Method and device for monitoring unknown program exception request and electronic device
A program request, program exception technology, applied in the protection of internal/peripheral computer components, platform integrity maintenance, etc., can solve the problems of file-level monitoring unable to capture, no solution found, etc., to achieve stable operation, low false positive rate, good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
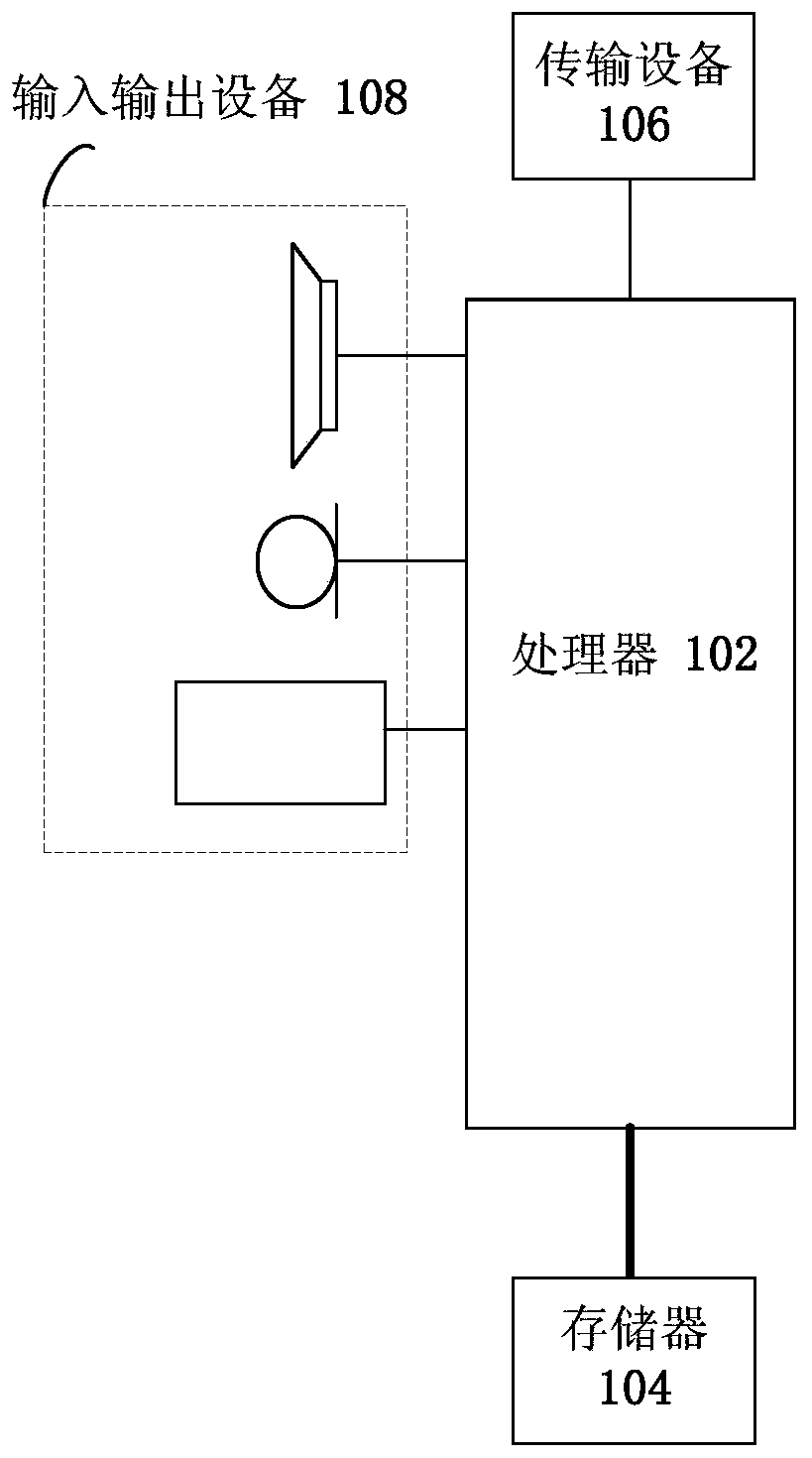
[0024] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer device, a server or a similar computing device. Taking running on computer equipment as an example, figure 1 It is a hardware structural block diagram of a computer device according to an embodiment of the present invention. like figure 1 As shown, the computer equipment may include one or more ( figure 1 Only one is shown in the figure) a processor 102 (the processor 102 may include but not limited to a processing device such as a microprocessor MCU or a programmable logic device FPGA) and a memory 104 for storing data. Optionally, the above-mentioned computer equipment is also A transmission device 106 for communication functions as well as input and output devices 108 may be included. Those of ordinary skill in the art can understand that, figure 1 The shown structure is only for illustration, and it does not limit the structure of the above ...
