Botnet detection method, system and storage medium
A botnet and network technology, applied in the fields of systems, storage media, and botnet detection methods, can solve problems such as low botnet detection efficiency, huge data flow, and large processing load, and achieve improved detection efficiency, low computational overhead, and features. small number of effects
Active Publication Date: 2022-06-21
ZTE CORP
View PDF6 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
However, these methods require a variety of data information, huge data streams, and need to analyze data packets to extract multiple features, and the processing load is too large, resulting in low detection efficiency of botnets
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
no. 1 example
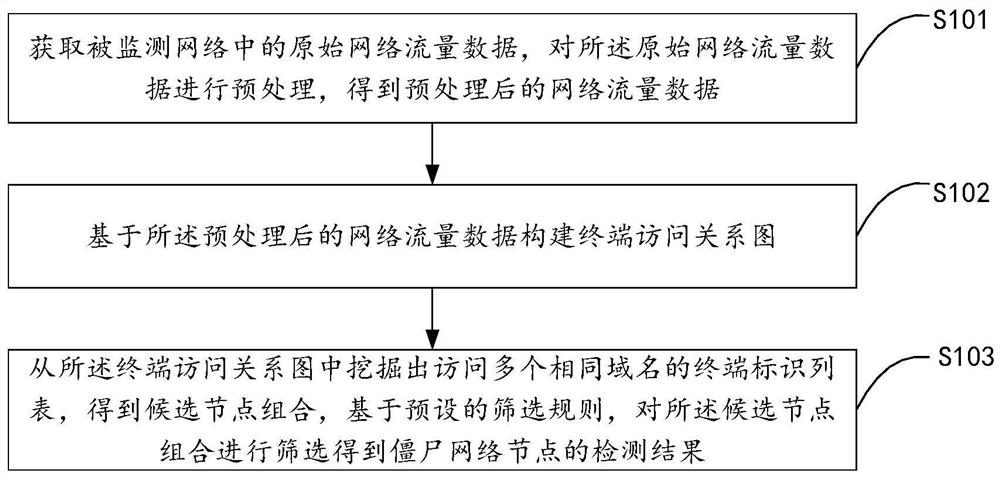
[0178] like Image 6 As shown, the second embodiment of the present invention proposes a botnet detection method, based on the above figure 2 In the first embodiment shown, the method further includes:
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
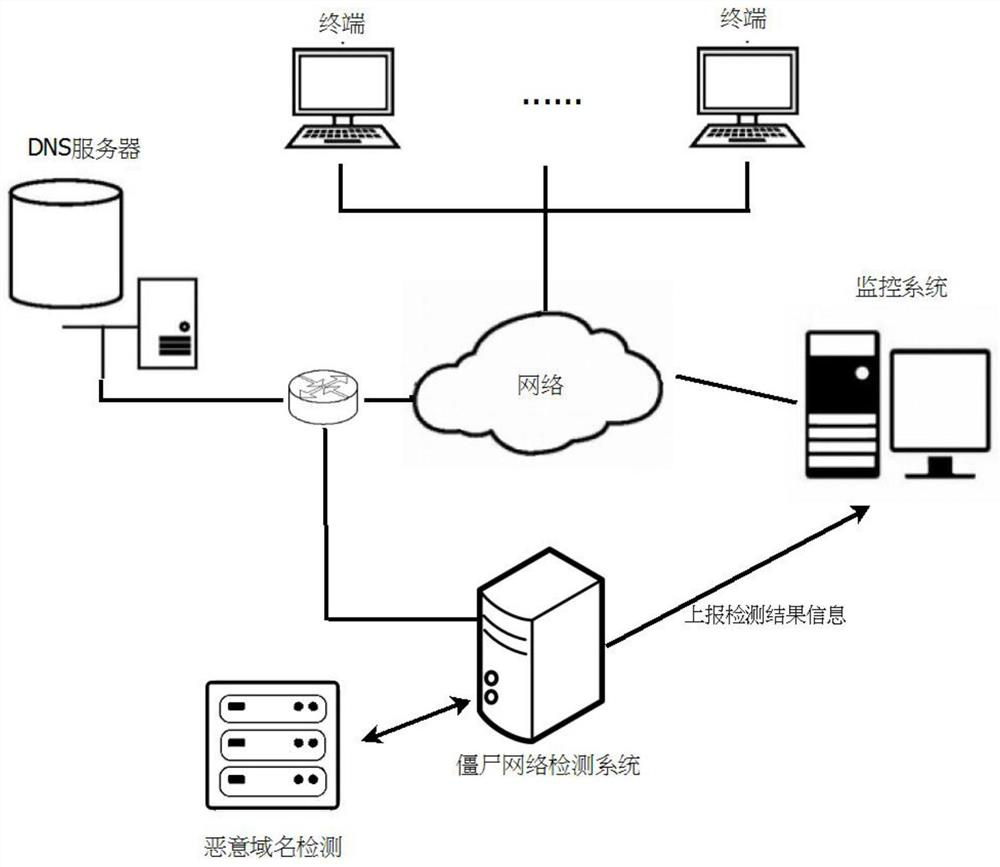
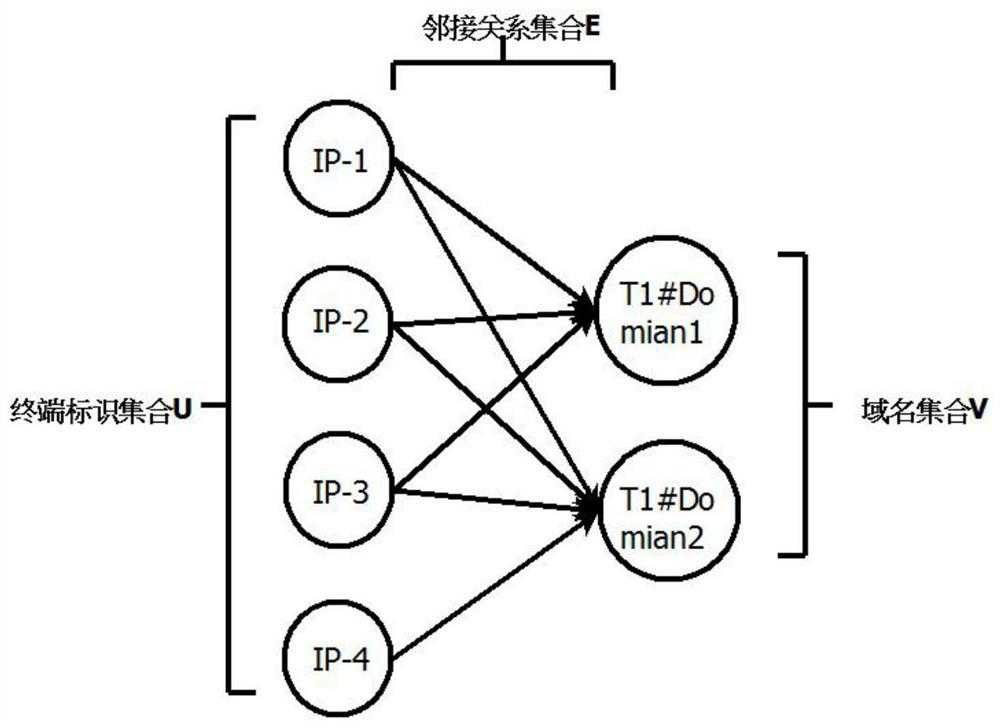
The invention discloses a botnet detection method, system and storage medium. The method comprises: obtaining original network flow data in the monitored network, preprocessing the original network flow data, and obtaining preprocessed network flow data; The preprocessed network traffic data constructs a terminal access relationship graph; from the terminal access relationship graph, a list of terminal identifiers accessing multiple same domain names is mined to obtain a candidate node combination. Based on the preset screening rules, the candidate node combination