Multi-application identity authentication system and method
An identity authentication and multi-application technology, applied in the system field of multi-application identity authentication, can solve problems such as easy confusion or forgetting, stolen passwords, cumbersome processes, etc., and achieve the effects of ensuring identity security, simplifying identity authentication, and reducing burdens
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] The present invention provides a multi-application identity authentication system, such as figure 1 As shown, it includes the client, the application, and the proxy service center. The client establishes a connection with the application through the proxy service center.
[0037] The proxy service center includes a proxy key generation module, a proxy key storage module, a control module, and an encryption and decryption module. The proxy key generation module is used to generate the proxy public key and private key pair; the proxy key storage module is used to store the proxy public key and private key pair; the control module is used to communicate with the client and the application terminal according to the preset communication protocol ; The encryption and decryption module is used for encryption and decryption of communication data. The proxy service center can be a proxy server, or a software development kit (SDK) for realizing the same function.
[0038] The c...
Embodiment 2
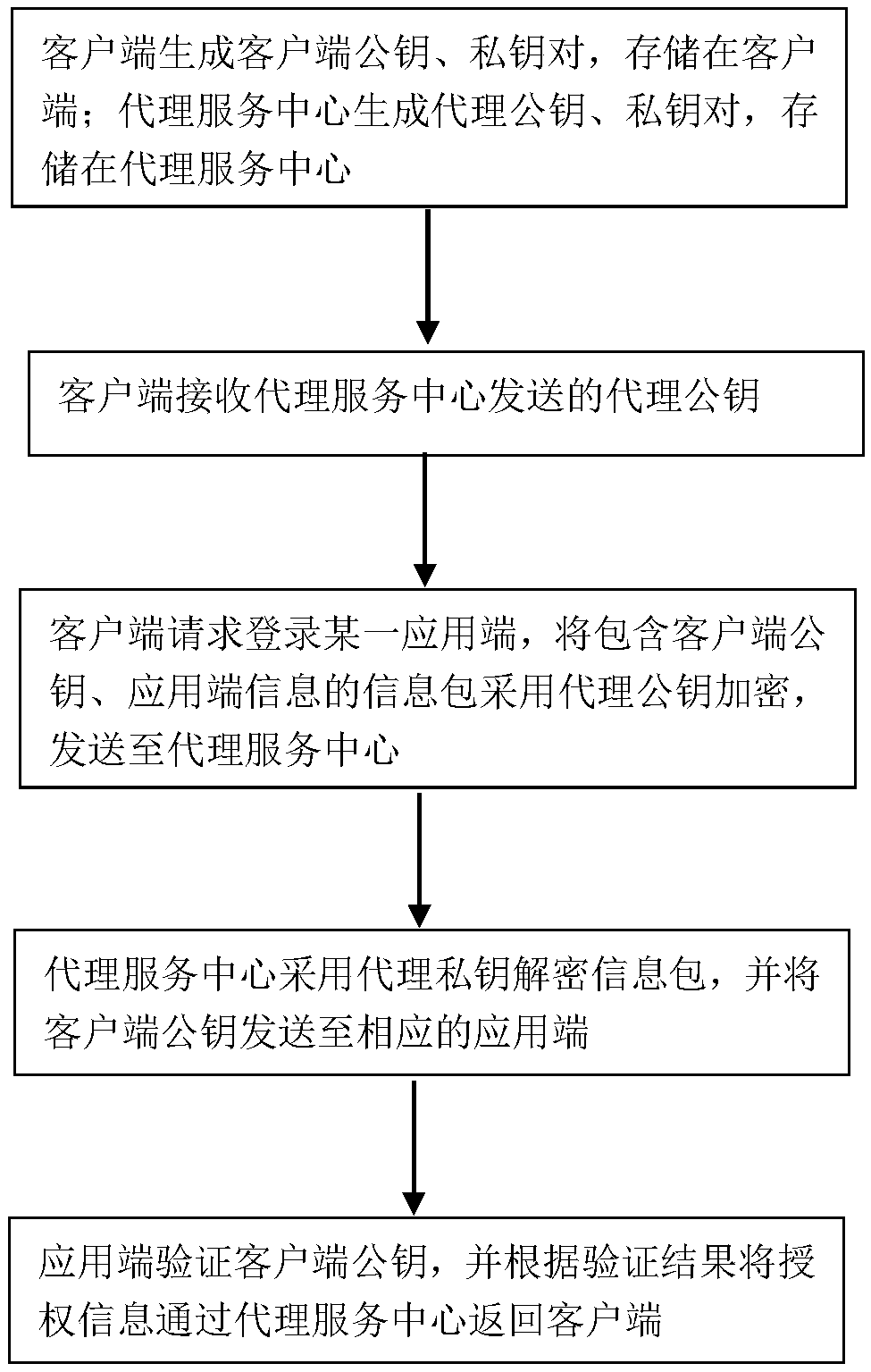
[0042] The present invention provides a method for multi-application identity authentication, such as figure 2 shown, including the following steps:
[0043] Step 1: The client generates a client public key and a private key pair and stores them in the client; the proxy service center generates a proxy public key and a private key pair and stores them in the proxy service center;
[0044] The client in step 2 receives the proxy public key sent by the proxy service center;
[0045] The client in step 3 requests to log in to a certain application end, encrypts the information packet containing the client public key and application end information with the agent public key, and sends it to the agent service center;
[0046] Step 4: The proxy service center uses the proxy private key to decrypt the information package, and sends the client public key to the corresponding application end;
[0047] Step 5: The application side verifies the client public key;
[0048]When the cli...
Embodiment 3
[0053] The present invention provides another method for multi-application identity authentication, which includes the following steps:
[0054] Step 1: The client generates a client public key and a private key pair, which are stored in the client, and the proxy service center generates a proxy public key and a private key pair, which are stored in the proxy service center;
[0055] The client described in step 2 sends the client public key to the agency service center;
[0056] The client in step 3 requests to log in to a certain application end, encrypts the information packet containing the client public key and application end information with the client private key, and sends it to the agency service center;
[0057] Step 4: The proxy service center uses the client public key to decrypt the information packet, and uses the proxy private key to encrypt the client public key and sends it to the application side;
[0058] In step 5, the application side uses the proxy publ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com