Secure re-use of private key for dynamic group of nodes
A private key and group technology, applied in secure communication devices, data processing applications, user identity/authority verification, etc., can solve problems such as attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] blockchain network
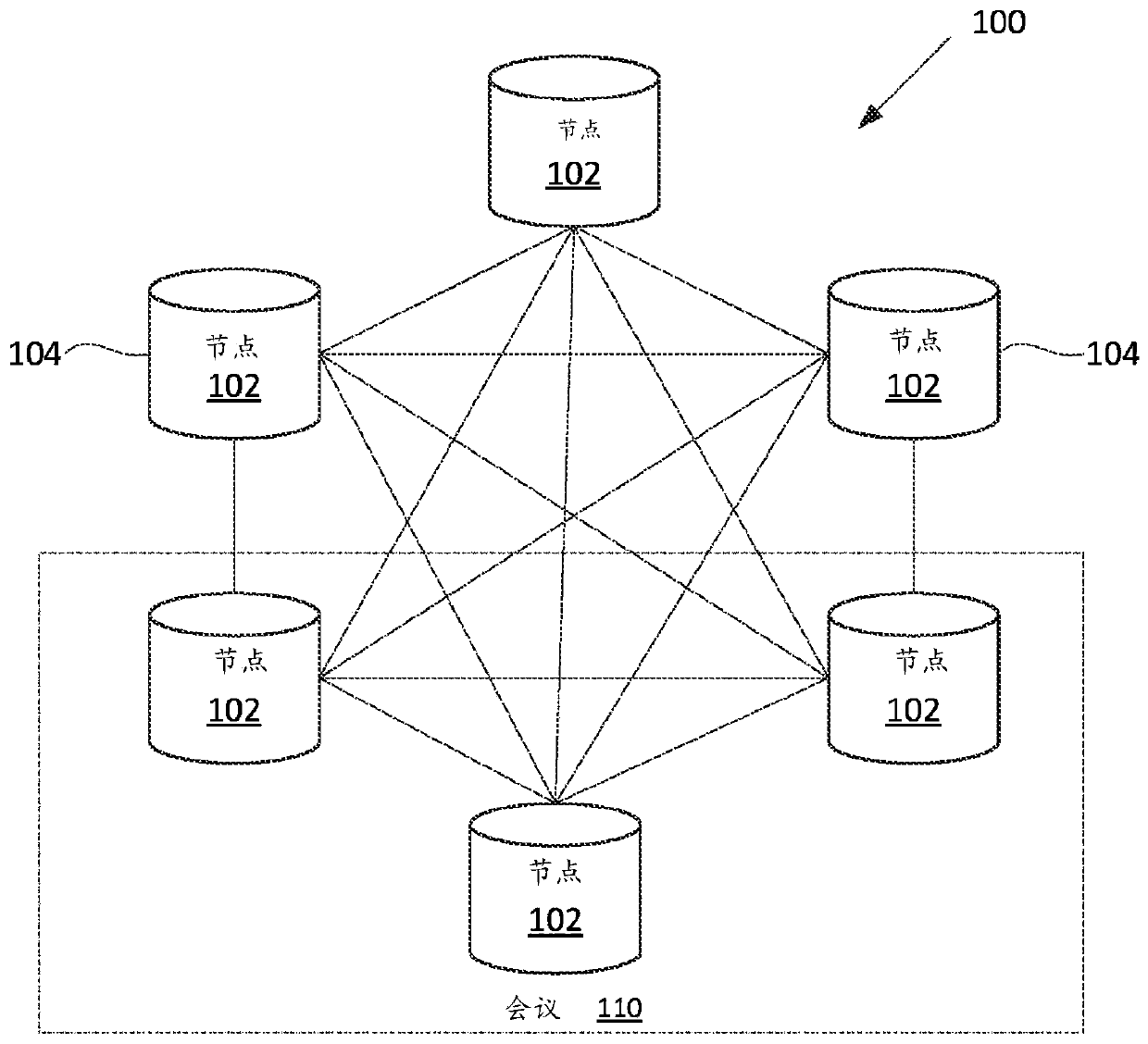
[0036] first reference figure 1 . figure 1 An exemplary blockchain network 100 associated with a blockchain is shown in block diagram form. A blockchain network can be a public blockchain network, which is a peer-to-peer open membership network in which anyone can join without invitation or consent from other members. Distributed electronic devices running instances of the blockchain protocol under which the blockchain network 100 operates may participate in the blockchain network 100 . Such distributed electronic devices may be referred to as nodes 102 . The blockchain protocol can be, for example, the Bitcoin protocol.
[0037] The electronic devices that run the blockchain protocol and form the nodes 102 of the blockchain network 100 can be various types of devices including, for example, desktop computers, laptop computers, tablet computers, servers, mobile devices such as smart phones, such as Wearable computers like smart watches, or othe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com