Privacy leakage protection method based on data traceability
A technology for data traceability and privacy leakage. It is used in digital data protection, electronic digital data processing, and special data processing applications. It can solve the problems of complex threats and scattered terminals, and achieve the effect of protecting privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention is further described below in conjunction with accompanying drawing.
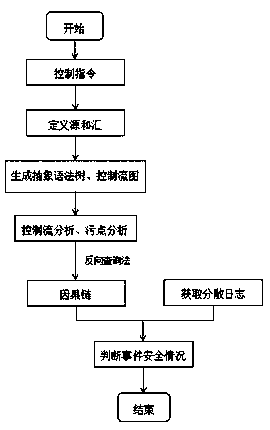
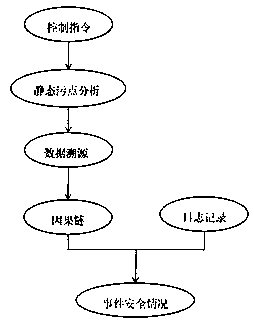
[0023] Such as figure 1 , 2 As shown, a privacy leakage protection method based on data traceability, taking the smart home platform as an example, includes the log fusion generated by the operation of smart home appliances (such as smart speakers, automatic curtains, smart lights, etc.) and the control command detection of the cloud center. It is characterized in that it conducts static taint analysis on the control instructions of the cloud center, uses data traceability technology to find the corresponding logical relationship at the code level for all events that occur in the user's room, and integrates the logs of scattered smart home appliances to obtain a complete centralized system. Logging system (a collection of causal chains of events); includes the following steps:
[0024] Step 1. Use static taint analysis technology to analyze all the control instructions about a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com