Fraud phone identification method, device and system
A technology of fraudulent calls and identification methods, applied in the information field, can solve problems such as economic losses, impact on social integrity, and psychological trauma of victims, and achieve the effect of reasonable diversion.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
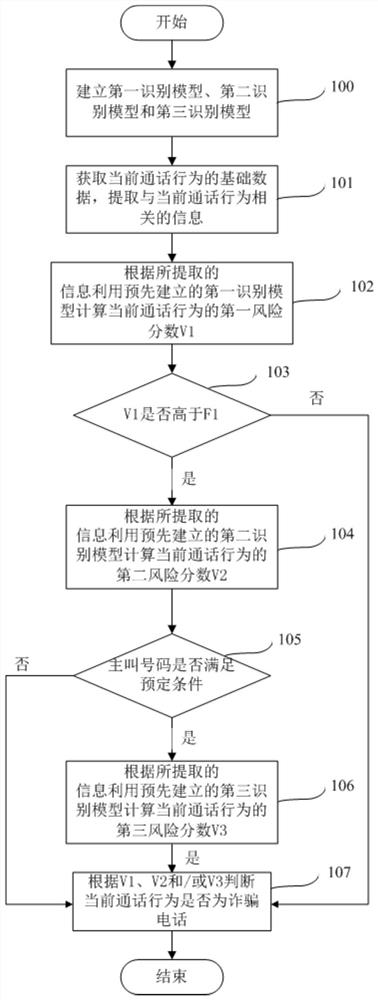
[0040]The embodiment of the present invention provides a fraud phone identification method, figure 1 is a schematic diagram of the method, please refer to figure 1 , the method includes:
[0041] Step 101: Obtain the basic data of the current call behavior, and extract information related to the current call behavior;
[0042] Step 102: Calculate the first risk score V1 of the current call behavior by using the pre-established first recognition model according to the extracted information;
[0043] Step 103: Judging whether the first risk score V1 is higher than the preset first threshold F1, if the judgment is yes, execute step 104, and if the judgment is no, execute step 107;
[0044] Step 104: Calculate the second risk score V2 of the current call behavior by using the pre-established second recognition model according to the extracted information;
[0045] Step 105: judging whether the calling party of the current call behavior satisfies the predetermined condition, if ...
Embodiment 2
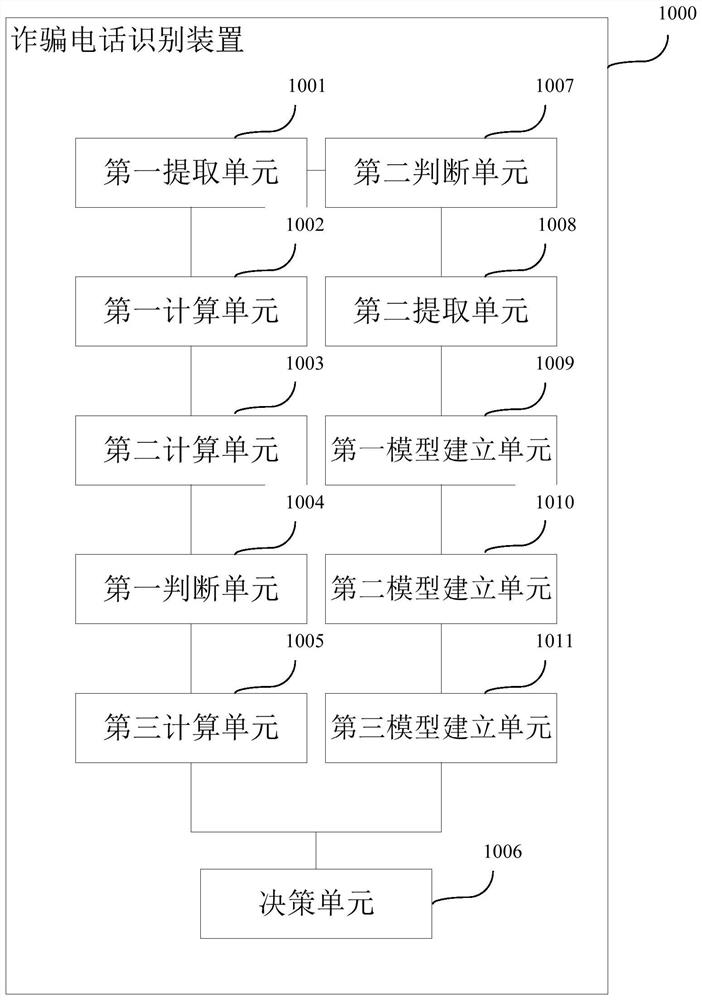
[0099] This embodiment provides a device for identifying fraudulent calls. The apparatus may be, for example, a piece of equipment in a service system of a telecom operator, or may be one or some components or components configured in the above-mentioned equipment. Since the problem-solving principle of the device is similar to that of the method in Embodiment 1, its specific implementation can refer to the embodiment of the method in Embodiment 1, and the same content will not be repeated.
