Container-based cluster safety management method
A security management and cluster technology, applied in the field of container-based cluster security management, to prevent malicious damage to host resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
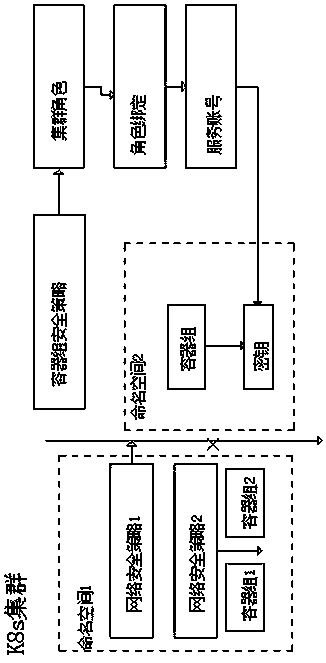
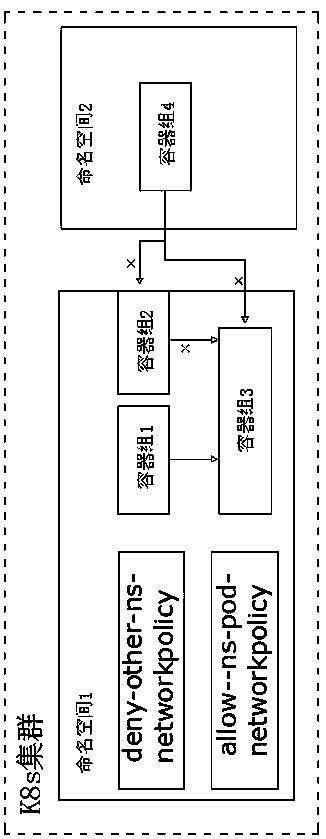
[0058] as attached figure 1 As shown, the cluster K8S has two security policies, Networkpolicy: network security policy and PodSecurityPolicy: container group security policy;
[0059] The network security policy is used to isolate the network of the namespace, and can also isolate the network of the container group within the namespace;
[0060] The container group security policy is used to define whether the containers in the container group can access the host machine resources. In order to ensure the security of the cluster nodes, except for the K8S system-level namespace, container groups in other namespaces are not allowed to access the host machine’s network, System configuration and other information.
[0061] A container group security policy (PSP) is a system resource that is managed through a cluster role and bound to a service account in a specific namespace through the role. The container group obtains the highest authority to operate the host through the servic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com