Method for detecting intranet lateral movement attack
A lateral movement, intranet technology, applied in the directions of instruments, character and pattern recognition, electrical components, etc., can solve problems such as inability to defend against advanced attacks, difficult to eradicate attackers hiding, and inability to effectively solve the problem of lateral movement attack detection. The effect of low reporting rate, protection of information security, and high detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the purpose, features and advantages of the present invention more obvious and easy to understand, the technical core of the present invention will be further described in detail below in conjunction with the accompanying drawings and examples instruction of.
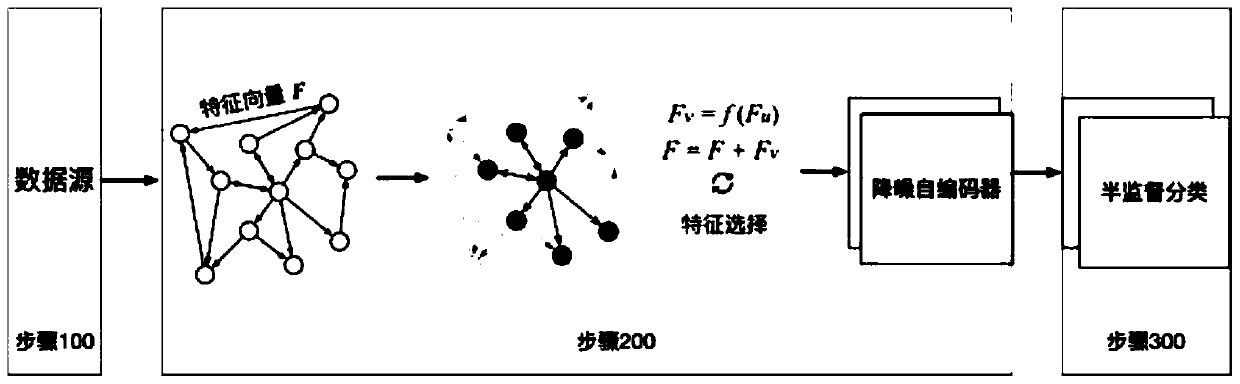
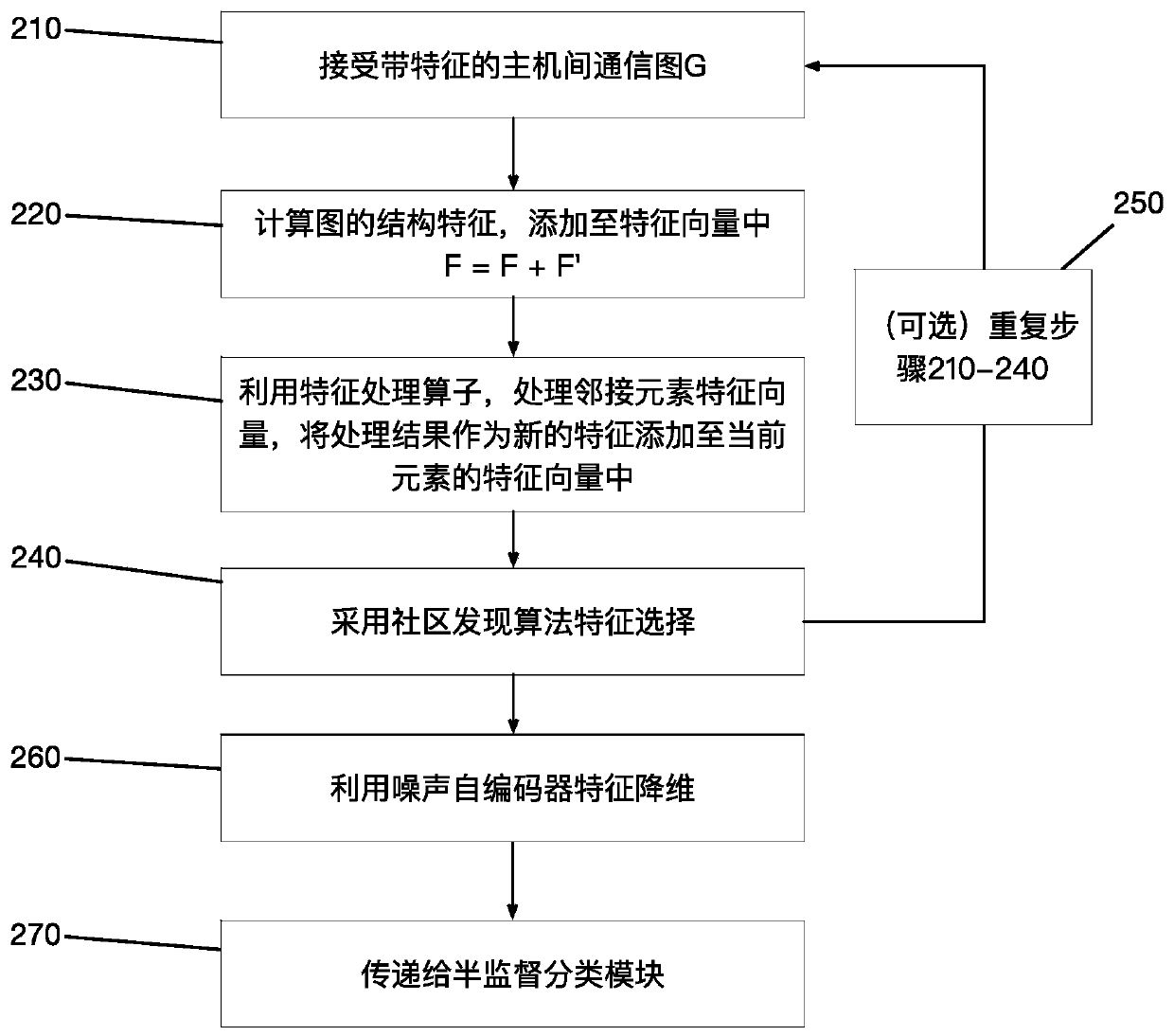
[0037] This embodiment discloses a reliable and effective method for detecting intranet lateral movement attacks, such as figure 1 As shown, this method is mainly composed of four parts: information collection, communication construction between hosts, network representation learning and semi-supervised classification. The main steps are as follows.
