User portrait method applied to field of network security
A network security and user technology, applied in the field of information security, to achieve accurate user behavior, accurate description, and reduce the effect of false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
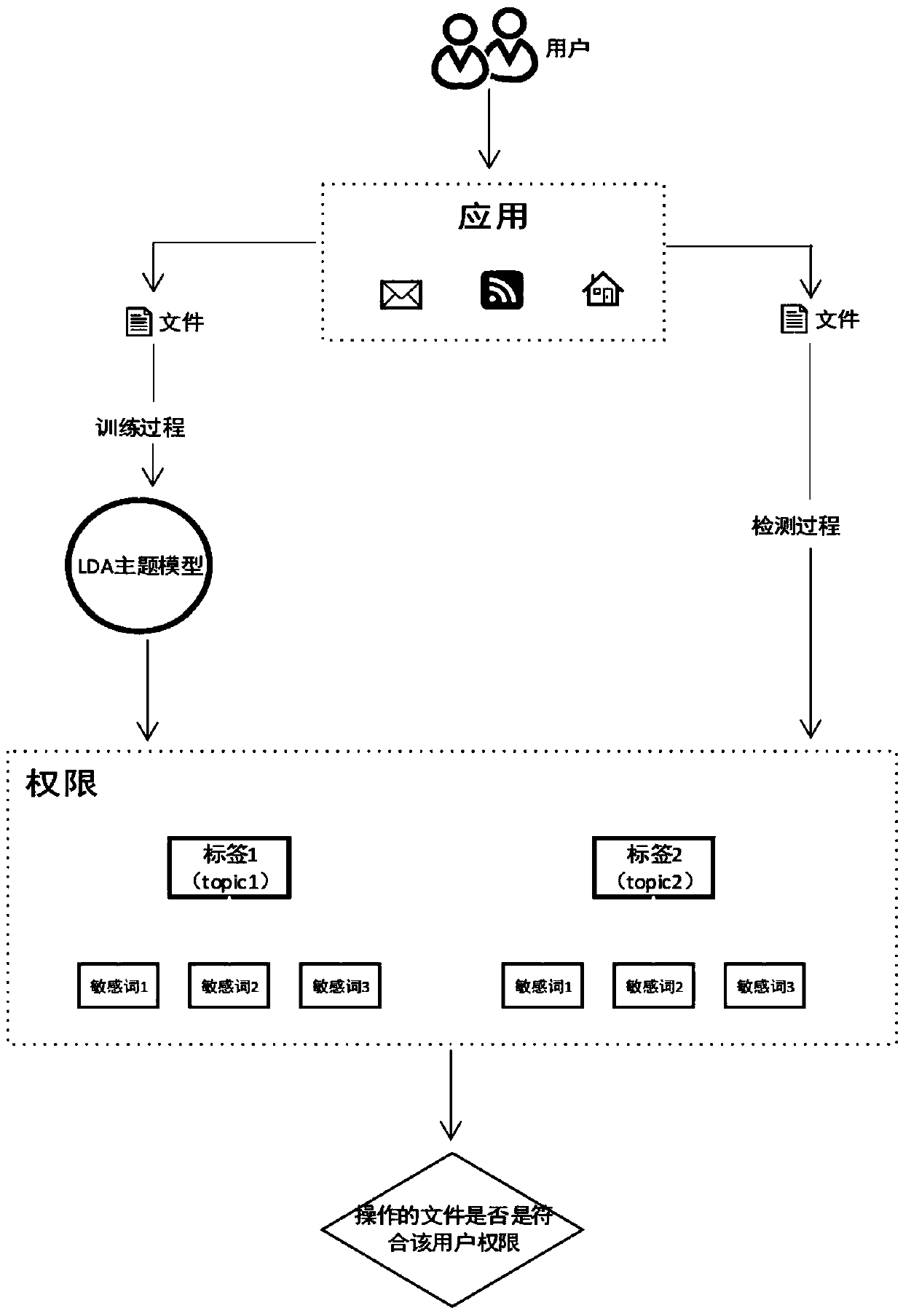
[0011] 1. Obtain data
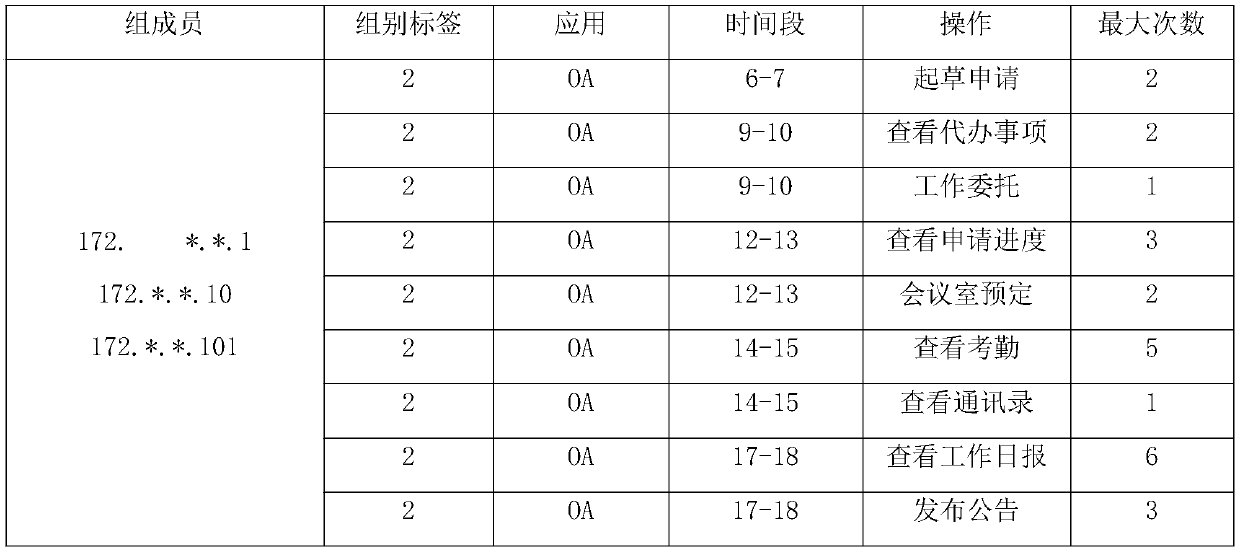
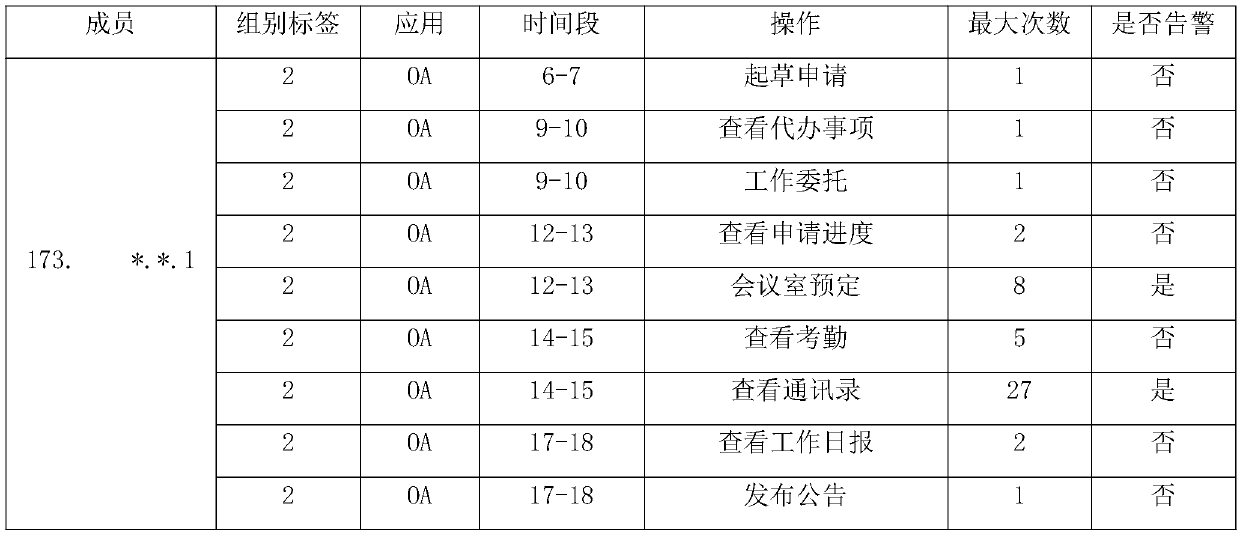
[0012] Get user's data from multiple data sources. Structured data includes: user demographic attributes (such as age, gender, location, department, education level, etc.), job characteristics (such as working hours, workload, working years, overtime hours, working time periods, etc.). Semi-structured data includes: system operations (such as authority compliance, commonly used functions, operation frequency, operation time period, valid operands, etc.), sensitive operations (such as unauthorized operations, non-personal operations, data leakage, etc.). Unstructured data is mainly the specific content of traffic, in the format of text, pictures, audio, video, etc.
[0013] 2. Data preprocessing
[0014] It mainly deals with structured and semi-structured data. There are two main directions of processing: statistical description, and vectorized description.
[0015] In machine learning, non-digital data can only be embedded in one-hot without convers...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com