A data access method, access verification device and data storage system
A data storage system and data access technology, which is applied in the fields of data access methods, access verification equipment and data storage systems, can solve the problems of low data access efficiency, improve data access efficiency, and avoid low data access efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
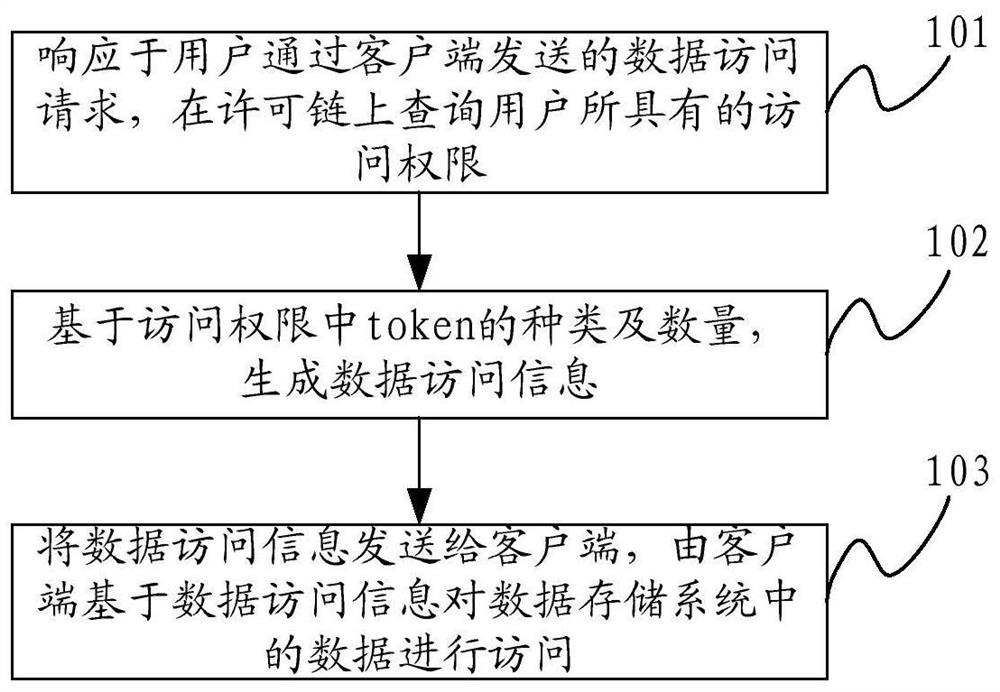
[0055] In order to realize data sharing, data is usually shared in a data storage system, and security is ensured by setting data access permissions. At present, the commonly used authority management scheme adopts the hierarchical authorization mechanism. The data sharing service between different entities needs to rely on the mutual authentication of the upper layer of the hierarchical authorization system, and then send it down to the level of the data requesting entity to complete the authorization. And because different levels of entities (user clients) correspond to different data permissions, different data have different visibility to different entities, resulting in the formation of massive mapping relationships between data and users (clients), and layer after layer requests. Issuing authorization leads to low data sharing efficiency, and it is difficult to flexibly support multi-level sharing authority management.
[0056] In order to solve the above problems, the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com