A detection method for illegal file upload
A file upload and detection method technology, applied in the field of anomaly detection, can solve problems such as inaccurate detection results, and achieve the effects of low accuracy, poor flexibility, and accurate detection of the legitimacy of uploading behaviors.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
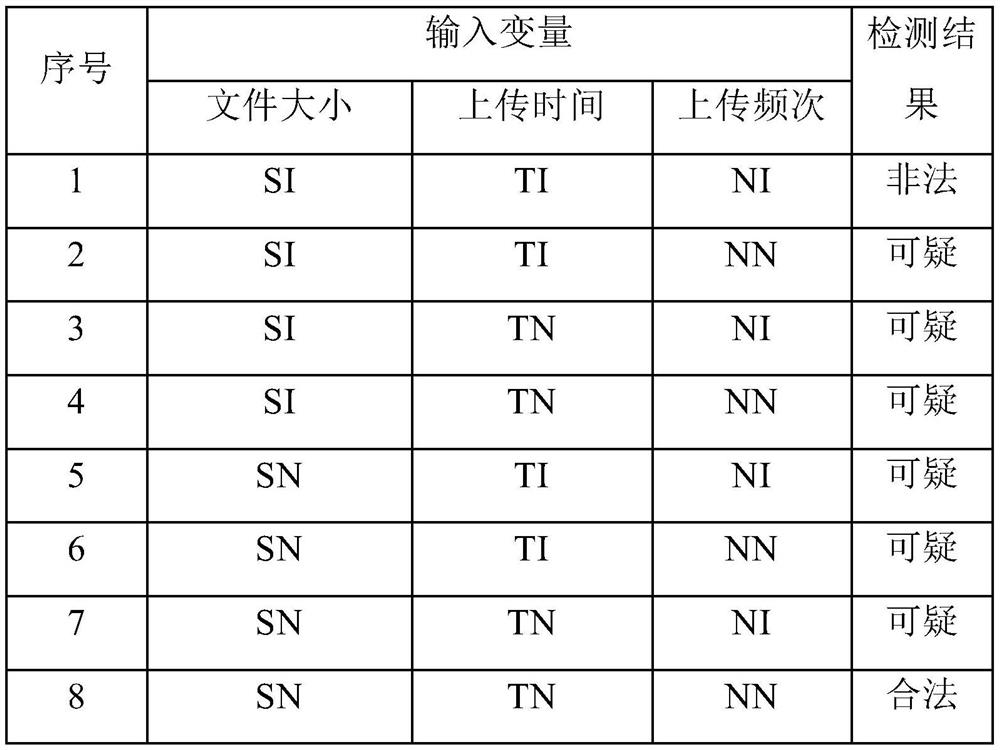
[0033] First, the terms involved in the embodiments of the present application are explained as follows:
[0034] Fuzzification and fuzzy set: Fuzzification is the process of converting the determined value of the input quantity of the fuzzy controller into the corresponding fuzzy language variable value, and the fuzzy language variable value is a fuzzy set, so the fuzzification method should give Transformation method for fuzzy sets.
[0035] Fuzzy rules: the essence is the binary fuzzy relationship R defined in X and Y, and the form of fuzzy rules is: if x is Athens y is B. where A and B are linguistic values defined by fuzzy sets on domains X and Y.
[0036] Defuzzification: Defuzzification is the transformation of fuzzy values into unambiguous values of the domain of discourse at an appropriate scale as the output of the system.
[0037] In order to enable those skilled in the art to better understand the solution of the present application, the technical solution ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com