Embodiment 2
[0059] In this embodiment, a control device for opening a file is also provided, which is used to implement the above embodiments and preferred implementation modes, including a client, a server, etc., which have already been described and will not be repeated. As used below, the term "module" may be a combination of software and / or hardware that implements a predetermined function. Although the devices described in the following embodiments are preferably implemented in software, implementations in hardware, or a combination of software and hardware are also possible and contemplated.
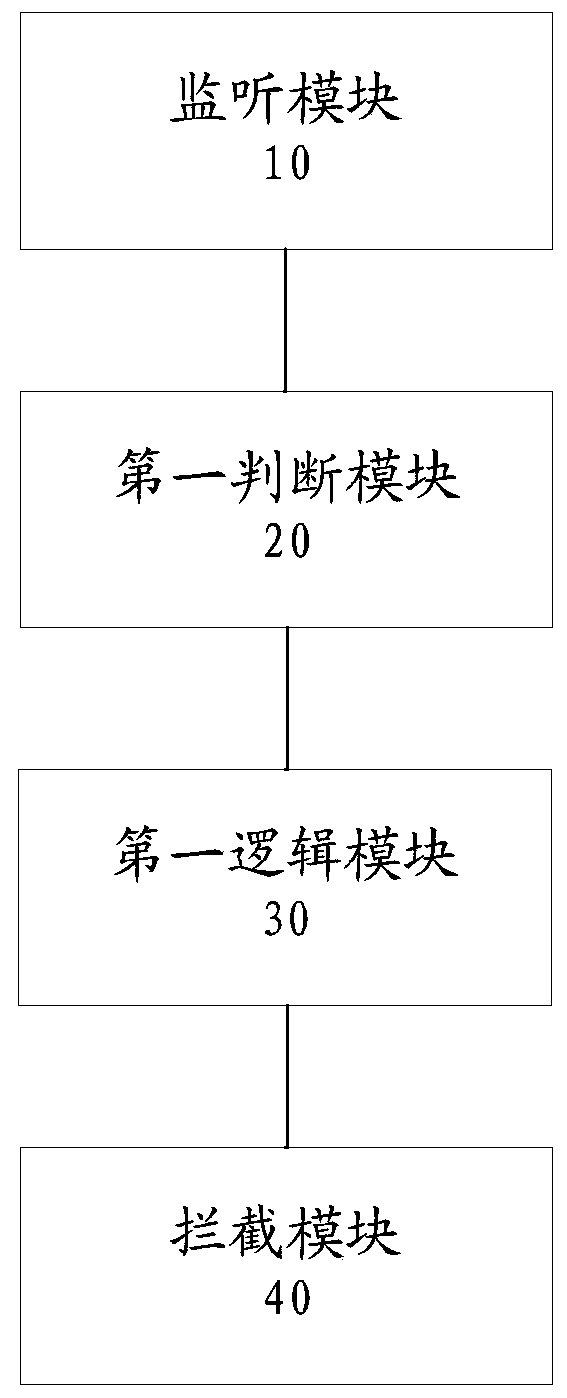
[0060] image 3 is a structural block diagram of an optional control device for opening files according to an embodiment of the present invention, such as image 3 As shown, the device includes: a monitoring module 10 , a first judging module 20 , a first logic module 30 and an intercepting module 40 .
