A digital identity authentication method and system based on a secure two-dimensional code
A technology of identity authentication and digital identity, applied in transmission systems, electrical components, etc., to ensure login security and prevent data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
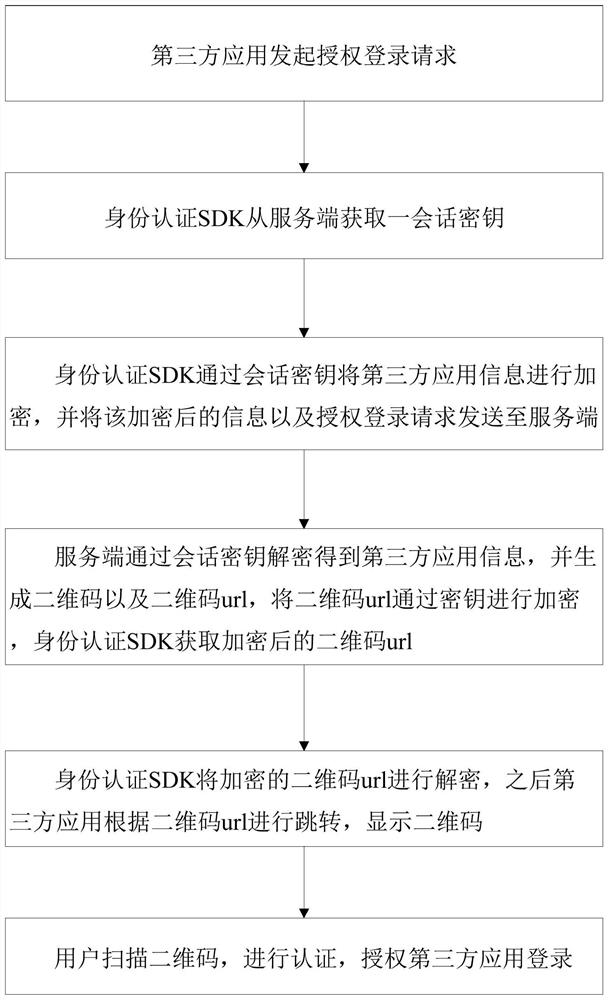
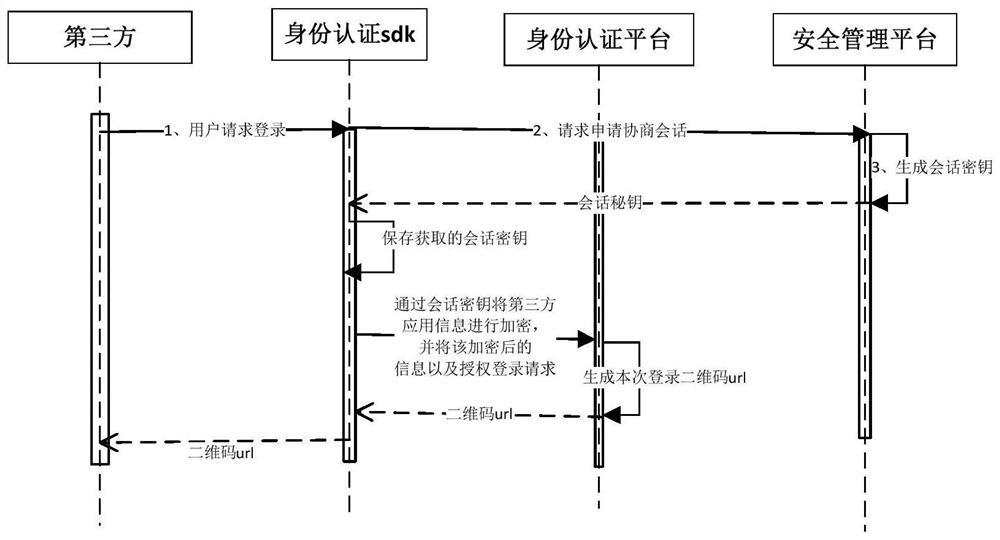
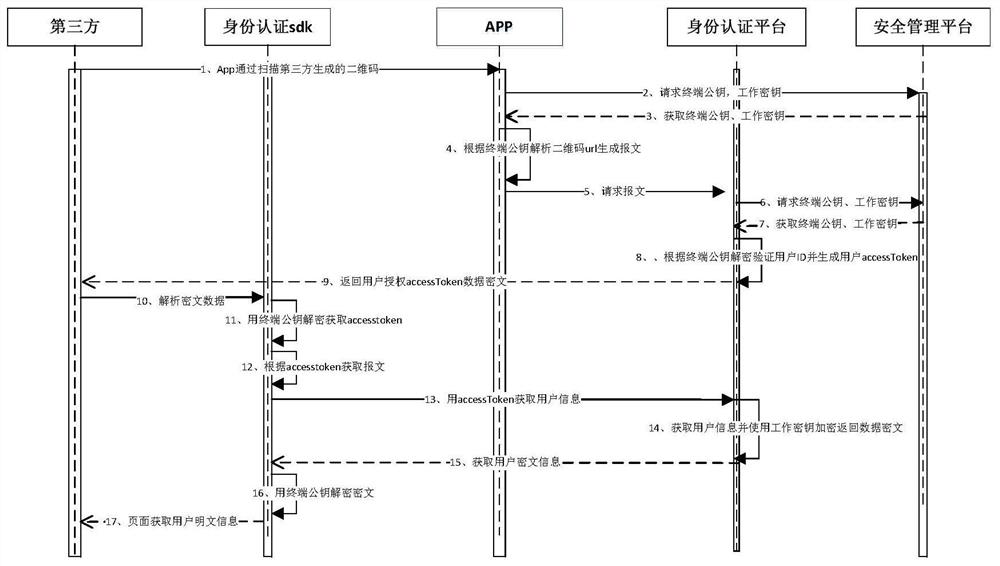
[0026] Such as figure 1 , figure 2 with image 3 As shown, the authentication method of the digital identity based on the security two-dimensional code of the present invention includes:
[0027] Step 1. The third-party application initiates an authorization login request;
[0028] Step 2. The identity authentication SDK obtains a session key from the server;
[0029] Step 3. The identity authentication SDK encrypts the third-party application information through the session key, and sends the encrypted information and the authorized login request to the server;
[0030] Step 4. The server decrypts the third-party application information through the session key, generates a QR code and a QR code url, encrypts the QR code url with the session key, and the identity authentication SDK obtains the encrypted QR code url ;
[0031] Step 5. The identity authentication SDK decrypts the encrypted QR code url, and then the third-party application jumps according to the QR code url...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com