Ciphertext data set intersection calculation method, device, system, client, server and medium
A computing method and data set technology, applied in the field of data security, can solve problems such as the inability to prohibit set intersection operations, the inability to specify users, and the inability to achieve fine-grained authorization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0107] Such as figure 1 As shown, this embodiment provides a method for calculating the intersection of ciphertext data sets, which is applied to the client and includes the following steps:
[0108] S101. Generate a user's public key and private key.
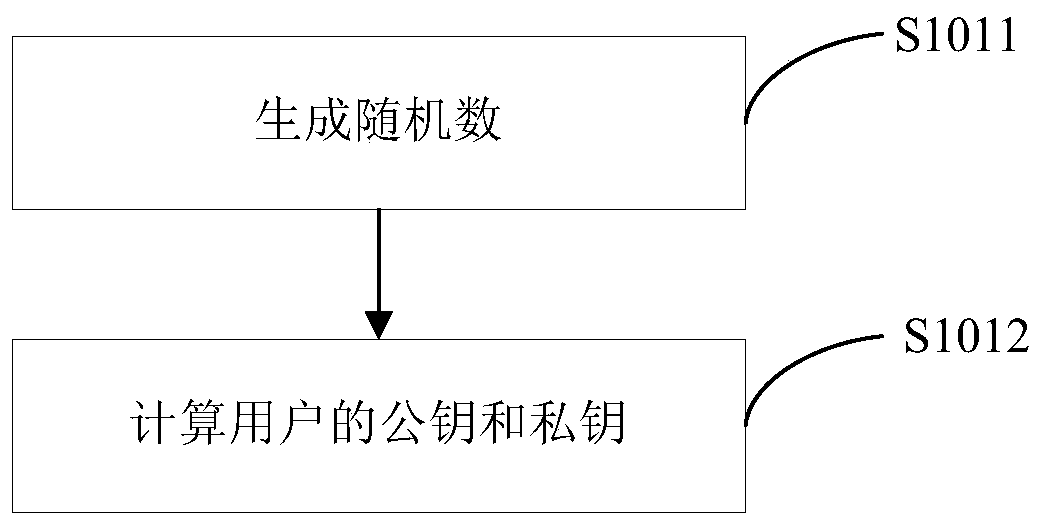
[0109] Each user uses a client, for a certain user i, the public key and private key of the user i are generated by the client it uses, such as figure 2 shown, including:
[0110] S1011. After user i starts the client and chooses to register, the client generates a random number
[0111]S1012. The client calculates the public key of user i and the private key (x i ,y i ,z i ).
[0112] S102. Encrypt the plaintext data set according to the plaintext data set and the public key input by the user to obtain a ciphertext data set, and send the ciphertext data set to the server.
[0113] Such as image 3 As shown, the step S102 specifically includes the following steps:
[0114] S1021. User i inputs plaintext data set D...
Embodiment 2
[0149] Such as Figure 10 As shown, this embodiment provides a method for calculating the intersection of ciphertext data sets, which is applied to a server and includes the following steps:
[0150] S1001. Receive a ciphertext data set sent by a client, and store the ciphertext data set in a ciphertext database.
[0151] According to the plaintext data set and public key input by the user, the client encrypts the plaintext data set to obtain the ciphertext data set, and sends the ciphertext data set to the server. After the server receives the ciphertext data set sent by the client, Store the ciphertext dataset in the ciphertext database.
[0152] S1002. Receive authorization information sent by the client.
[0153] After the user sends a ciphertext data set intersection calculation request to the server through the client, as described in Embodiment 1, four authorization levels can be selected (the first authorization level, the second authorization level, the third author...
Embodiment 3
[0188] Such as Figure 13 As shown, this embodiment provides a ciphertext data set intersection calculation system, the system includes n clients 1301 and a server 1302, n clients 1301 have the same function, but are used by different users, that is, a shared There are n users, and each user uses a client 1301 , and the n clients 1301 cannot communicate with each other, but are respectively connected and communicated with the server 1302 .
[0189] The client 1301 is used to generate the user's public key and private key; according to the plaintext data set and public key input by the user, the plaintext data set is encrypted to obtain the ciphertext data set, and the ciphertext data set is sent to the server 1302: According to the authorization level selected by the user, generate the authorization information of the authorization level; send the authorization information to the server 1302; receive the intersection of the ciphertext data set sent by the server 1302; accordin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com