Adaptive binary search algorithm for malicious user positioning in smart grid neighboring network
A binary search algorithm and malicious user technology, applied in the field of adaptive binary search algorithm, can solve the problems of high deployment cost and long detection time, and achieve the effect of shortening the detection time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be further described in detail below in conjunction with the embodiments.
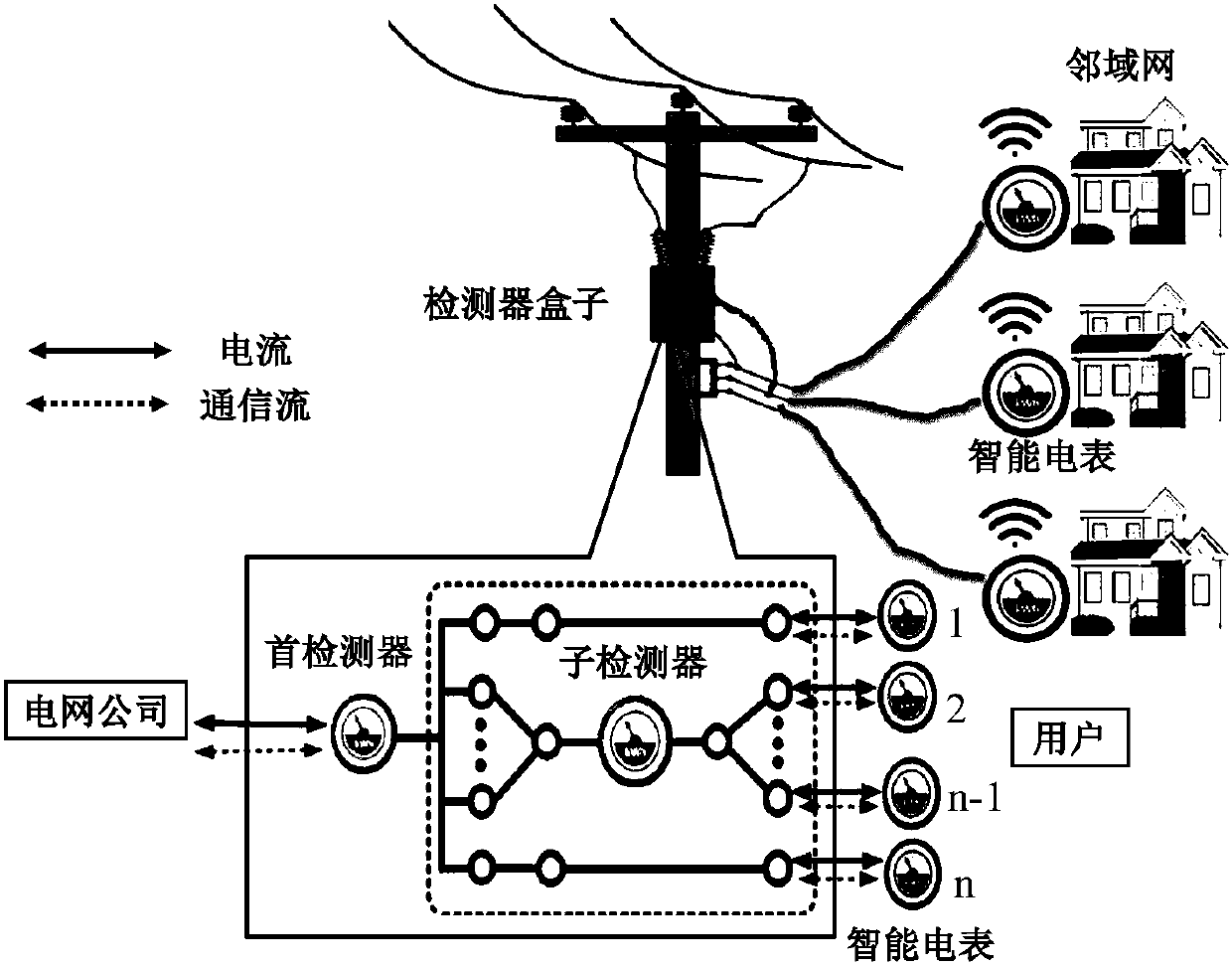
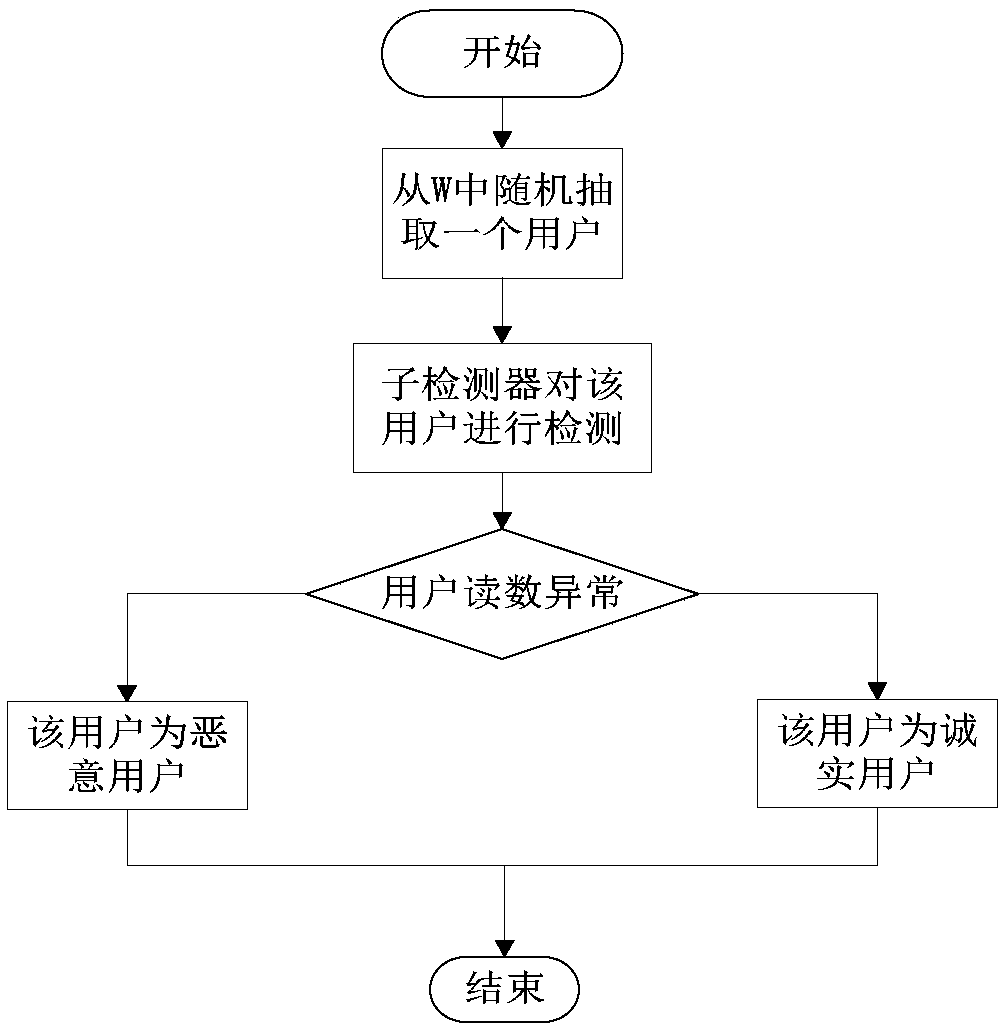
[0040] The main feature of this method is to first estimate the maximum value of malicious users in the neighborhood network; in the search process, the detector adaptively adapts to the relationship between the number of malicious users that have been detected and the total number of users still to be detected. Adjust the search strategy. Its search strategy includes one-by-one search strategy and binary search strategy. When the one-by-one search strategy is adopted, the detector detects only one user at a time; when the binary search strategy is adopted, the detector detects multiple users at the same time, and the number of detected users is determined by the number of malicious users that have been detected and the users that still need to be detected. The number is decided together.
[0041] An adaptive binary search algorithm for locating malicious users in smart g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com