Privacy protection method, terminal, and computer-readable storage medium
A privacy protection and computer technology, applied in the field of privacy protection, can solve the problems of leakage of user privacy information, low user experience, etc., to achieve the effect of protecting privacy and improving experience satisfaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
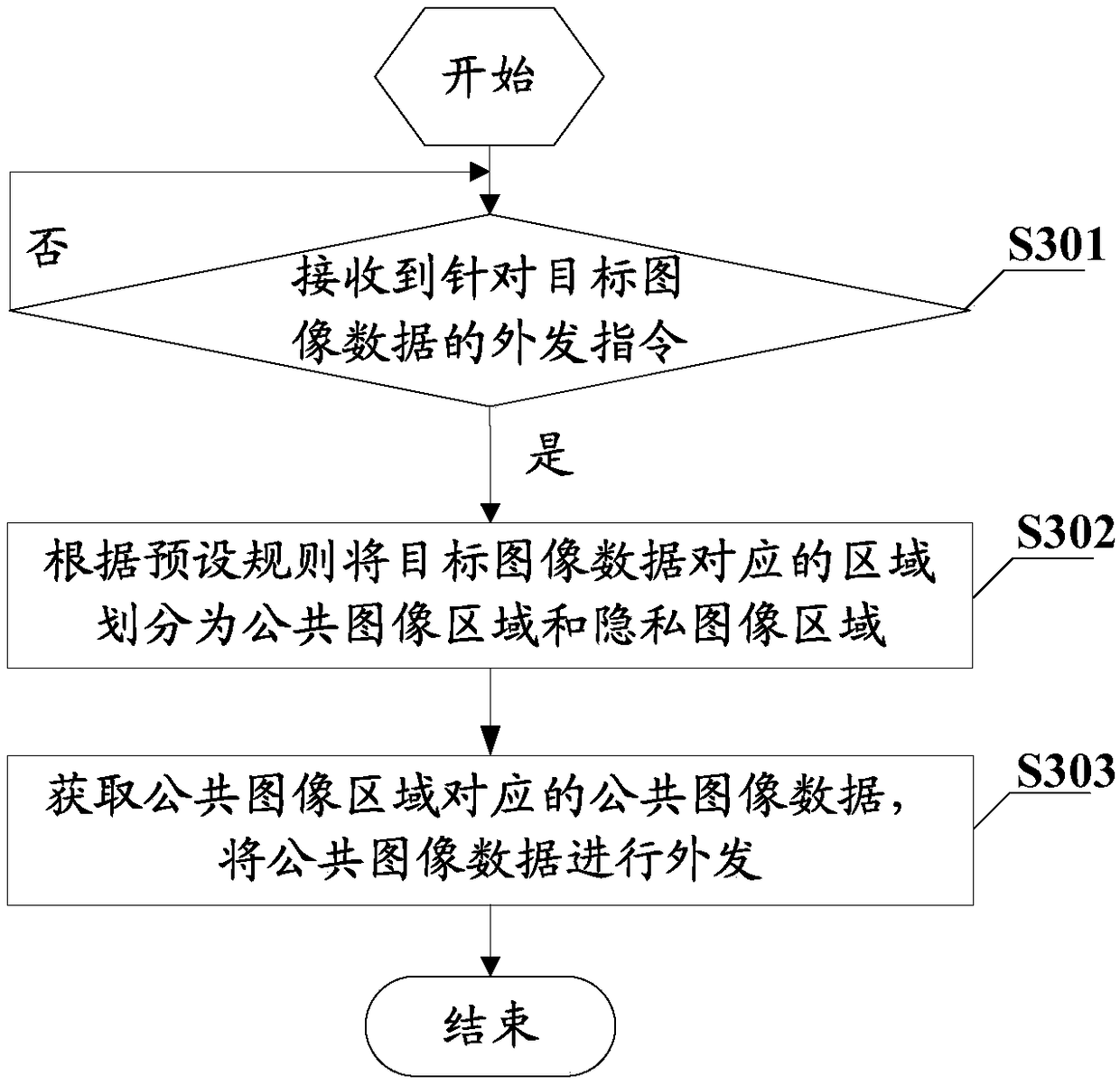
[0081] In order to solve the problem in the prior art that the user's private information is unintentionally leaked when the image is sent out, resulting in low user experience. This embodiment provides a privacy protection method. By judging whether an outgoing instruction for target image data is received, the method corresponds to the target image data according to preset rules when receiving an outgoing instruction for target image data. The area is divided into a public image area and a private image area, and then the public image data corresponding to the public image area is obtained, and the public image data is sent out. For details, please refer to image 3 as shown, image 3 The basic flowchart of the privacy protection method provided in this embodiment, the privacy protection method includes:
[0082] S301: judging whether an outgoing instruction for target image data is received;
[0083] If yes, execute S302; if not, continue to execute S301.
[0084] First...
no. 2 example
[0121] This embodiment is based on the first embodiment, taking a specific privacy protection method as an example to further illustrate the present invention. For details, see Figure 10 shown.
[0122] S1001: judging whether an outgoing instruction for target image data is received;
[0123] If yes, execute S1002; if not, continue to execute S1001.
