Full-mesh link protection method and device, equipment and storage medium
A full mesh and link technology, applied in data exchange network, digital transmission system, electrical components, etc., can solve problems such as no link available, service interruption, etc., to ensure normal communication, stability and robustness Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
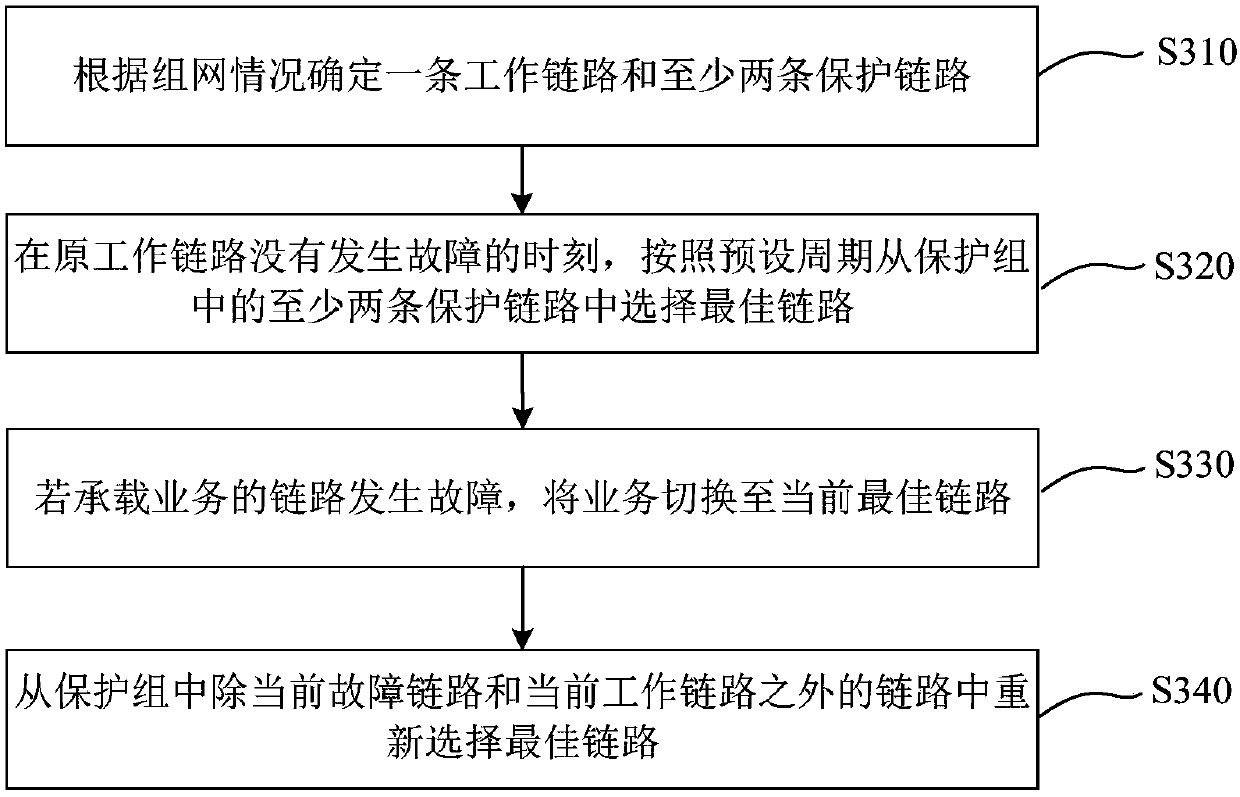
[0050] image 3 It is a flow chart of the full-mesh link protection method provided by Embodiment 1 of the present invention. This embodiment is applicable to the case of full-mesh topology link protection. The method can be implemented by a full-mesh link protection device To execute, the device may be implemented by software and / or hardware, and the device may be integrated into the core device. Specifically, the method may be performed by an ingress node on an LSP in each direction on the tunnel. Such as image 3 As shown, the method specifically includes the following steps:
[0051] S310. Determine one working link and at least two protection links according to networking conditions.
[0052] Among them, the networking situation includes the application scenario of the networking, the number of nodes in the networking, and physical link information. Establish a protection group between two nodes, such as between two PE (Provider Edge, network side edge) devices in the...
Embodiment 2
[0066] On the basis of the above-mentioned embodiments, this embodiment describes several situations of selecting the best link in the full-mesh link protection method.
[0067] (1) At the moment when no link fails or no link recovers from the failure, periodically select the best link from the links in the protection group except the current working link and the current failure link; wherein, the protection The group initially includes one working link and at least two protection links. That is, when no link fails or no link recovers from the failure, the selection of the best link is triggered when the preset period is reached.
[0068] (2) When a link fails, if the current working link fails, switch the service to the current best link so that the current best link is the current working link, and remove the current working link from the protection group The best link is selected from the links other than the failed link and the current failed link.
[0069] (3) When a li...
