Data encryption method and device, and data decryption method and device
A data encryption and data decryption technology, applied in the field of data processing, can solve the problems of easy cracking of encrypted information, easy leakage of fixed keys, and reducing the security of information transmission, and achieve the effect of increasing the difficulty of cracking and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0076] see figure 2 , shows a schematic flowchart of a data encryption method in the embodiment of the present application. In this embodiment, applied to the first device, the method may include the following steps, for example:
[0077] Step 201: Generate service request data, a first random number, a second random number and service request parameters based on a service request to a second device.
[0078] It can be understood that, in a scenario where the service request of the first device to the second device has privacy and needs to be kept secret, the service request data corresponding to the service request needs to be encrypted. Due to the use of fixed key encryption methods such as traditional symmetric keys or asymmetric keys, it is easy for attackers to attack the fixed keys stored on the device side to decipher the encrypted service request data. The stored dynamic key encryption method. Considering that business requests have corresponding business request p...
Embodiment 2
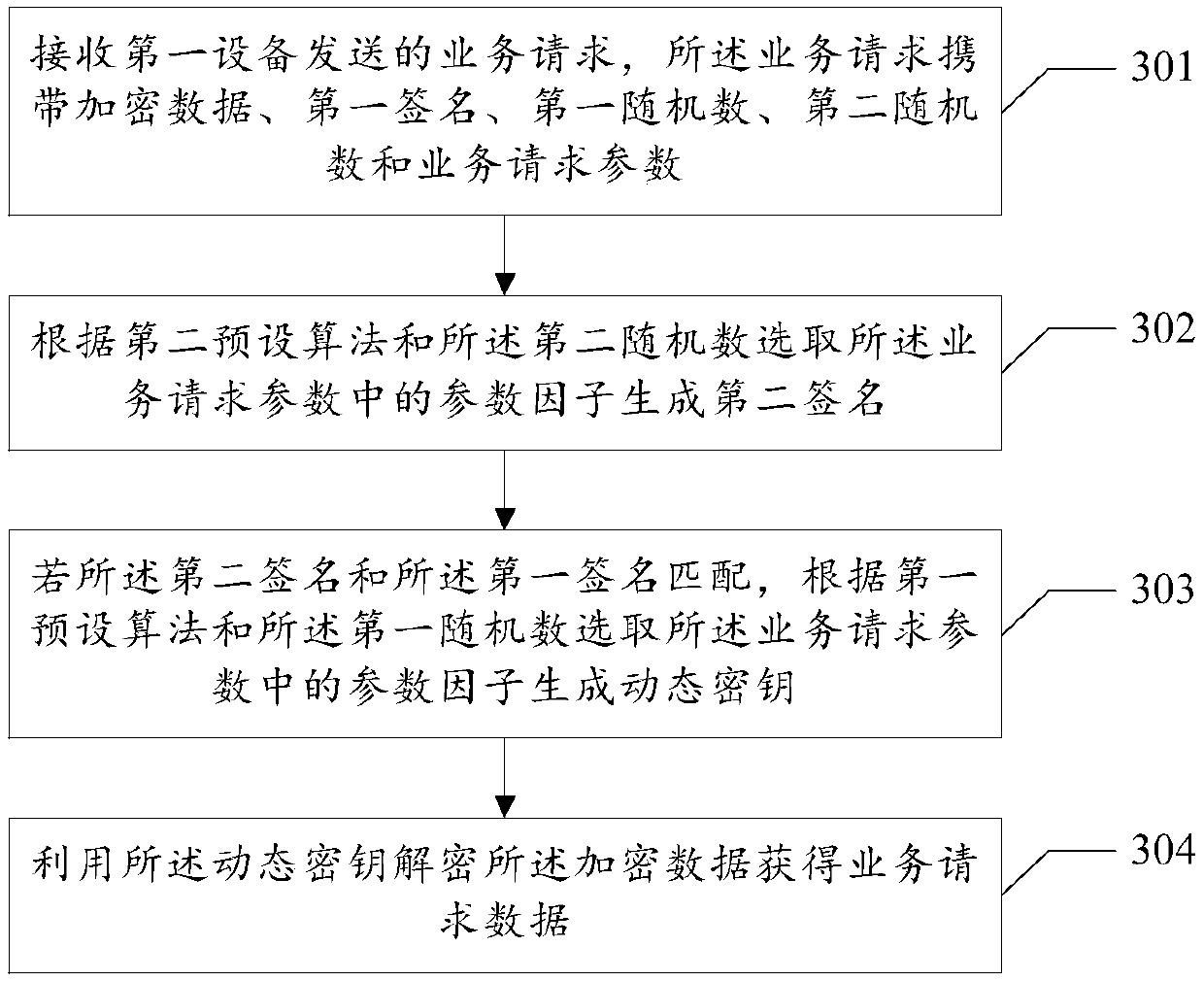
[0096] see image 3 , shows a schematic flowchart of another data decryption method in the embodiment of the present application. In this embodiment, applied to the second device, the method may include the following steps, for example:
[0097] Step 301: Receive a service request sent by a first device, where the service request carries encrypted data, a first signature, a first random number, a second random number and service request parameters.
[0098] Based on the above description of the service request parameters generated by the first device corresponding to the service request, the service request parameters received by the second device and sent by the first device are the same as above. Therefore, in some implementations of the embodiments of the present application, the service request parameter includes at least the first device identifier or one other service request parameter.
[0099] It should be noted that, based on the above description of the first prese...
Embodiment 3
[0112] see Figure 4 , which shows a schematic flowchart of another data encryption and data decryption method in the embodiment of the present application. In this embodiment, the method may include the following steps, for example:
[0113] Step 401: The first device generates service request data, a first random number, a second random number and service request parameters based on a service request to the second device.
[0114] Step 402: The first device selects the parameter factor in the service request parameter according to the first preset algorithm and the first random number to generate a dynamic key; and selects the parameter factor in the service request parameter according to the second preset algorithm and the second random number Generate the first signature.
[0115] Step 403: the first device uses the dynamic key to encrypt the service request data to generate encrypted data.
[0116] Step 404: the first device sends a service request to the second device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com