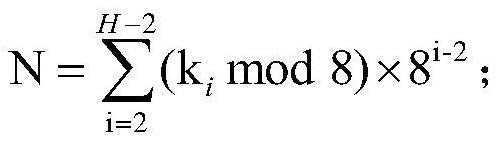A Steganographic Encoding Method for Low-Disturbance Information Security Based on Chinese Remainder Theorem
A technology of Chinese remainder theorem and information security, applied in the field of information steganography, which can solve the problems of image redundancy, inability to improve, and limited single-pixel embedding capacity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the implementation examples described here are only for illustration and explanation of the present invention, and are not intended to limit this invention.
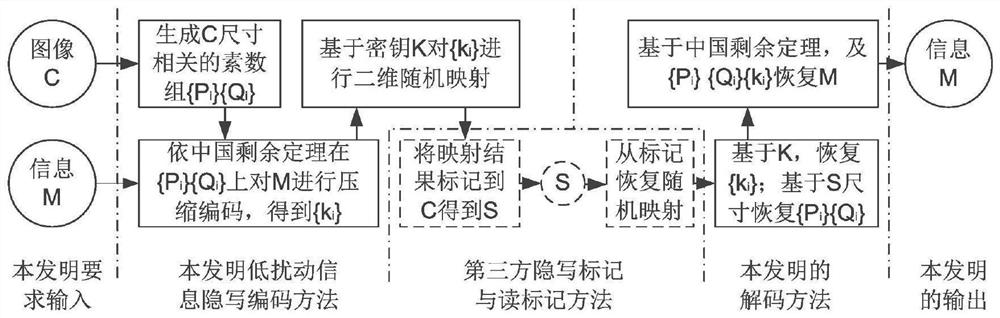
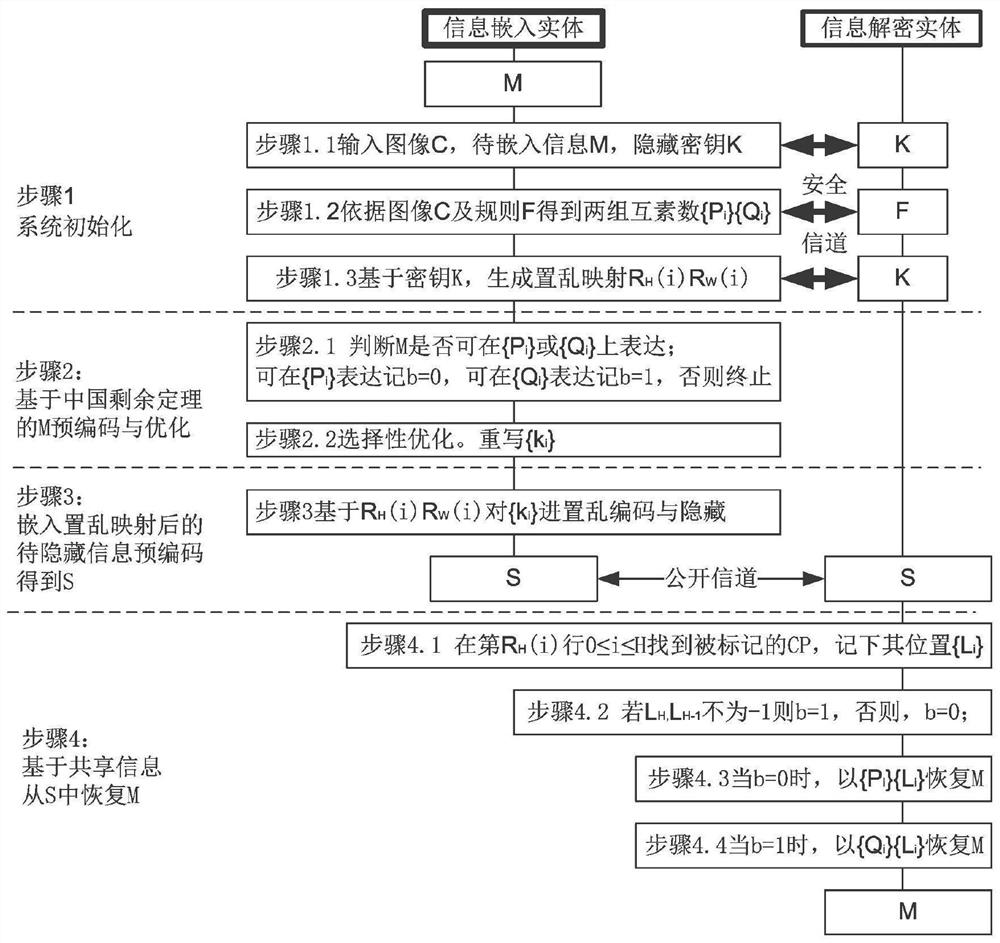
[0050] The present invention provides a low-disturbance information security steganographic encoding method based on the Chinese remainder theorem. For the convenience of description, an image is regarded as a pixel matrix, and the monochrome component of each pixel in the pixel matrix is denoted as CP. For example, the CP description can be applied to grayscale image pixels, and monochrome components of RBG images. The original CP matrix used for information hiding is denoted as Cover image, referred to as C; the CP matrix obtained after hiding inform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com