Embodiment 3
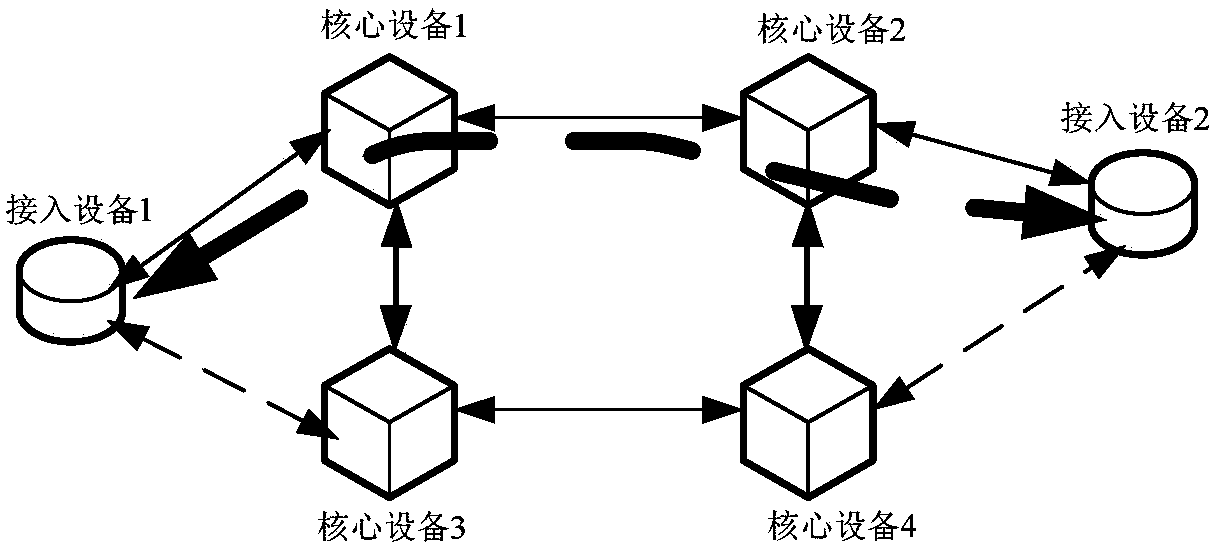
[0082] This embodiment provides a specific example of a full-mesh link protection method on the basis of the foregoing embodiments. by figure 2 The full mesh topology shown in the figure is taken as an example for illustration. The access device 1 communicates with the access device 2, and uses MPLS (Multi-Protocol Label Switching, Multi-Protocol Label Switching, Multi-Protocol Label Switching) OAM between the core devices to detect link connectivity.
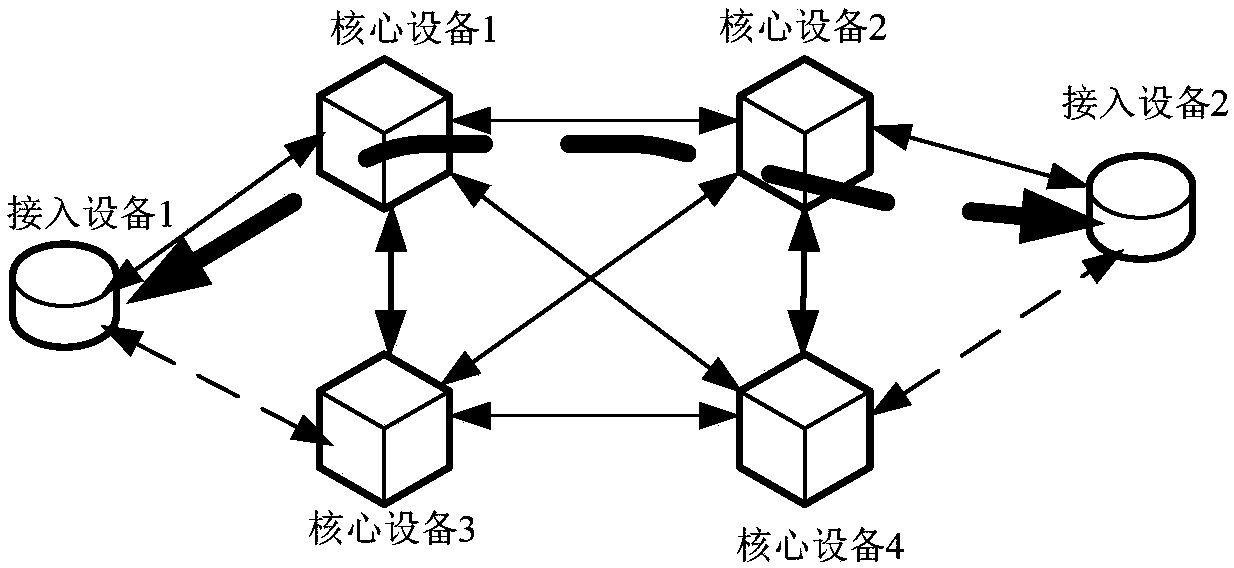
[0083] Such as Figure 4 As shown, it is a schematic diagram of a normal communication model of the core network, the ingress node of the LSP is the core device 1, and the egress node is the core device 4. Make sure the working link is core device 1->core device 4, and the four protection links are: core device 1->core device 2->core device 4, core device 1->core device 3->core device 4, core device 1->core device 3->core device 2->core device 4, core device 1->core device 2->core device 3->core device 4. That is, this emb...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com