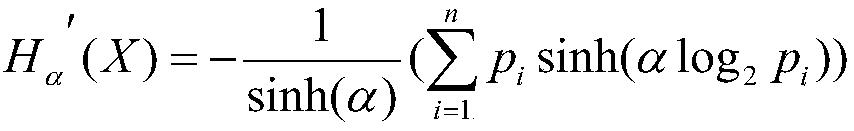DDoS attack and shanyong event detection method based on stream
A technology of event detection and event, applied in the field of computer security, can solve problems such as increased difficulty and achieve the effect of improving detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
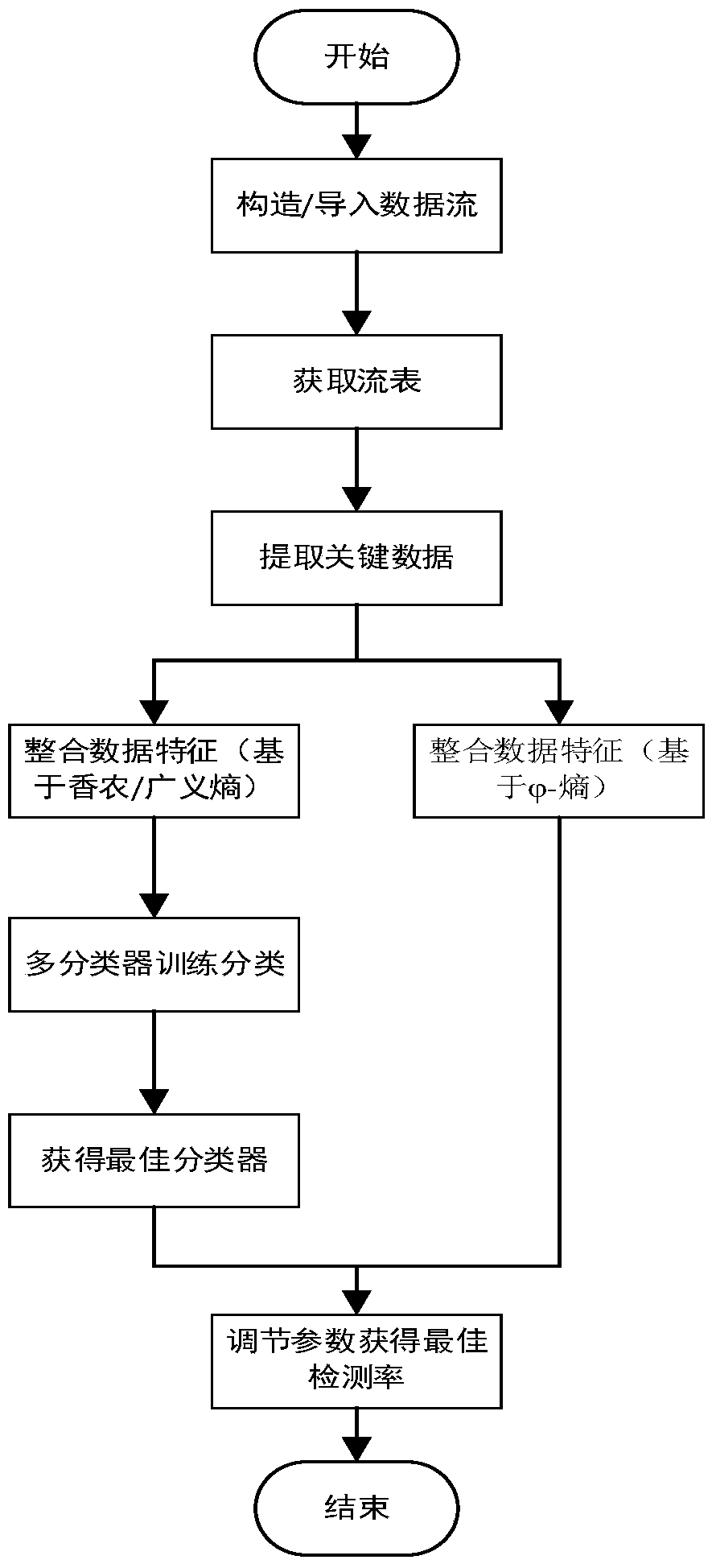
[0031] In order to demonstrate the purpose and advantages of the present invention more intuitively and clearly, the present invention will be described in detail below in conjunction with the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are part of the embodiments of the present invention, not all of them. . Based on the implementation manners in the present invention, all other implementation manners obtained by persons of ordinary skill in the art without creative efforts fall within the protection scope of the present invention.
[0032] refer to figure 1 , this embodiment proposes a flow-based DDoS attack and flash event detection method in SDN, the applied flow detection method combines Shannon entropy and generalized entropy improved Entropy and streaming multidimensional features, methods include:
[0033]First, build a topology on the Mininet platform, including SDN controllers, OpenFlow switches, source ho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com