[0124] Assuming that user A and user B have started video chatting, that is, user B is about to receive the target image data from user A at this time, that is, at this time, an outgoing instruction for the target image data has been received, and S1002 is executed.
[0125] S1002: Use image recognition technology to judge whether there is an image in the preset public image table in the target image data;
[0126] If yes, execute S1003; if not, continue to execute S1002.
[0127] Following the above example, further, assume that the image in the public image table set by user A is the image of user A himself, at this time, u...
no. 3 example
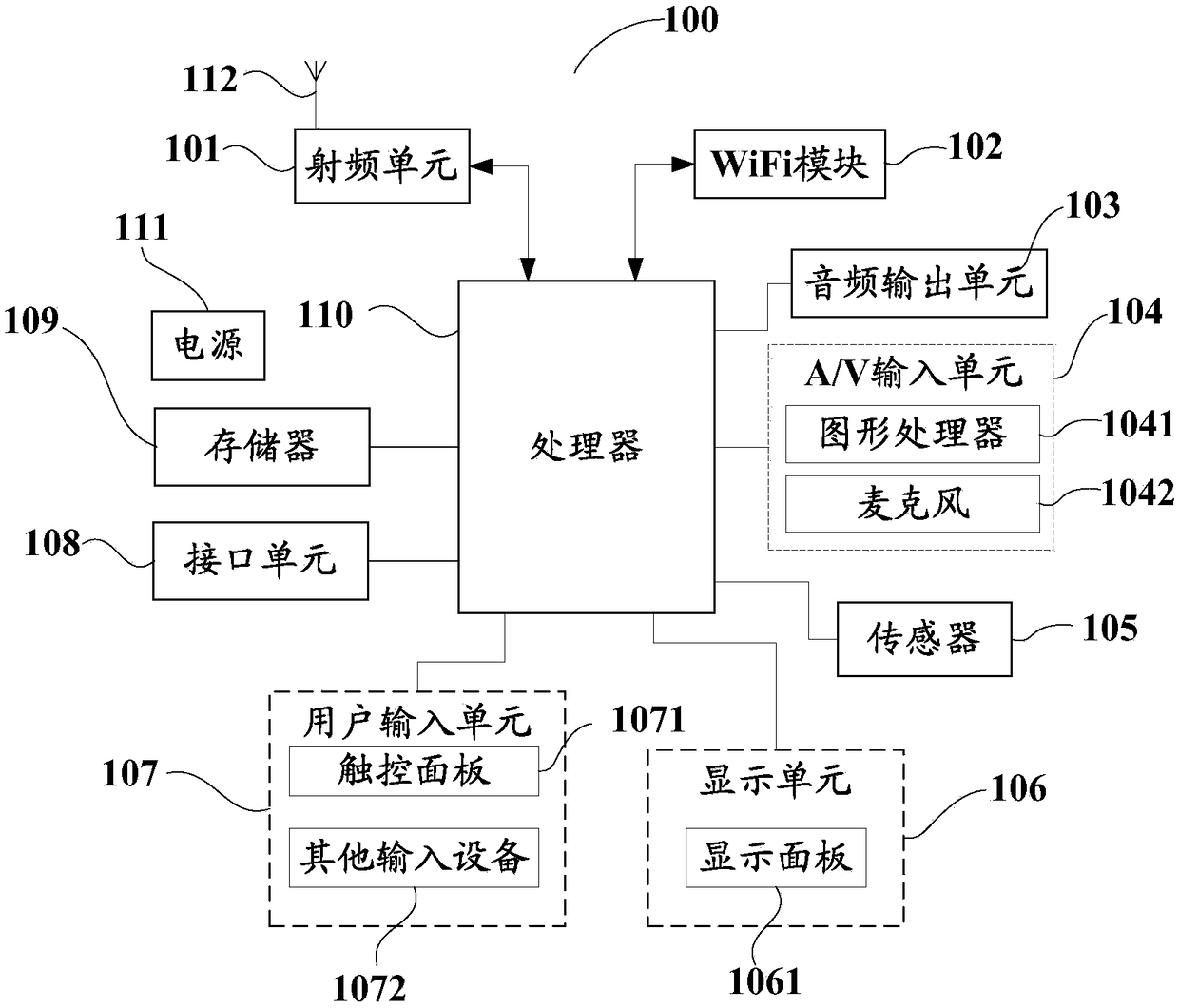
[0138] This embodiment provides a terminal, for details, refer to Figure 11 As shown, the terminal provided in this embodiment includes a processor 1101 , a memory 1102 and a communication bus 1103 .
[0139] Wherein, the communication bus 1103 in this embodiment is used to realize connection and communication between the processor 1101 and the memory 1102, and the processor 1101 is used to execute one or more programs stored in the memory 1102, so as to realize the following steps:
[0140] Judging whether an outgoing instruction for the target image data is received;
[0141] If so, divide the area corresponding to the target image data into a public image area and a private image area according to preset rules;
[0142] The public image data corresponding to the public image area is obtained, and the public image data is sent out.
[0143] It should be noted that the above steps implemented by the processor 1101 may be an independent application, that is, it is separate ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com