Privacy protection method and a privacy protection system for triangular data publishing in a graph
A privacy protection and data publishing technology, applied in digital data protection, electronic digital data processing, instruments, etc., to achieve the effect of protecting privacy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
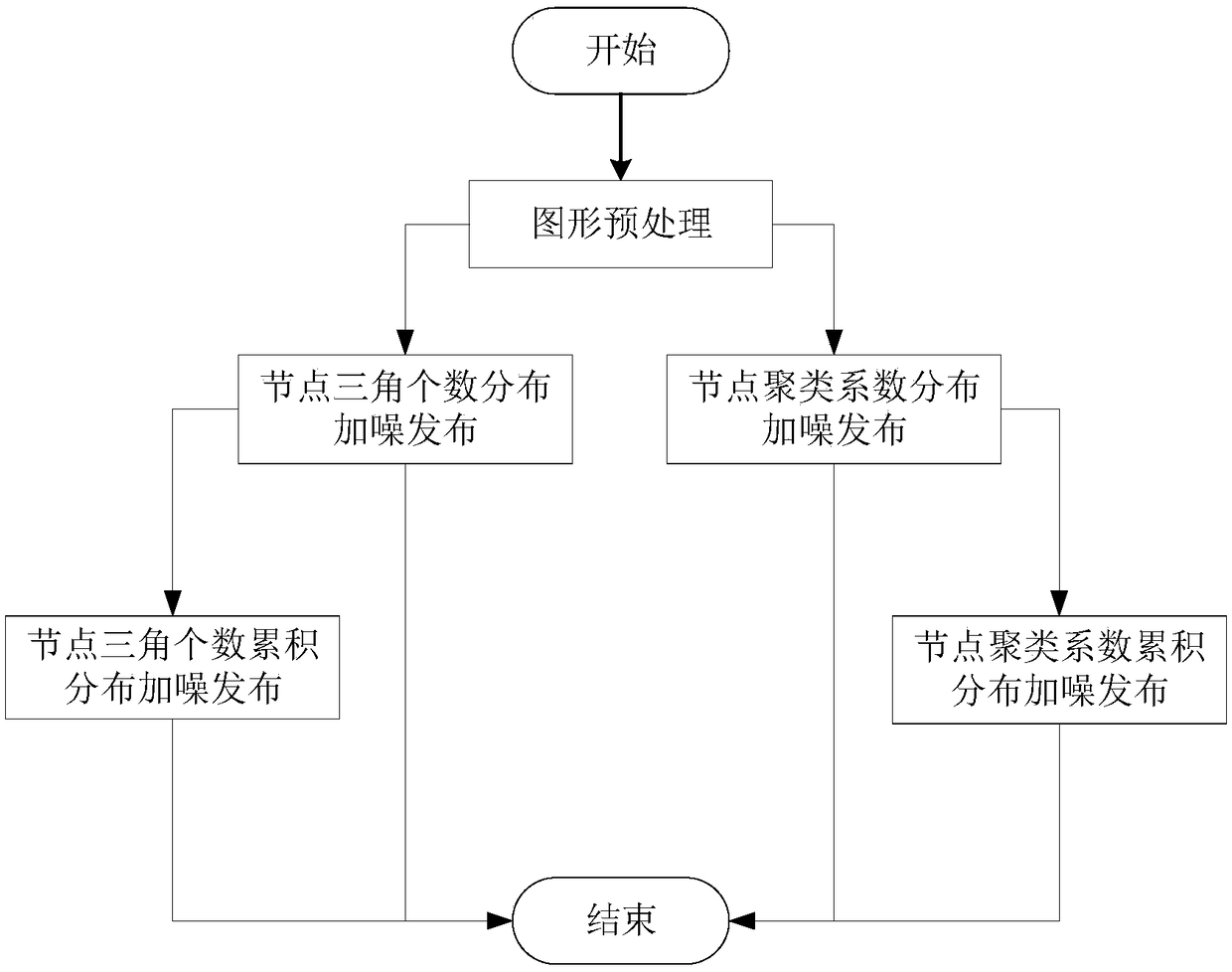
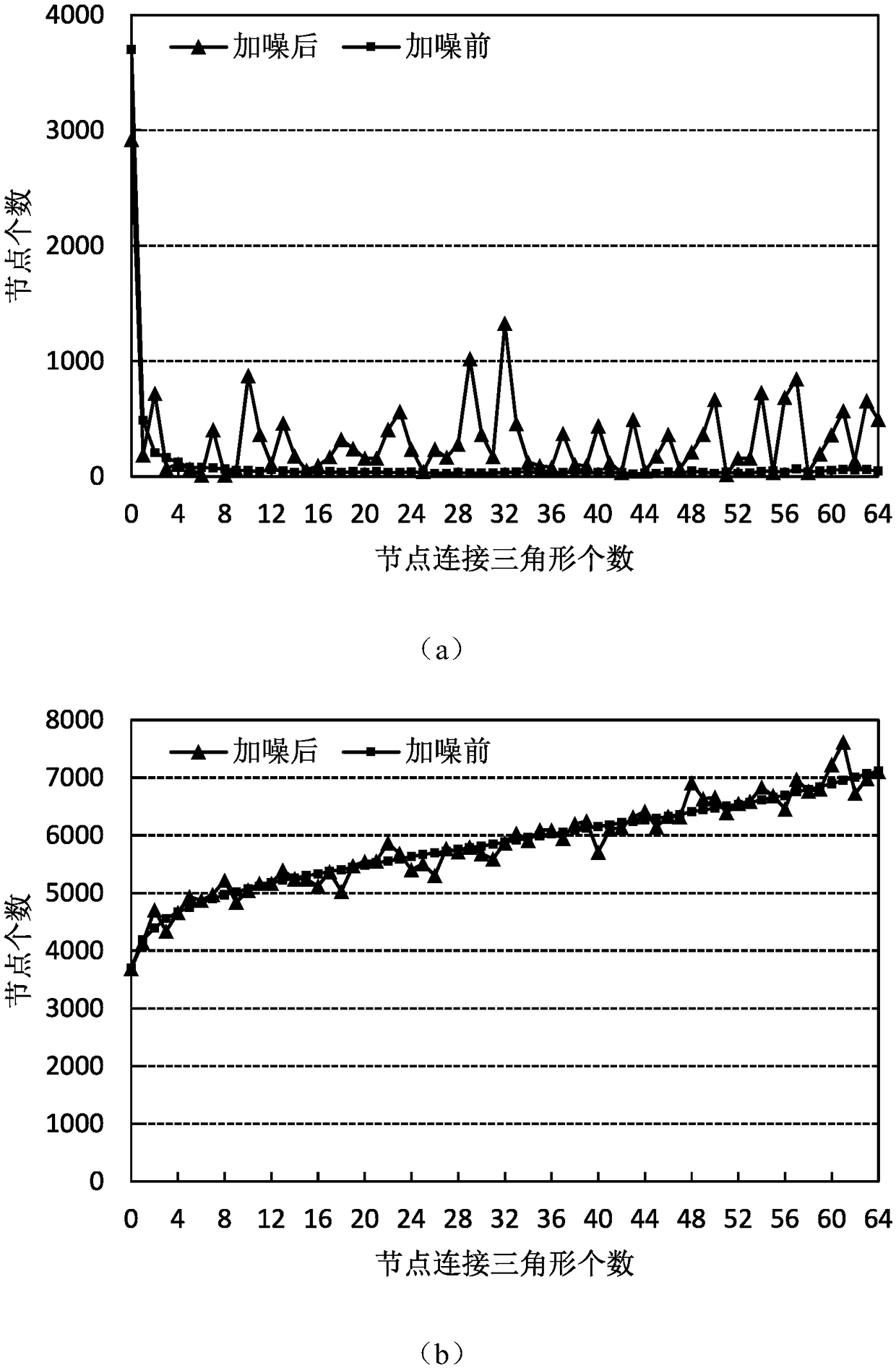
[0065] The graph preprocessing step achieves the purpose of deleting the triangles connected by nodes larger than the preset threshold by deleting part of the connected edges of the nodes. It aims to reduce the global sensitivity by reducing the maximum number of triangles connected to the nodes, thereby reducing the node difference. The amount of noise to add for privacy. The specific implementation method comprises the following steps:
[0066] (1.1) Count the number of triangles connected to each node, denoted as Tri i (G), where the subscript i represents the current node number, and G represents the currently active graph;
[0067] (1.2) Count the number of nodes connected to each node, denoted as Deg i (G);
[0068] (1.3) Record each node v i The sequence of neighbor nodes is LinkNode(v i );
[0069] (1.4) Traverse all nodes and judge the current node v i The number of connected triangles Tri i (G) Whether it is greater than the preset threshold λ, if Tri i (G)>...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com