Unified user malicious behavior detecting method and system in social network
A technology of social network and detection method, applied in the direction of data exchange network, transmission system, digital transmission system, etc., can solve the problems of difficult accuracy, unsatisfactory detection effect, and relatively difficult combination, and achieve high detection accuracy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The specific embodiment of the present invention will be further described below in conjunction with accompanying drawing:
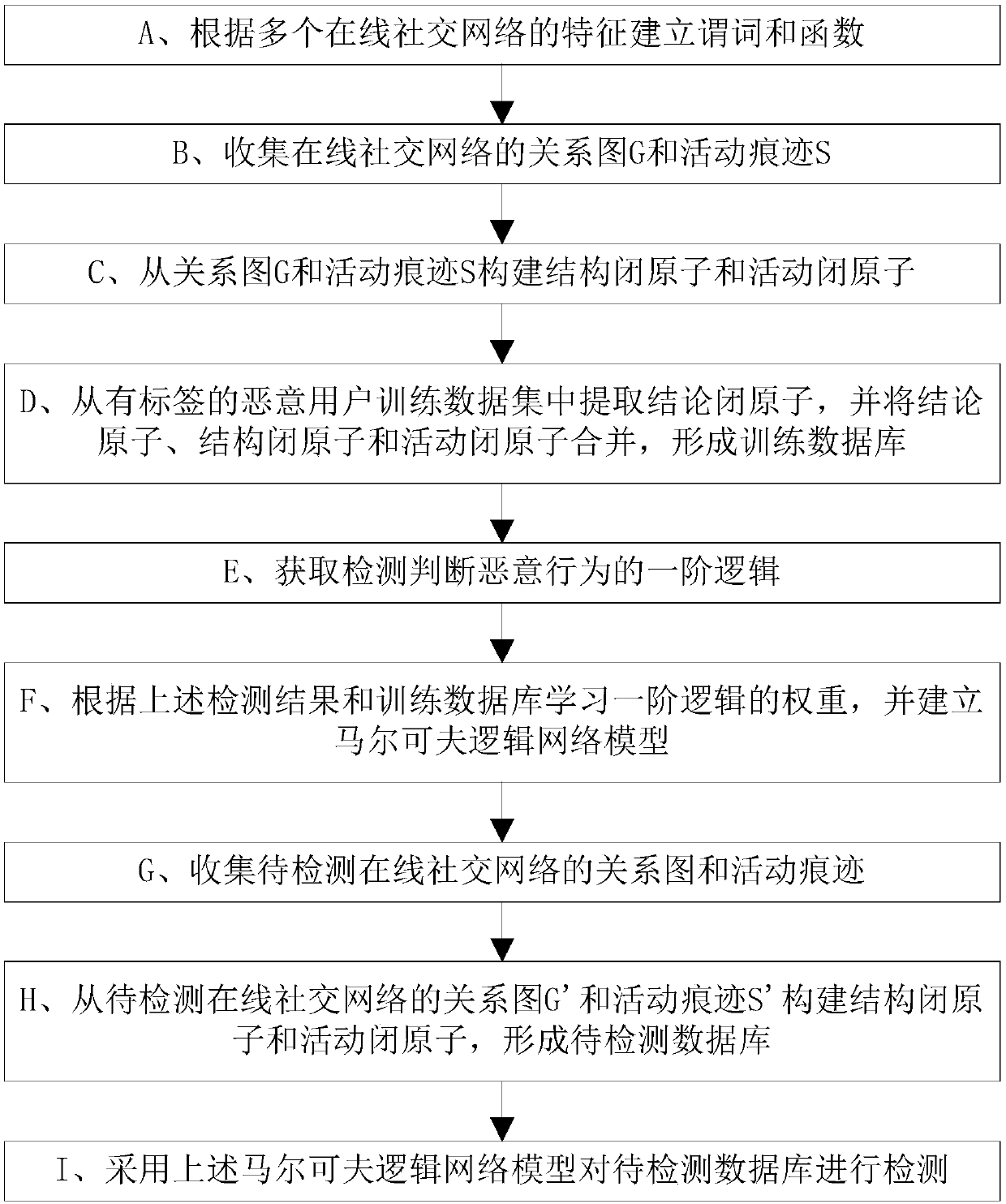
[0028] refer to figure 1 , a unified user malicious behavior detection method in a social network, comprising the following steps:
