Wireless router protection method and system based on cloud shadow system
A wireless router and cloud server technology, applied in the transmission system, digital transmission system, electrical components, etc., can solve the problems of slow action of equipment manufacturers, low security awareness of wireless router users, and difficult security issues of wireless routers, etc., to achieve convenient promotion Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to enable relevant persons in the technical field to better understand the technical solution of the present invention, and to make the purpose, features and points of the present invention more obvious and easy to understand, the core technology of the present invention will be described below in conjunction with the accompanying drawings and examples Further clarification.
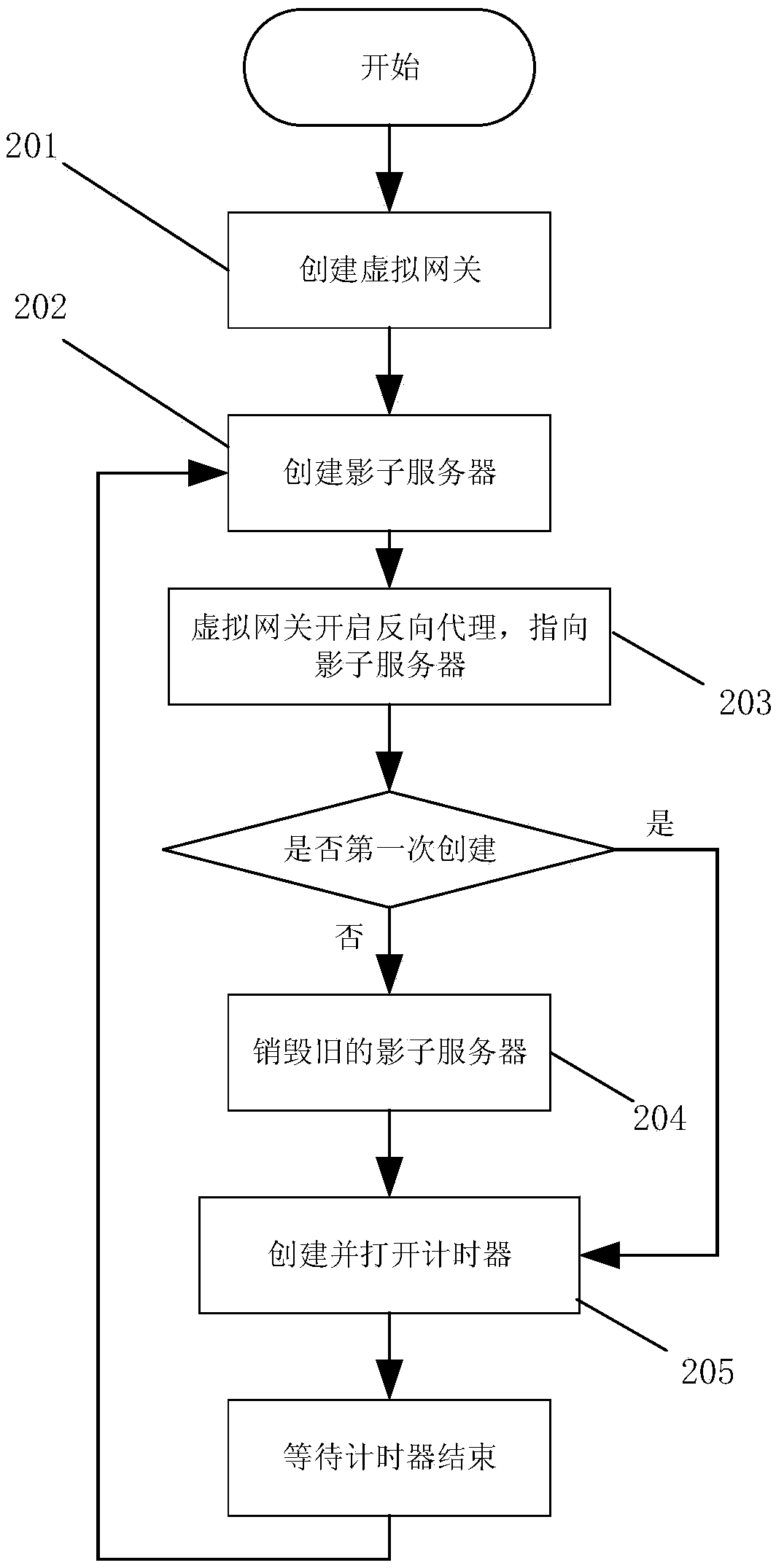
[0032] Core content of the present invention mainly comprises:
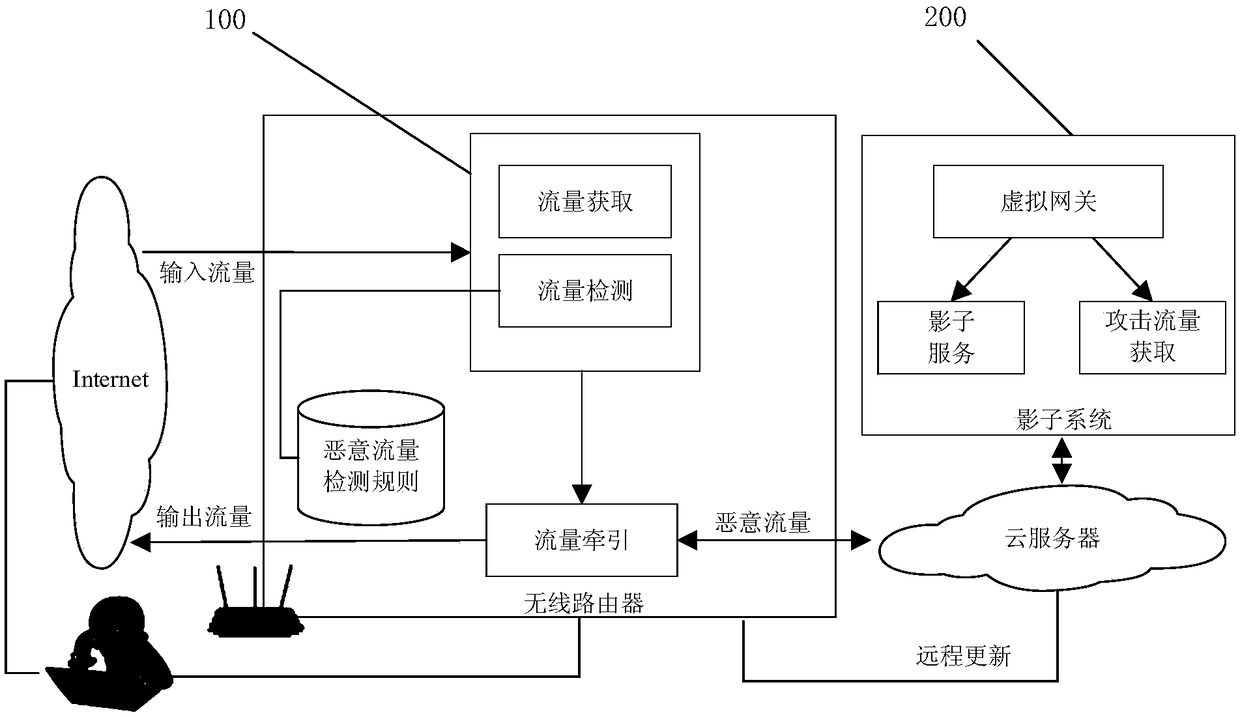
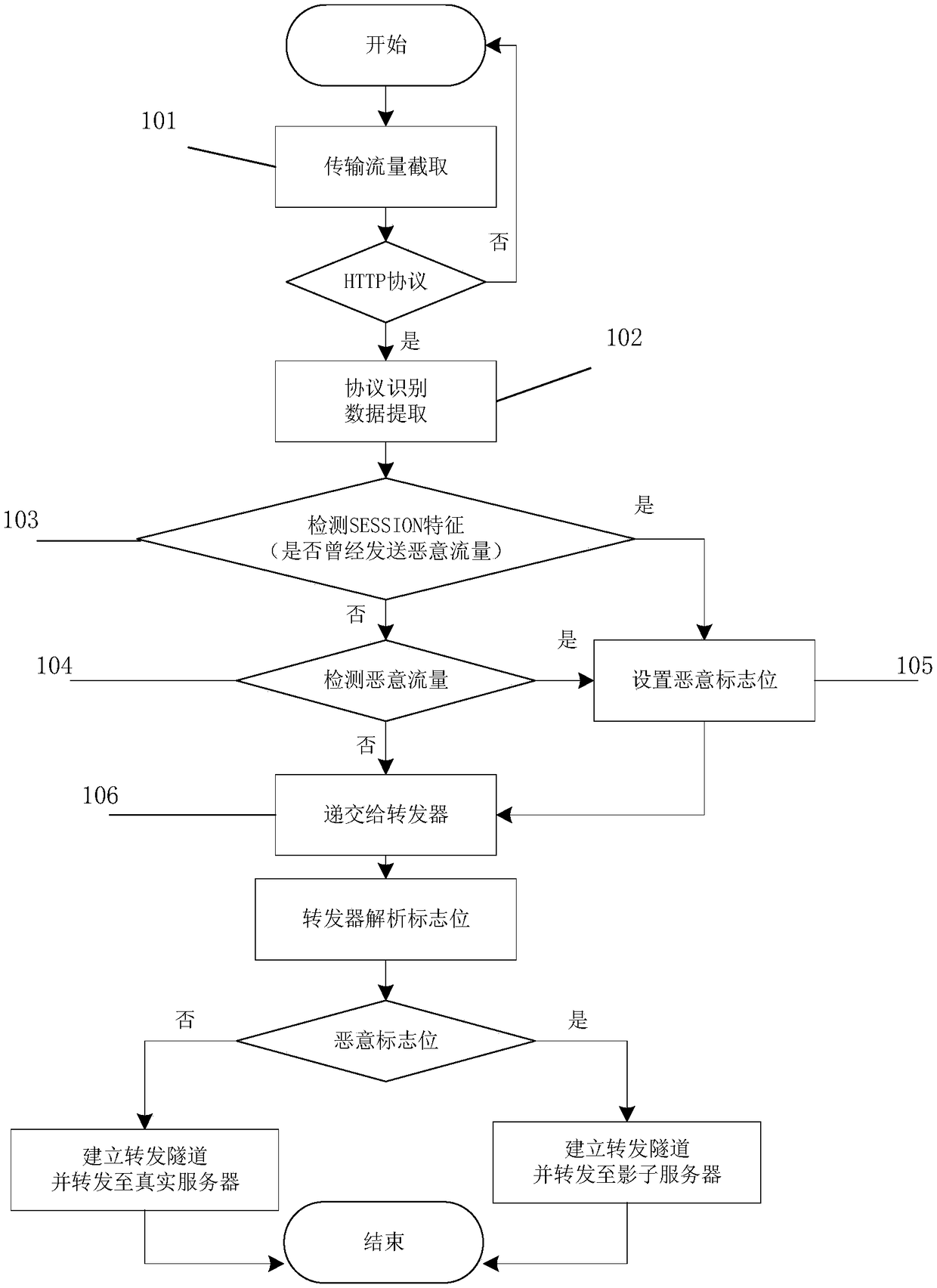
[0033] 1. Traffic data packet acquisition. Traffic data packet acquisition is the most basic function point in the wireless router protection system. For the data packets flowing through the router, it is obtained through the middleman technology, and analyzed, classified according to the destination address, and the data packets whose destination address is not the router are released. .
[0034] 2. Packet detection. Packet detection is a key part of the wireless router protection system. It uses the regularly updated ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com