A method and device for solving hash collision
A hash collision and device technology, applied in the computer field, can solve problems such as hash algorithm hash collisions, reduce the number of hash collisions, improve the performance of the whole machine, and ensure data consistency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
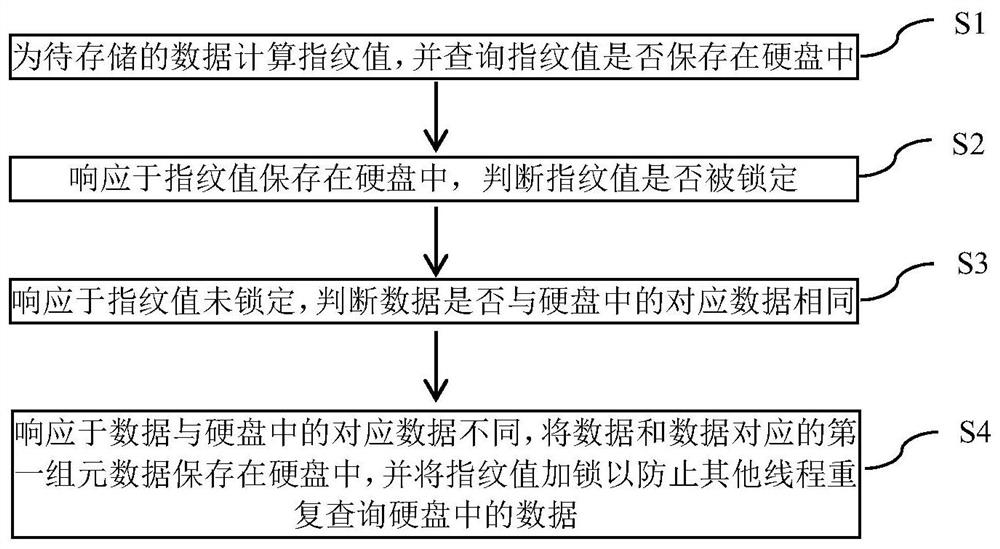
[0040] 1. The host will issue multiple data of a certain size;
[0041] 2. Calculate the fingerprint value of each data through the hash algorithm;
[0042] 3. Query whether the finger pattern value is saved in the store;
[0043] 4. When the fingerprint value is not queried in the system, it means that the current processing is non-repetitive data, which needs to be saved to the hard disk, and save the fingerprint value - physical address metadata, logical address - physical address metadata and Physical address - logical address metadata;
[0044] 5. When the finger pattern value is queried in the system, it is determined whether the finger pattern is locked. When it is not locked, the data is compared to the current data in the hard disk, and the data is identical, and the data is identical to the current processing is duplicate data. Do a heavy deletion, the data does not need to be saved to the hard disk, just save the logical address of the data - physical address metadata a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com