Network encryption method, system, medium and equipment based on southbound interface
A technology of southbound interface and encryption method, which is applied in the field of SDN and can solve the problem of no effective solution for network service encryption without a controller.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0028] Example 1: Please refer to figure 1 ,
[0029] A southbound interface-based network encryption method includes:
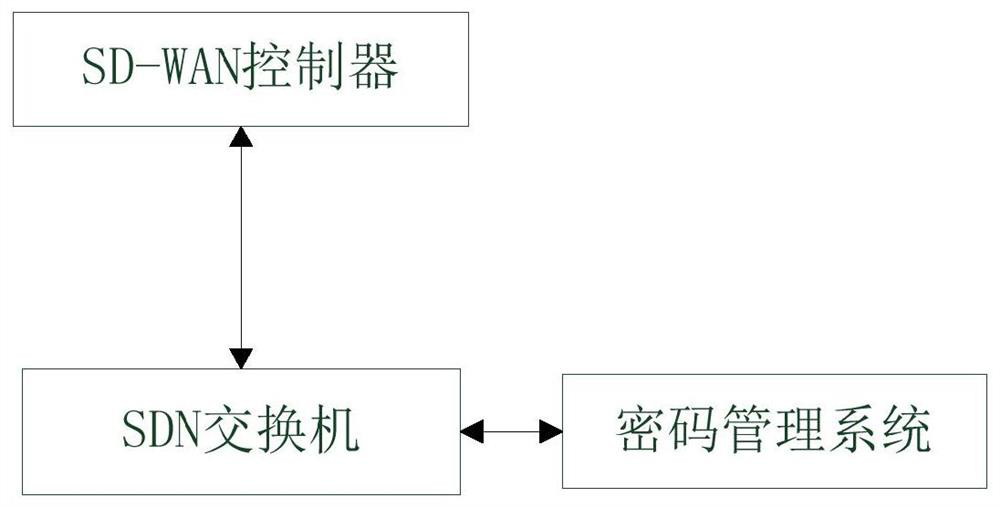
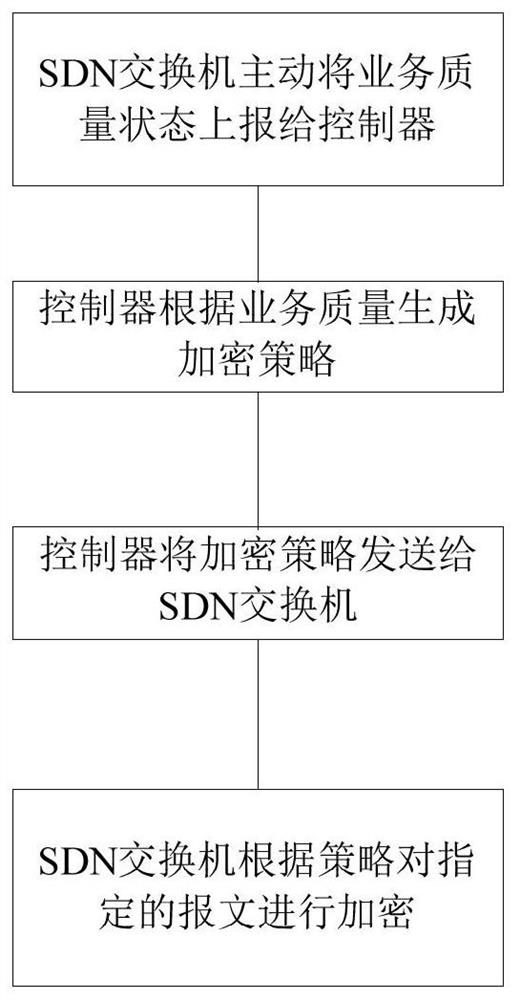
[0030] Step 1: The SD-WAN controller reports the message according to the service quality status information, queries the encryption list, obtains the encryption policy, and forms an encryption policy message;
[0031] Step 2: The SD-WAN controller sends an encryption policy message through the southbound interface;
[0032] Step 3: The SDN switch encrypts and forwards the specified message according to the encryption policy message.