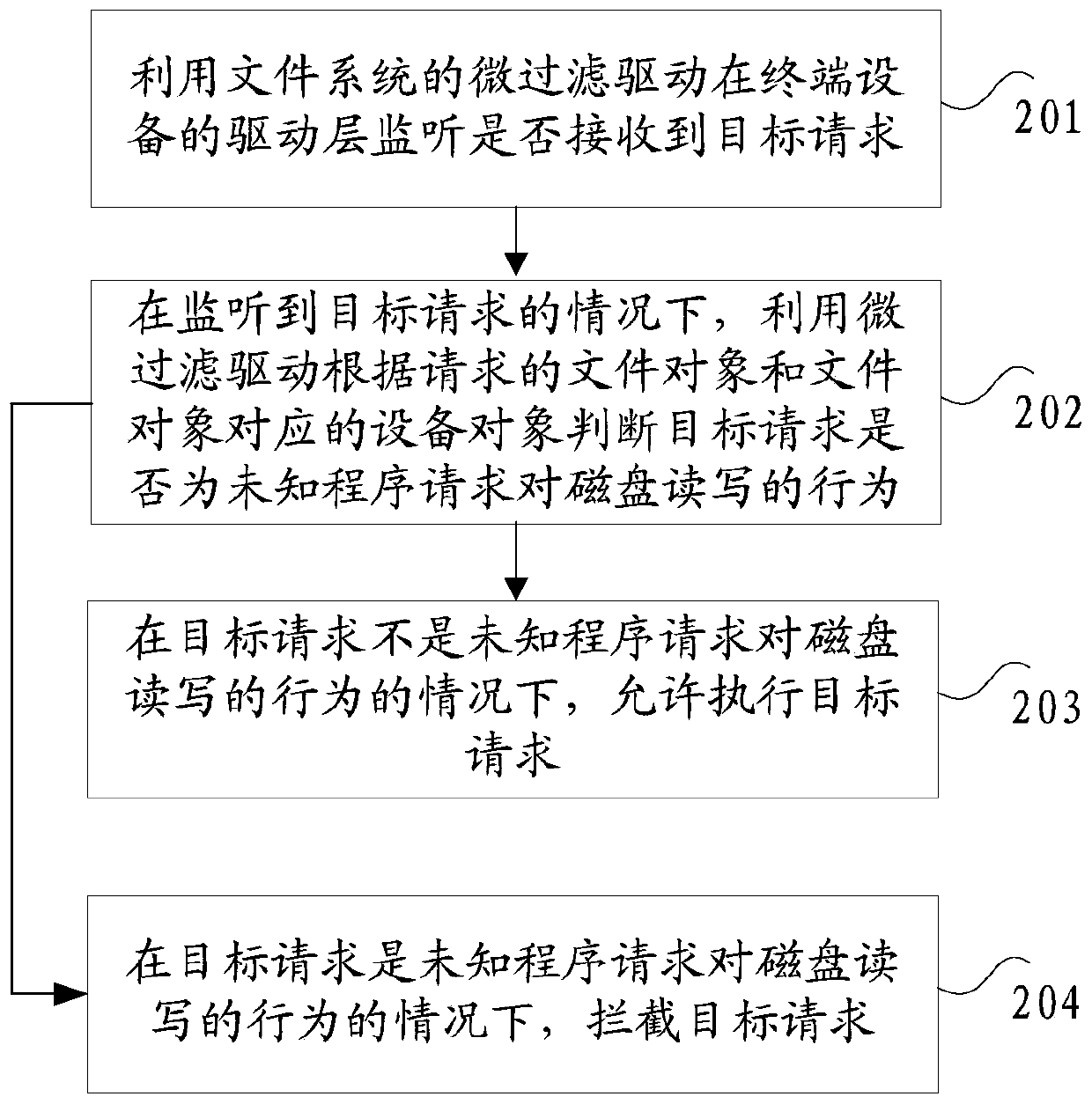
[0061]Wherein, the monitoring module is used to utilize the microfilter driver of the fi...
Embodiment 3
[0071] An embodiment of the present invention also provides a storage medium, in which a computer program is stored, wherein the computer program is set to execute the steps in any one of the above method embodiments when running.
[0072] Optionally, in this embodiment, the above-mentioned storage medium may include but not limited to: U disk, read-only memory (Read-Only Memory, ROM for short), random access memory (Random Access Memory, RAM for short), Various media that can store computer programs, such as removable hard disks, magnetic disks, or optical disks.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com