Block chain construction method
A construction method and blockchain technology, applied in the field of information security, can solve problems such as transaction speed, security doubts, trust concentration, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
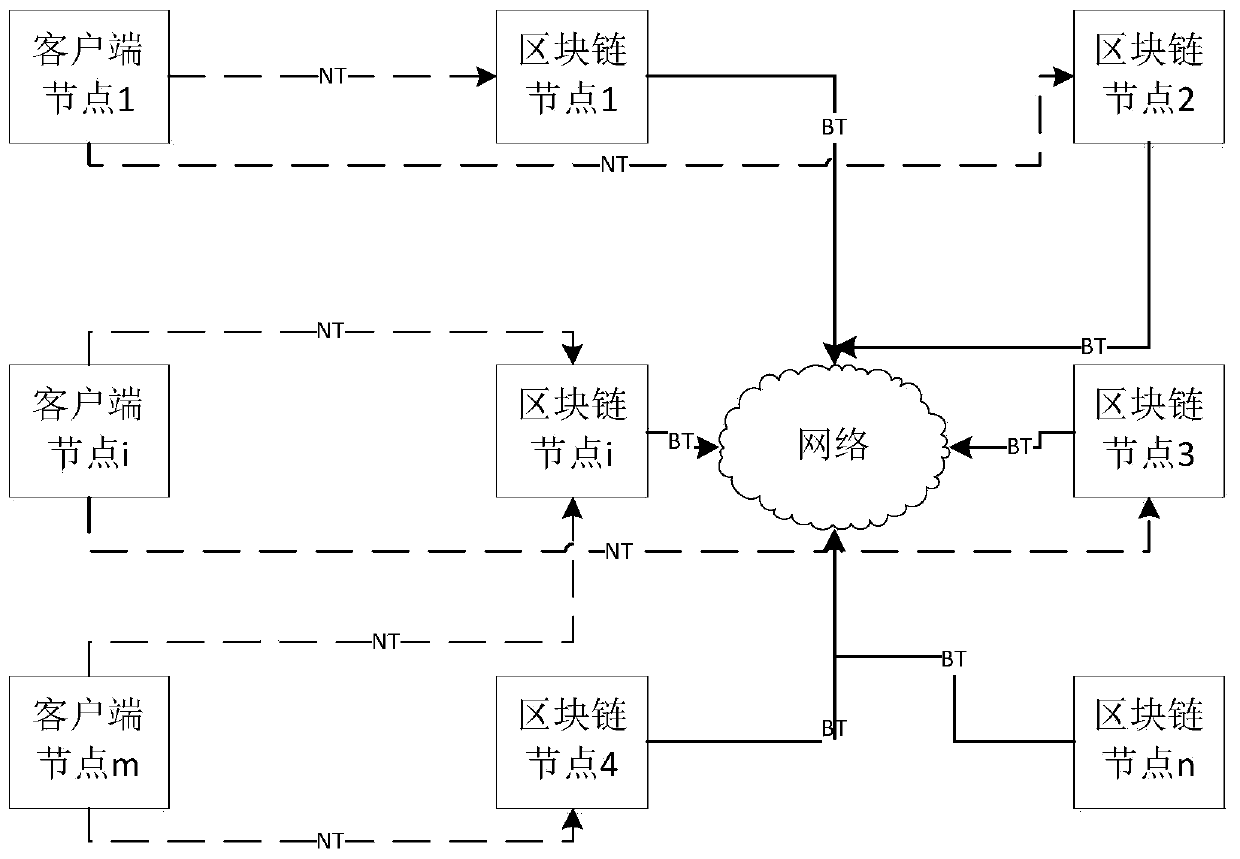
[0085] 1. This embodiment is a public chain scenario, set NS=2, T=60, NC=10, D=2, NL=NC, α=0.6, β=0.6, NR=2, DT 0 =DT 1 =3, set the network to P2P (point-to-point) network, DL=3 seconds.
[0086] 1) In this embodiment, each computing device acts as a client node and a blockchain node at the same time, and the number of computing devices is far greater than 10. Each computing device includes various modules specified in the present invention. The user of each computing device completes the distribution of the original rights and interests through an off-chain platform such as Ethereum, which is mapped to this embodiment and stored in their respective accounts in the state database.
[0087] The total equity of the public chain is included in the genesis transaction, which also includes the default all 0 Merkel roots, the list of active blockchain nodes of generation 0, the start time of the generation, the period and other information.
[0088] After the blockchain node is running, i...
Embodiment 2
[0107] This embodiment is a consortium chain scenario, set NS=2, T=360, NC=10, D=2, NL=NC, α=0.9, β=0.9, NR=2, DT 0 =DT 1 =1, set the network as the multicast network realized by the multicast group, DL=1 second. We set T=360 because the basic assumption in the consortium chain scenario is that nodes occasionally fail and the list of blockchain nodes changes slowly.
[0108] The execution process of the second embodiment is the same as that of the first embodiment, the only difference is that the above-mentioned set parameters are used for the specific parameters, and the values related to the specific parameters in each implementation step will correspondingly change.
Embodiment 3
[0110] This embodiment adopts the parameter setting of the public chain, and the execution process is the same as that of embodiment 1, except that the weight of the node in the current active blockchain list is a value proportional to the node equity, which is equal to the node equity; customer When the terminal selects an active blockchain node to send NT, if it knows the equity of each node, it selects in the order of equity, otherwise it is selected randomly; the weight threshold is equal to the product of the total equity of the current active blockchain node and the security parameter α.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com