Color JPEG image format-compliant encryption and decryption method
An encryption method and image technology, applied in image communication, electrical components, etc., can solve problems such as insufficient security protection, privacy leakage, and no composite encryption system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
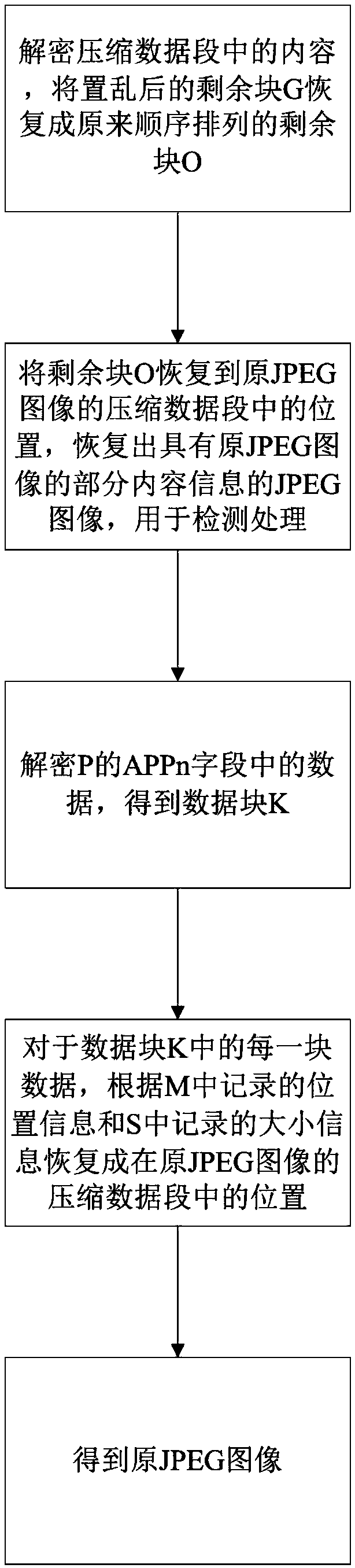
[0052] A format-compatible encryption method for color JPEG images such as figure 1 , including the following steps:
[0053] S1: Determine the size L of the block T to be extracted T ;
[0054] S2: select the ROI block from the compressed data segment of the original JPEG image, and re-select the ROI block or add random blocks to the ROI block according to the size relationship between the ROI block and T to make the ROI block equal to the size of T;
[0055]S3: Perform RC4 encryption on the block obtained in S2 to form an encrypted block;
[0056] S4: scrambling and rearranging the remaining blocks in the compressed data segment of the original JPEG image;
[0057] S5: reorganize the encrypted block generated by S3 and the scrambled rearranged block in S4 into an encrypted JPEG image with compatible format;
[0058] S6: Restoring the image or decrypting the image.
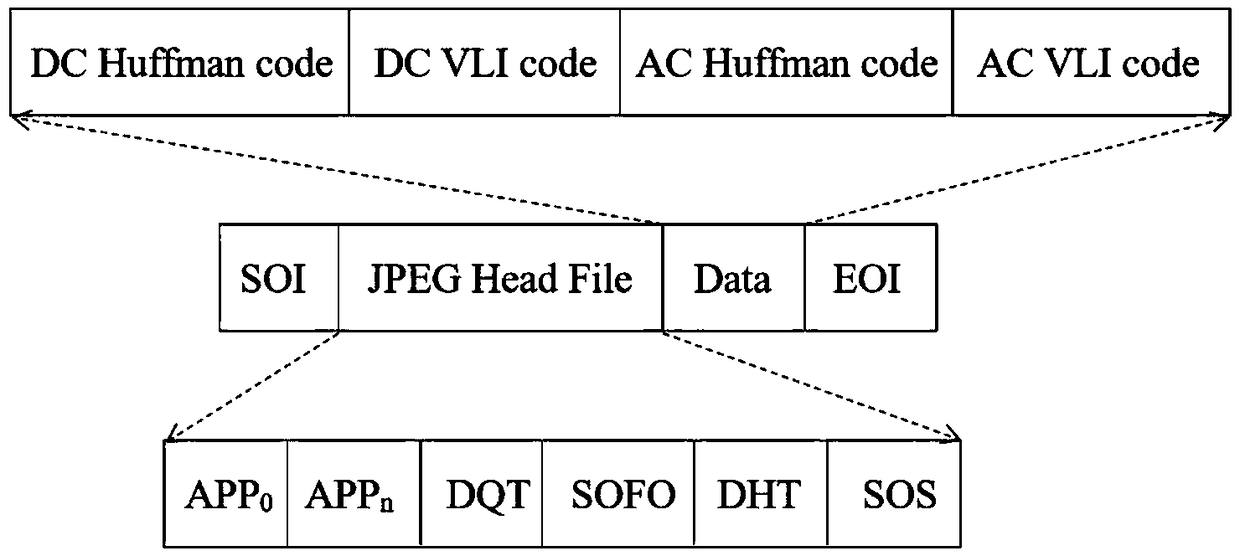
[0059] In the specific implementation process, the format of the JPEG image file is as follows image 3 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com