[0100] figure 2 is a schematic diagram of the device 1000, as figure 2 As shown, the device includes a first extraction unit 1001, a first calculation unit 1002, a second calculation unit 1003, a first judgment unit 1004, a third calculation unit 1005, and a decision unit 1006, and the first extraction unit 1001 obtains the current call behavior Basic data, extracting information related to the current call behavior; the first calculation unit 1002 uses the pre-established first recog...
Embodiment 3
[0116] An embodiment of the present invention provides a system for identifying fraudulent calls, and the system for identifying fraudulent calls may include the device for identifying fraudulent calls described in Embodiment 2. Since the device for identifying fraudulent calls has been described in detail in Embodiment 2, its content is incorporated here, and will not be repeated here.
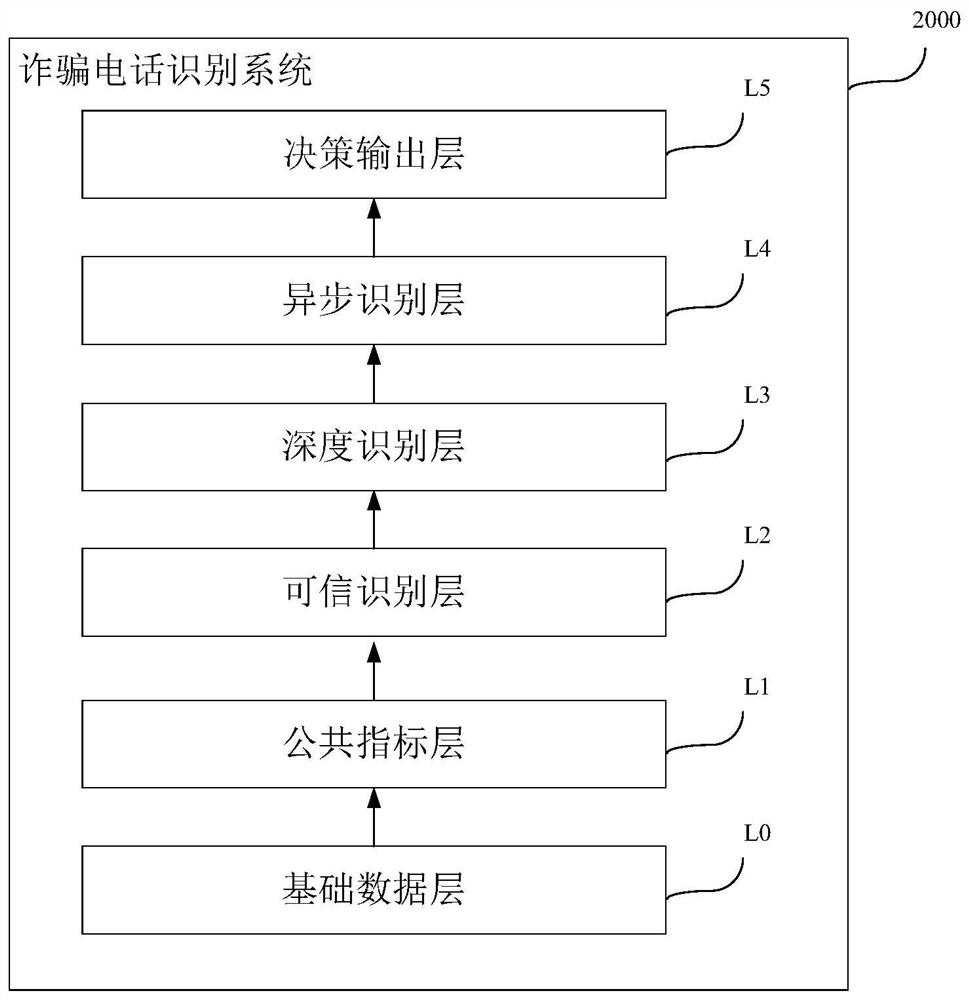
[0117] image 3 is a schematic diagram of the data architecture of the fraud phone identification system of this embodiment, as image 3 As shown, the fraud phone identification system has six layers, namely the basic data layer L0, the public index layer L1, the trusted identification layer L2, the deep identification layer L3, the asynchronous identification layer L4 and the decision output layer L5.
[0118] The basic data layer L0 is mainly used to collect and store call records and all information related to call records;
[0119] The public indicator layer L1 is mainly used to extract...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com