is screened to obtain Detection results of botnet nodes. The scheme of the present invention has fewer types of applied data, fewer features extracted from data traffic, less computational overhead, and can effectively improve detection efficiency, and the scheme does not need to be detected based on well-known botnet behavior characteristics, and can be better applied detection of unknown botnet threats.
Description
technical field [0001] The invention relates to the technical field of network security, in particular to a botnet detection method, system and storage medium. Background technique [0002] Botnet refers to the use of one or more means of propagation to infect a large number of hosts with the bot (BOT program) virus, thereby forming a one-to-many command and control between the controller and the infected host. and Control, C&C) network. The attacker spreads the bot program to infect a large number of hosts on the Internet through various channels, and the infected host accepts the attacker's instructions through a control channel to form a botnet. This attack method provides attackers with a hidden, flexible and efficient one-to-many command and control mechanism, enabling attackers to achieve information theft, distributed denial attacks, and spam sending, and has become an important issue in the current network security field. threaten. [0003] At present, the mainstr...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L9/40H04L61/4511
CPCH04L63/1416H04L63/1425H04L63/145H04L2463/144H04L61/4511H04L43/0876H04L43/04H04L41/142H04L43/065
Inventor 成黎田甜李依馨罗熙杨婧王利明
Owner ZTE CORP
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Patsnap Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com