Application programming interface security management method and system
A programming interface and application program technology, applied in the field of information security, can solve the problem of being unable to block illegal access to business data, and achieve the effects of preventing loopholes, ensuring controllability, and preventing malicious attacks on the interface
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
[0030] In the description of the present application, it should be understood that the term "plurality" means two or more, unless otherwise specifically defined. The terms "including", "comprising" and similar terms should be understood as open-ended terms, ie "including / comprising but not limited to". The term "based on" is "based at least in part on". The term "an embodiment" means "at least one embodiment"; the term "another embodiment" means "at least one further embodiment". Relevant definitions of other terms will be given in the description below.
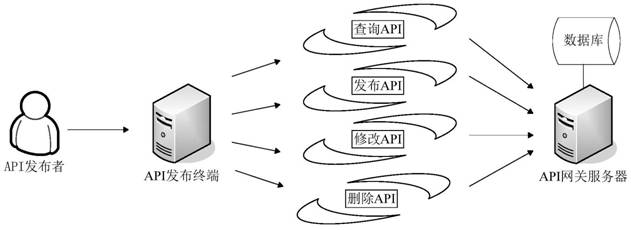
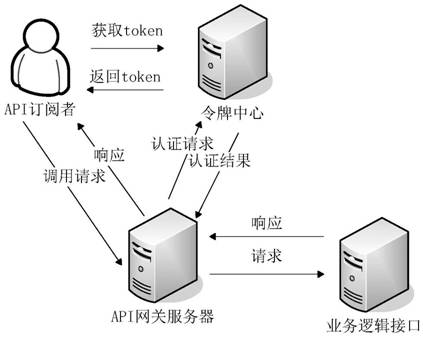
[0031] refer to figure 1, showing the flow of an embodiment of the application programming interface security management method of the present appl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com