Anti-counterfeiting method and system of two-dimensional code for tracing
A technology of two-dimensional codes and users, which is applied in the anti-counterfeiting method and system field of two-dimensional codes for traceability, and can solve the problems that barcode technology does not have anti-counterfeiting capabilities, negatively affects the credibility of product quality traceability systems, and cannot meet traceability requirements, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
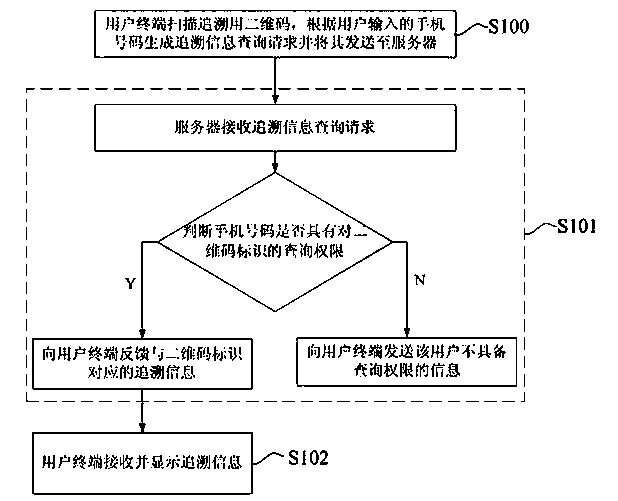
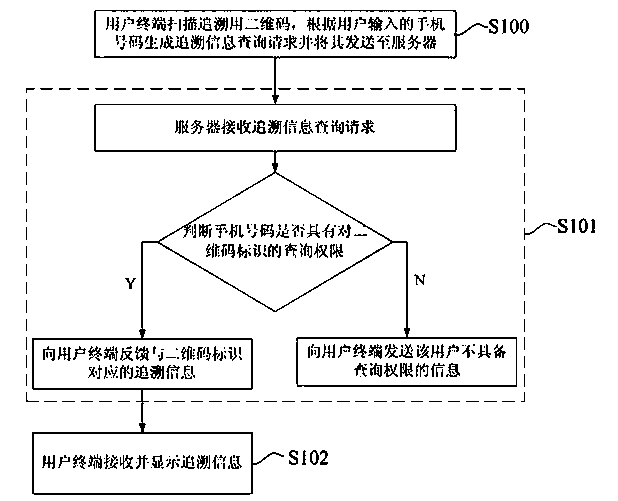
[0034] refer to figure 1 , in the query stage of traceability information, the anti-counterfeiting method of the traceability two-dimensional code of the present invention comprises:
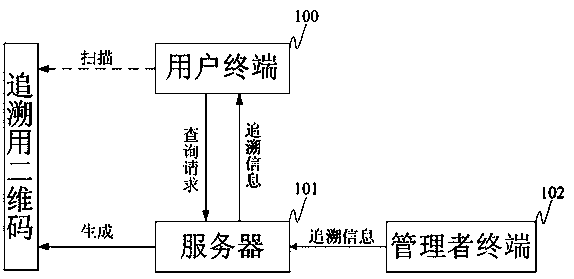
[0035] S100. The user terminal scans the two-dimensional code for traceability, generates a traceability information query request according to the mobile phone number input by the user, and sends it to the server.
[0036] Among them, the traceability information inquiry request carries the QR code identification and the mobile phone number. The user terminal can be a smart terminal with a camera such as a smart phone, a smart tablet, etc. In practical applications, the QR code for traceability can be scanned using the existing WeChat, QQ and other APPs of the user terminal; the QR code can be a QR Code , it can also be a Chinese Sensible code, or a two-dimensional code generated by other technologies.
[0037] For the generation process of the traceability QR code, it specifically includes: ...
Embodiment 2
[0043] Based on the methods disclosed in the above embodiments, after the server determines that the mobile phone number in the request has the query authority for the two-dimensional code identification in the request, before feeding back the traceability information corresponding to the two-dimensional code identification to the user terminal, the server may also include the following steps:
[0044] S200. The server sends a dynamic SMS password to the user terminal after determining that the mobile phone number in the request has the right to query the two-dimensional code identifier in the request.
[0045] S201. The user terminal receives the dynamic SMS password, and sends the input dynamic password to the server.
[0046] Specifically, after the user terminal receives the dynamic SMS password, the user can check it by himself and input the dynamic password at a designated location, or the associated program can automatically detect and analyze the received dynamic SMS pa...
Embodiment 3
[0051] Based on the methods disclosed in the above embodiments, the traceability registration and authorization mentioned in Embodiment 1 will be described in detail. Specifically, the traceability registration and authorization process includes the following steps:
[0052] Step S300, the user terminal or the manager terminal scans the QR code for traceability, and sends a new user authorization registration request to the server.
[0053] Among them, the new user authorization registration request carries the new user mobile phone number and the authorization QR code identification.
[0054] Step S301, the server receives the new user authorization registration request, stores the new user's mobile phone number in the user authorization registration database, and includes the authorized QR code identifier into the scope of authority of the new user's mobile phone number, and completes the new user authorization registration operation.
[0055] It should be noted that the reg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com