[0029] A. Establish predicates and functions according to the characteristics of multiple online social networks;
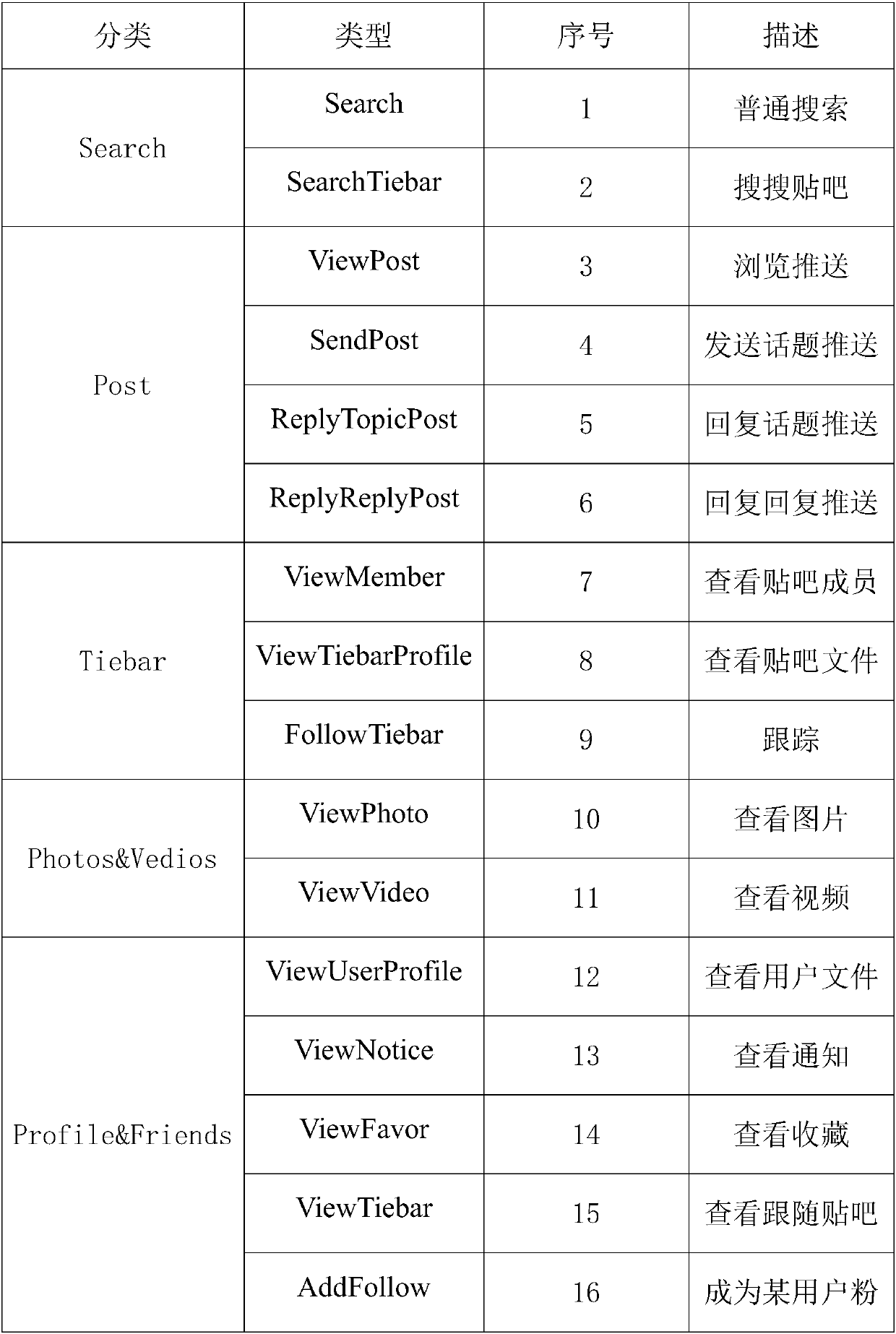
[0030] Given an online social network (Online Social Networks, OSN) relationship graph G and activity traces S, including the following definitions:
[0031] (1) Rule: Malicious behavior detection rules are expressed as , where F is a first-order logic formula including constants, variables, predicates, and functions, and w is the value weight of F.
[0032] (2) Constant (Constant): all users User={u appearing in the relationship graph G and activity trace S 1 ,u 2 ,...,u k}, objects such as blog posts, topics, etc., non-negative integer time.
[0033] (3) Function (Function): The function realize...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com