Content security for video stream
A technology for video streaming and video capture, applied in secure communication devices, selective content distribution, and key distribution, can solve privacy issues, encryption, decryption of video data by unauthorized users, etc., to increase scalability and reduce computational complexity degree of effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will now be described more fully hereinafter with reference to the accompanying drawings, in which embodiments of the invention are shown. The systems and devices disclosed herein will be described during operation.
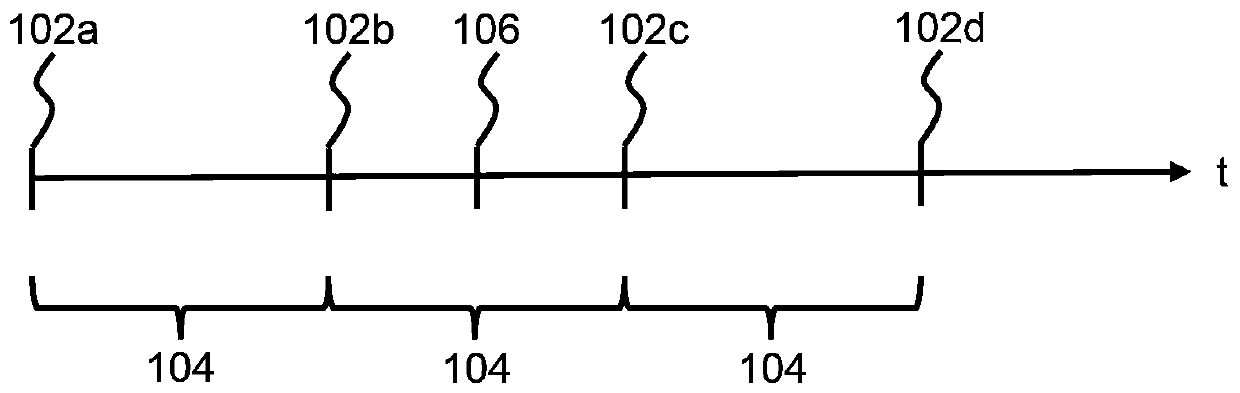
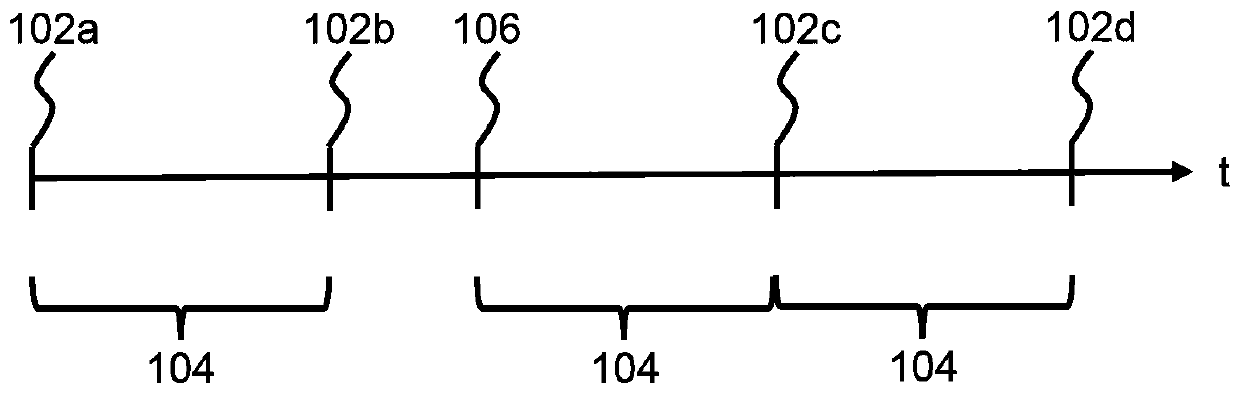
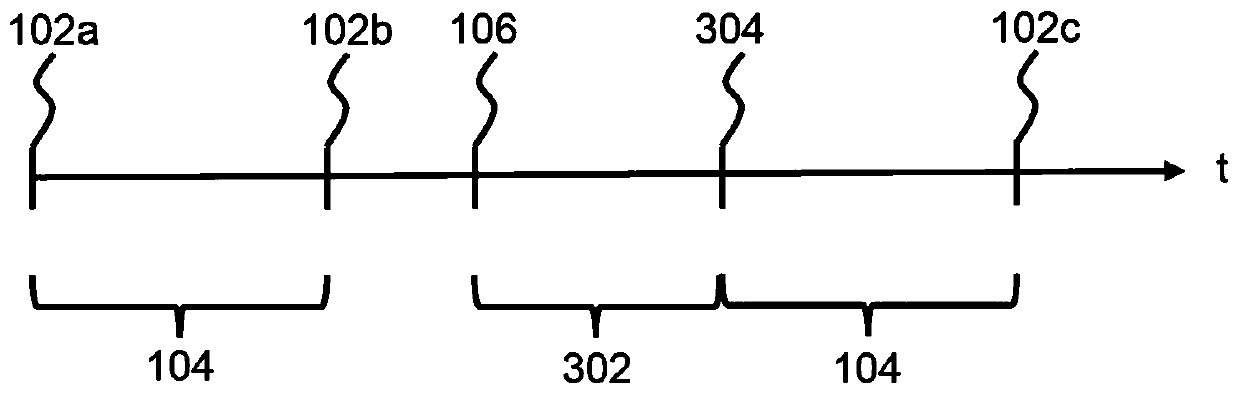
[0038] It is an object of the invention to reduce the risk of unauthorized access to video streams. One solution could be to encrypt the memory where the video stream is stored. However, the security level of this scheme is considered insufficient. To further reduce the risk of unauthorized access to the video stream, the video stream may be encrypted using an encryption key. To increase the level of security, different parts of the video stream can be encrypted with different encryption keys. Figure 1 to Figure 5 Different schemes for changing encryption keys used for encryption of video streams according to the invention are shown.
[0039] It should be understood that the following examples only discuss encryption of video str...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com