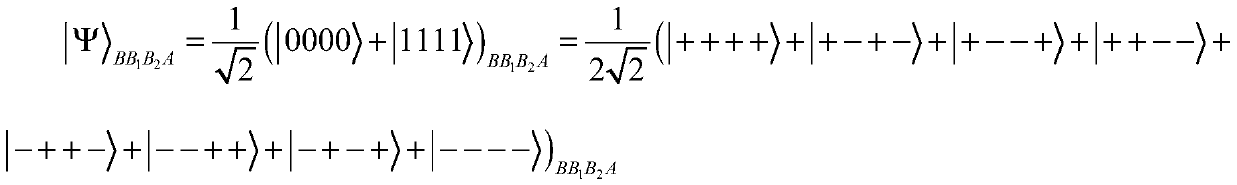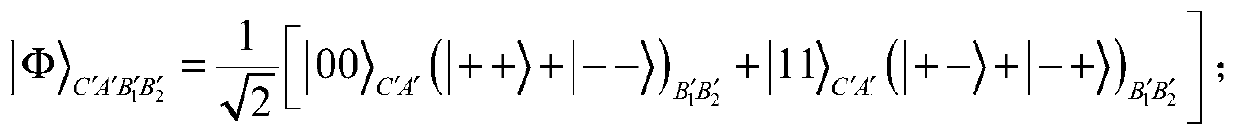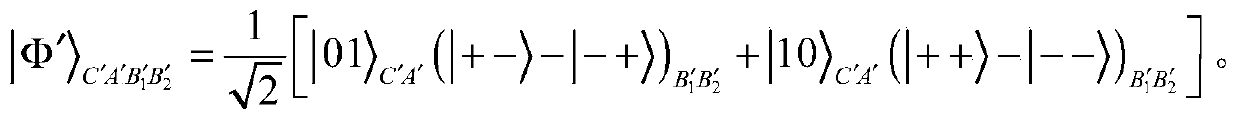Quantum agent blind signature method and system based on cluster state
A technology of proxy signature and proxy blindness, which is applied in transmission system, digital transmission system and key distribution, can solve the problem of low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0093] In this embodiment, a quantum proxy blind signature method based on the cluster state is disclosed. The method includes five communication parties, namely Alice, the message owner who holds the information to be signed, Bob, the initial signer who cannot sign normally, and the proxy The signer Bob1, the proxy signer Bob2, and the trusted receiver Charlie.
[0094] The quantum proxy blind signature scheme provided by the present invention includes 5 legal communication parties. Alice is the message owner, and her document needs to be signed by the initial signer, Bob. However, Alice wants Bob to be ignorant of the contents of her file, i.e. to achieve blindness in the signature scheme. If Bob is unable to complete the signing of Alice's initial message for some reason at this time, Bob can authorize the proxy signer group (Bob1 and Bob2) to perform the signature on his behalf during Bob's absence. Two proxy signers, Bob1 and Bob2, obtain proxy credentials from Bob. On...
Embodiment 2
[0191] Based on the method in Embodiment 1, this embodiment discloses a cluster state-based quantum proxy blind signature system for implementing the method in Embodiment 1. The system includes Alice, the message owner who stores the information to be signed, and cannot normally Signed initial signer Bob, proxy signer Bob1, proxy signer Bob2, and trusted receiver Charlie.
[0192] The message owner Alice, the initial signer Bob, the proxy signer Bob1, the proxy signer Bob2 and the trusted receiver Charlie are used to realize the following functions:
[0193] (I) The initial signer Bob distributes the key to the message owner Alice and the initial signer Bob through the four-particle GHZ state sequence, and the message owner Alice obtains the key k A , the initial signer Bob obtains the key k B ;
[0194] Proxy signer Bob1 and proxy signer Bob2 obtain keys through the quantum key distribution protocol
[0195] Optionally, the initial signer Bob distributes the key to the m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com