Embodiment 2
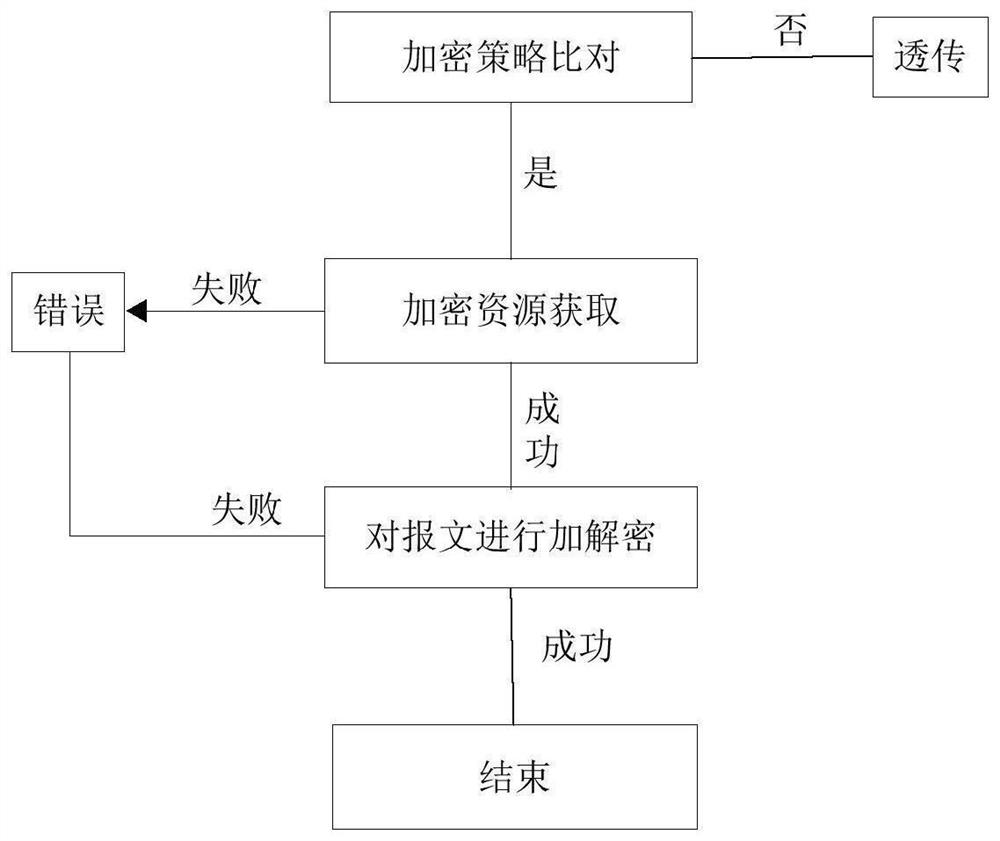
[0033] Embodiment two: if Figure 5 As shown, on the basis of Embodiment 1, the SD-WAN controller reports the message according to the service quality status information, queries the encryption list (wherein the encryption list is shown in Table 1), obtains the encryption policy, and forms an encryption policy message specifically indicating is:
[0034] According to the total bandwidth Total-band and the remaining bandwidth left-band, a service quality status information reporting message is formed;
[0035] Query the encryption list according to the total-band control word and left-band control word in the service quality status information report message, and obtain the encryption strategy including the Encry_alga control word, Encry_mode control word, key_index control word and flow_id control word; the service quality status information The format of the report message is: version+type+length+xid+flags1+Total-band+left-band; flags1 is a flag bit, indicating the status in...
Embodiment 3
[0055] Embodiment three, on the basis of embodiment one or 2, such as Figure 5 As shown, the specific format of the message of the encryption policy:
[0056] version+type+length+xid+flags2+Encry_alga+Encry_mode+key_index+flow_id; among them, version indicates the version number; type indicates the type of openflow message; length indicates the length of the message; xid indicates the processing id associated with the message; flags2 indicates The number of the policy indicates whether this policy is to add an encryption policy or delete an encryption policy; Encry_alga indicates the specific encryption algorithm; key_index indicates the key index, flow_id indicates the characteristic information of the message to be encrypted; Encry_mode indicates the encryption mode.
[0057] For example: the value of the type field is 81, indicating that this is an encryption policy sent by the controller to the switch.
[0058] Of course, the above message format can also be further expa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com