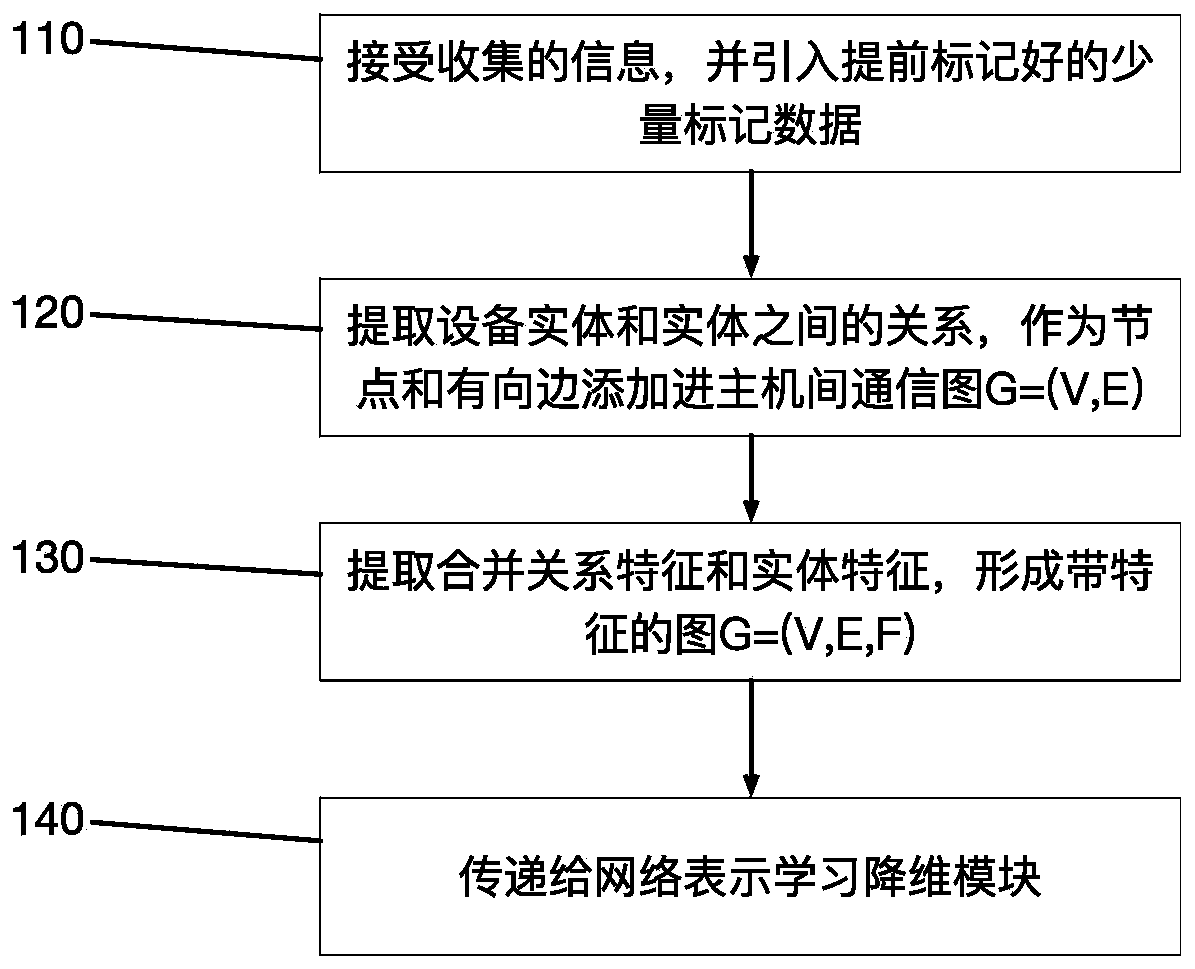
[0038] Step 100, the enterprise uses the intranet data collection module to collect information according to its own capabilities and needs. The collected information, such as the number of successful / failed logins between...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com