message as the NS reverse lookup request message to the PC, and simultaneously record the flag of the sent NS request message in the neighbor table entry;
[0057] The time stamp recordi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com