Device of using intelligent switching of multiple domain names for DDoS (Distributed Denial of Service) attack defence
A technology of intelligent switching and domain name, applied in electrical components, transmission systems, etc., can solve problems such as business interruption, continuous attack, and high cost, and achieve the effects of reducing impact, increasing attack threshold, and increasing cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
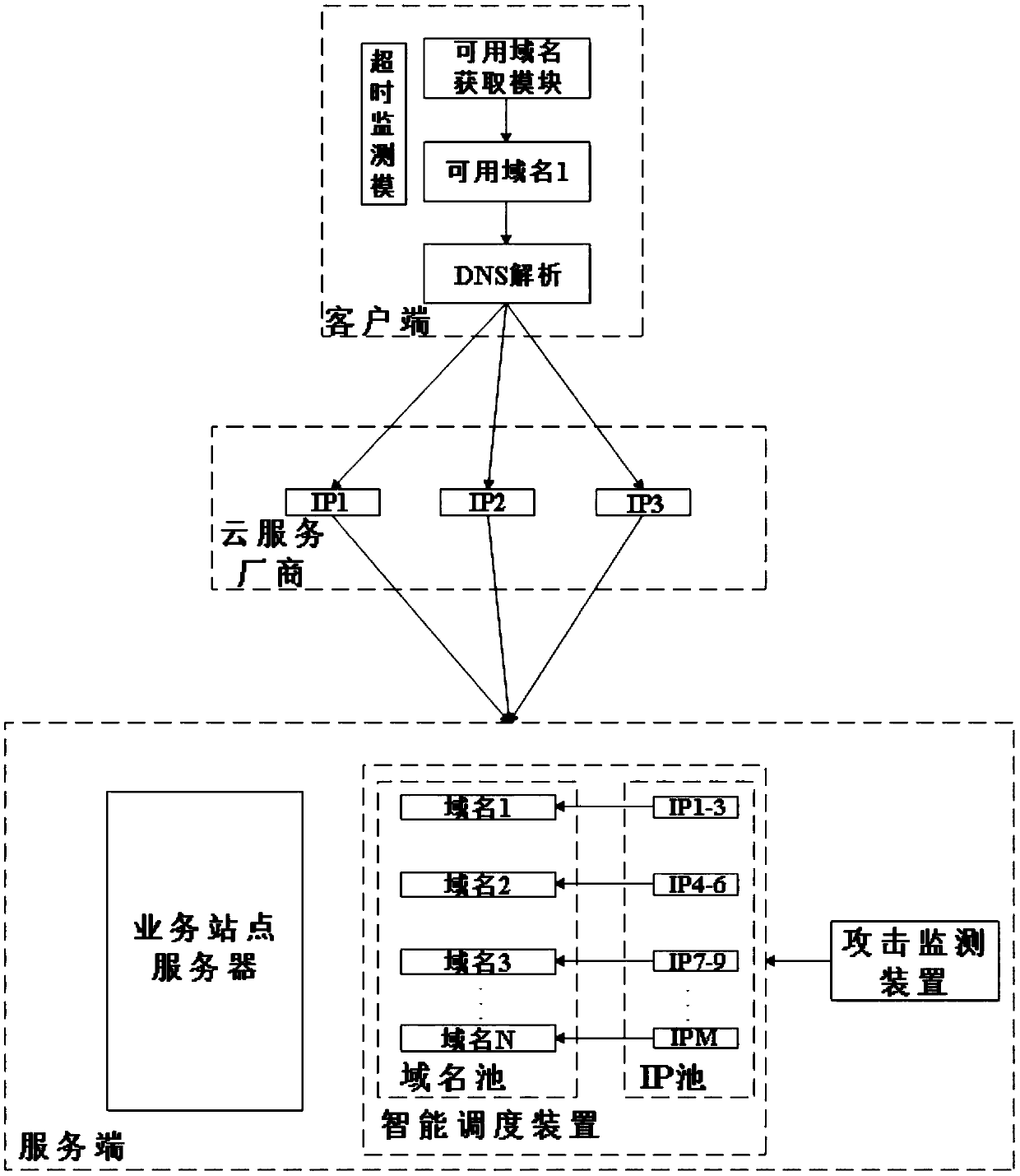
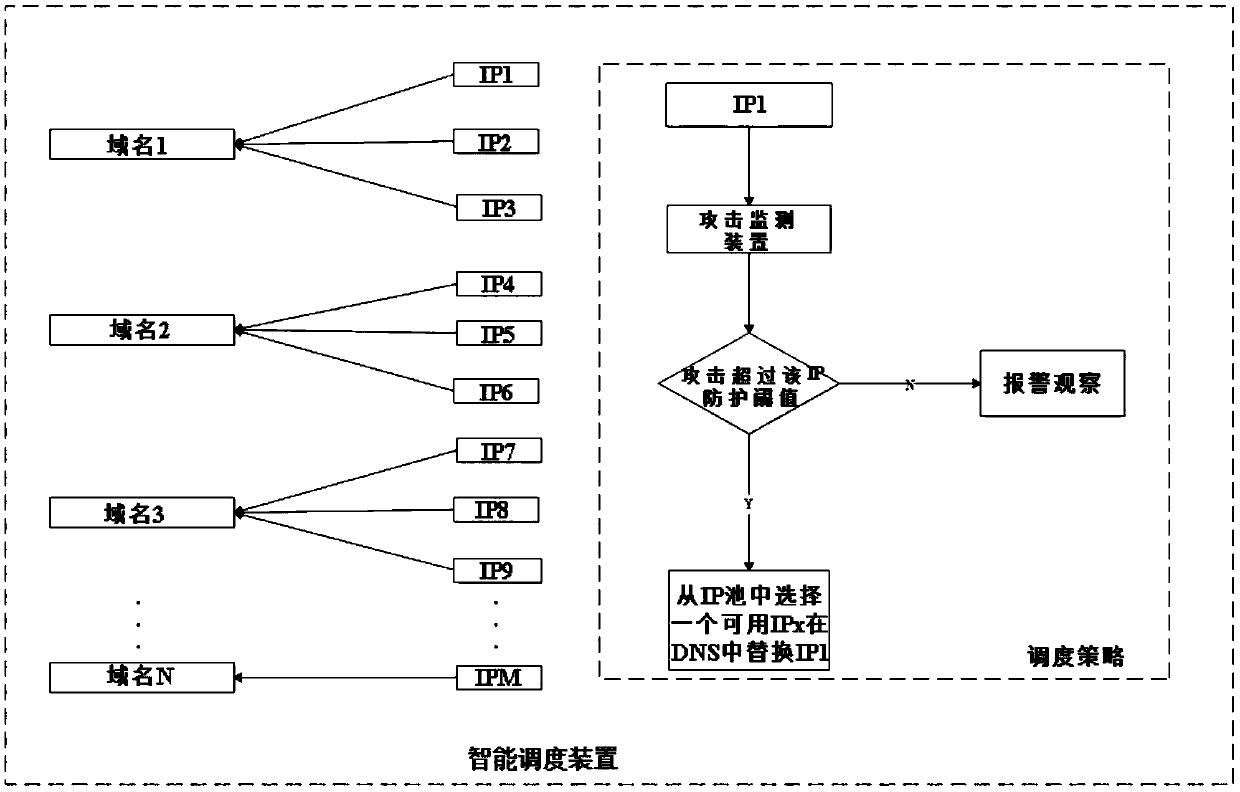
[0022] Such as figure 1 As shown, a device for preventing DDoS attacks by intelligently switching multiple domain names includes a domain name acquisition module and a timeout monitoring module arranged on the client side, and also includes an attack monitoring device and an intelligent scheduling device arranged on the server side;
[0023] Domain name acquisition module: obtain at least two available domain names from the available domain name pool of the server-side intelligent scheduling module every T time, one of which is used as the currently used domain name, and the rest are used as standby domain names;
[0024] At the same time, the domain name acquisition module can be protected by the client's own security reinforcement and communication encryption measures to prevent available domain names from being traversed.
[0025] Timeout m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com