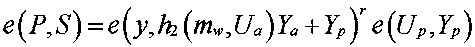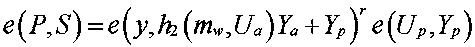General Composable Identity Proxy Signcryption Method
A technology of proxy signcryption and signcryption party, which is applied in the field of public key cryptography or general composable security framework or proxy signcryption, can solve the problem of proxy signcryption without identity, and achieve low computational complexity and universal composable security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
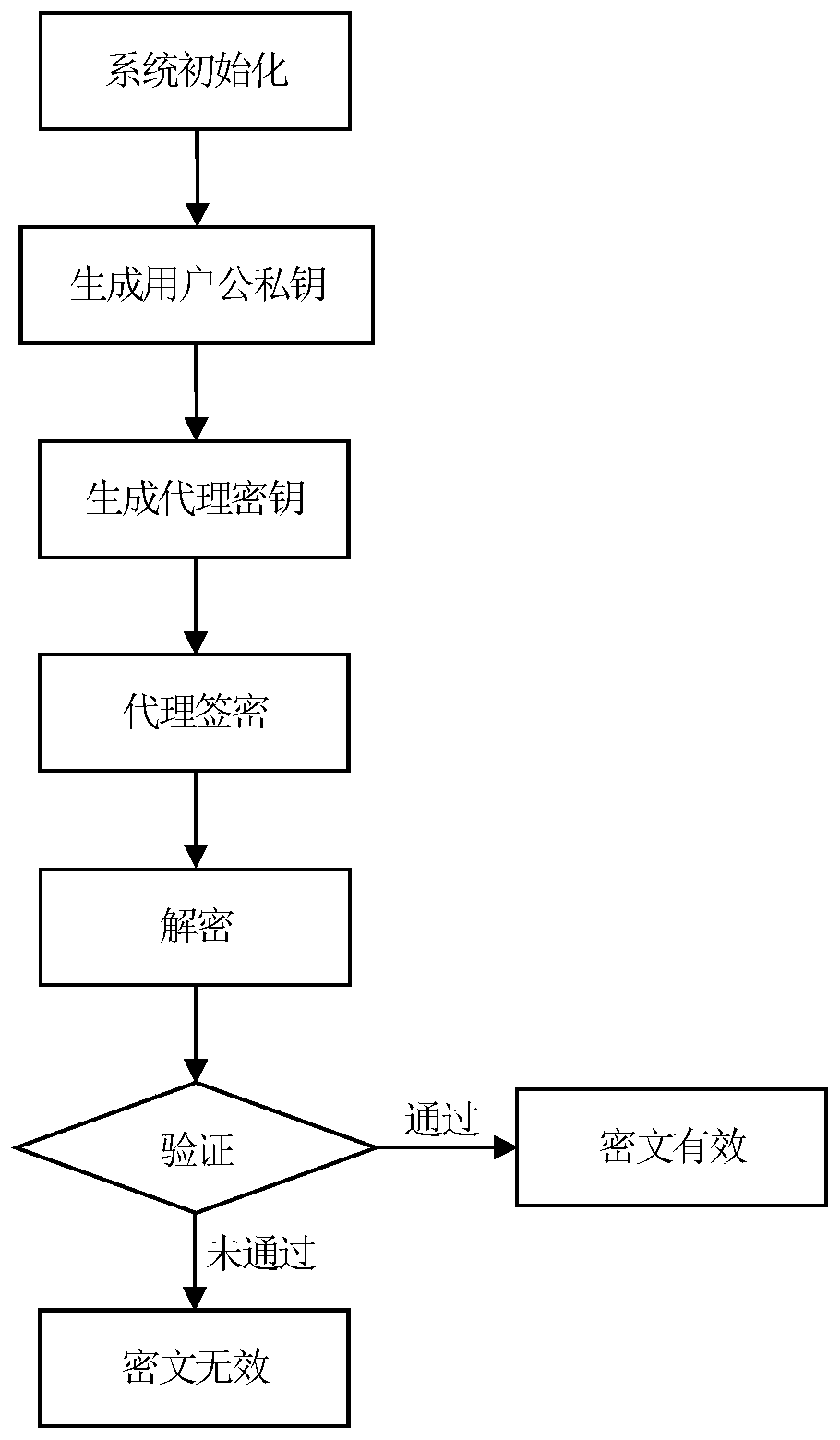
[0065] In this embodiment, the large prime number q is 2 192 -2 64 -1 as an example, the general and composite identity proxy signcryption method consists of the following steps:
[0066] A. System initialization
[0067] (A1) The order of the private key generator is selected as a large prime number q is 2 192 -2 64 A Cyclic Additive Group G of -1 1 and a cyclic multiplicative group G 2 , let P be the cyclic addition group G 1 A generator of , e is G 1 ×G 1 →G 2 A bilinear map of .
[0068] (A2) The private key generator selects a cryptographically secure Hash function h 1 、h 2 、h 3 、h 4 :h 1 is {0,1} * →G 1 , h 2 yes h 3 is {0,1} t ×G 1 ×G 2 →{0,1} l , h 4 yes in is {1,2,...,2 192 -2 64 -2}, is the length of the message, and t is the length of the authorization certificate.
[0069] (A3) The private key generator randomly selects the master key s∈Z q * And determine the system public key y:
[0070] y=sP.
[0071] (A4) The private key ge...
Embodiment 2
[0121] In this embodiment, the large prime number q is 2 224 -2 96 +1 as an example, the general and composable identity proxy signcryption method consists of the following steps:
[0122] A. System initialization
[0123] (A1) The order of the private key generator is selected as a large prime number q is 2 224 -2 96 A Cyclic Additive Group G of +1 1 and a cyclic multiplicative group G 2 , let P be the cyclic addition group G 1 A generator of , e is G 1 ×G 1 →G 2 A bilinear map of .
[0124] (A2) The private key generator selects a cryptographically secure Hash function h 1 、h 2 、h 3 、h 4 :h 1 is {0,1} * →G 1 , h 2 yes h 3 is {0,1} t ×G 1 ×G 2 →{0,1} l , h 4 yes in is {1,2,...,2 224 -2 96}, is the length of the message, and t is the length of the authorization certificate.
[0125] (A3) The private key generator randomly selects the master key s∈Z q * And determine the system public key y:
[0126] y=sP.
[0127] (A4) The private key gene...
Embodiment 3
[0131] In this embodiment, the large prime number q is 2 256 -2 224 +2 192 +2 96 +1 as an example, the general and composable identity proxy signcryption method consists of the following steps:
[0132] A. System initialization
[0133] (A1) The order of the private key generator is selected as a large prime number q is 2 256 -2 224 +2 192 +2 96 A cyclic addition group G of +1 1 and a cyclic multiplicative group G 2 , let P be the cyclic addition group G 1 A generator of , e is G 1 ×G 1 →G 2 A bilinear map of .
[0134] (A2) The private key generator selects a cryptographically secure Hash function h 1 、h 2 、h 3 、h 4 :h 1 is {0,1} * →G 1 , h 2 yes h 3 is {0,1} t ×G 1 ×G 2 →{0,1} l , h 4 yes in is {1,2,...,2 256 -2 224 +2 192 +2 96}, is the length of the message, and t is the length of the authorization certificate.
[0135] (A3) The private key generator randomly selects the master key s∈Z q * And determine the system public key y:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com